A new ransomware has been spotted called 7ev3n that encrypts your data and demands 13 bitcoins to decrypt your files. A 13 bitcoin ransom demand is the largest we have seen to date for this type of infection, but that is only just one of the problems with this ransomware. In addition to the large ransom demand, the 7ev3n Ransomware also does a great job trashing the Windows system that it was installed on. It does this by modifying a variety of system settings and boot options so that keyboard keys and system recovery options are disabled on the computer. So between a victim’s files being encrypted and the computer being trashed so you can’t bypass the lock screen, it makes for a very frustrating experience.
The 7ev3n Encryption Process
At this time, the 7ev3n ransomware does not currently appear to be wide spread and we only have one report of an infected user on our forums. When a computer is infected, the ransomware will scan all of the drive letters that match certain file extensions and when it finds a match rename them into numbered sequences of .files with the .R5A extension. For example, if a folder contains 25 data files, the ransomware will encrypt and rename all the files to 1.R5A, 2.R5A, 3.R5A … 25.R5A. The files currently targeted by this the 7ev3n ransomware are:
dbf, arw, txt, doc, docm, docx, zip, rar, xlsx, xlsb, xlsm, pdf, jpg, jpe, jpeg, sql, mdf, accdb, mdb, odb, odm, odp, ods
When the ransom has finished encrypting your data it will display a ransom note that demands 13 bitcoins and displays the bitcoin address you must send the ransom to. The ransom note that is displayed can be seen below.
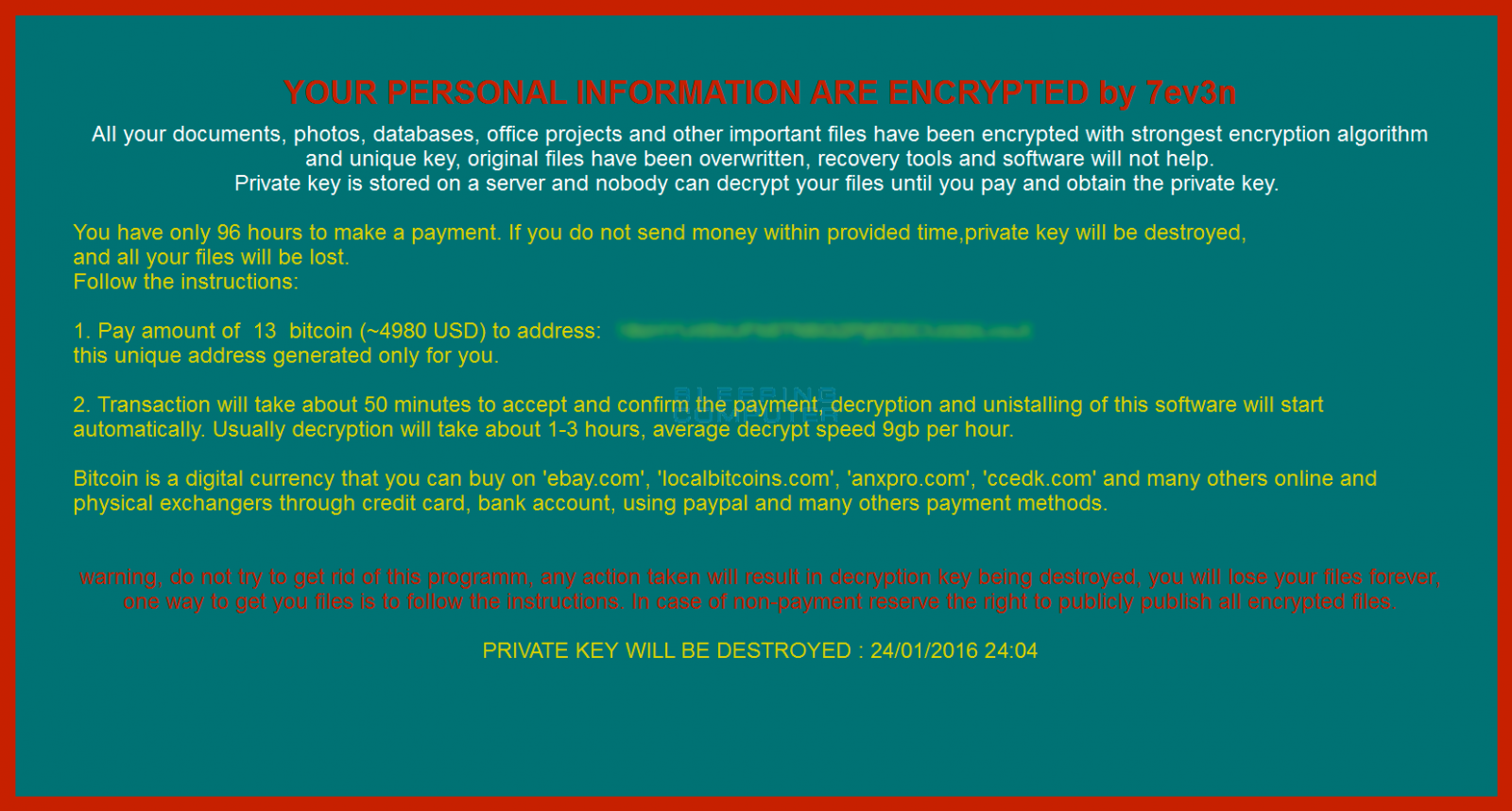
Trashing the infected computer
When the ransomware is installed it will also install numerous files in the %LocalAppData% folder. These files are:
- %LocalAppData%\bcd.bat – A batch file consisting of numerous BCDEDIT commands that disable various bootup recovery options.
- %LocalAppData%\del.bat – This batch file will delete the installer for the ransomware.
- %LocalAppData%\system.exe – This is the main executable for the ransomware, which encrypts your data and displays the ransom note.
- %LocalAppData%\time.e – This file contains the timestamp of when the infection started.
- %LocalAppData%\uac.exe – This executable allows various components of the ransomware to run with elevated rights without displaying a UAC prompt.
The bcd.bat files contains BCDEDIT commands that disable a variety of recovery options in Windows. The recovery options that are disabled include the Windows Emergency Management System, the Advanced Options startup menu, the Boot Options Editor, the Windows Error Recovery menu when Windows can’t start, and Startup Repair. The contents of this batch are listed below:
bcdedit /set {current} bootems no
bcdedit /set {current} advancedoptions off
bcdedit /set {current} optionsedit off
bcdedit /set {current} bootstatuspolicy IgnoreAllFailures
bcdedit /set {current} recoveryenabled off
del %0
Now that 7ev3n has effectively locked you out of any recovery options, it will also add a registry entry that disables keys commonly used to troubleshoot Windows such as Alt+Tab, Task Manager and the Run dialog, It does this by adding a specifial registry value that disables the F1, F10, F3, F4, Enter, Escape, Left Alt, Left Ctrl, Left Windows, Num Lock, Right Alt, Right Ctrl, Right Shift, Right Windows, and Tab keys. This registry value is shown below.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layout" "Scancode Map" = "00000000 00000000 17000000 00003800 000038e0 00005be0 00005ce0 00003600 00001d00 00001de000000f000000010000001c0000003e0000003b00000044000000450000003d0000005de000000000"
Finally, to make your life harder than it already is, it creates a Windows task that executes the above commands every time you login.
Removing the 7ev3n Ransomware
Unfortunately, at this time there is no way to decrypt files for free, but to make matters worse making the system usable again is a royal pain as well. The methods described below are advanced, so if you need help feel free to ask in our forums or seek a professional to perform these steps for you.
The best method to reset the damage is to use a Windows installation disc to bootup your computer and enter repair mode. Once in repair mode you should a list of recovery tools.
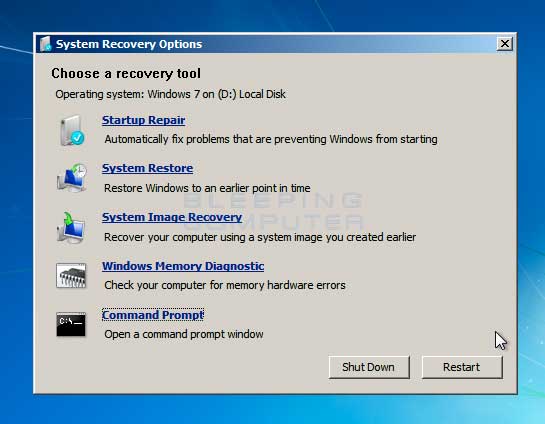
Click on the Command Prompt option to open the Recovery Command Prompt and enter the following BCDEDIT commands to enable recovery options again.
bcdedit /set {default} bootems yes
bcdedit /set {default} advancedoptions on
bcdedit /set {default} recoveryenabled on
bcdedit /set {default} bootstatuspolicy DisplayAllFailures
These commands should be entered by typing them directly into the command prompt as displayed below:

Once you have fixed the repair mode, you need to type exit and reboot into Safe Mode with Command Prompt. Once in the Command Promp you want to perform the following tasks:
Delete the Following files:
%LocalAppData%\bcd.bat
C:\Windows\System32\Tasks\uac
Rename the Following files:
%LocalAppData%\system.exe
C:\Windows\System32\Tasks\uac
Remove the following Registry values with Regedit:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layout" "Scancode Map" Once you have completed all of these steps, you can reboot your computer into Normal Mode and run your favorite antivirus or antimalware program to clean up the rest of the datmage.
Files added by the 7ev3n Ransomware:
%LocalAppData%\bcd.bat
%LocalAppData%\del.bat
%LocalAppData%\system.exe
%LocalAppData%\time.e
%LocalAppData%\uac.exe
C:\Windows\System32\Tasks\uac
C:\Windows\System32\elsext.dll
Registry Keys added by the 7ev3n Ransomware:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{62EC9C46-634C-4957-8A5C-4566462D0CE6}
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\uac
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell = "C:\Users\[login_name]\AppData\Local\system.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion" /v "crypted"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layout" "Scancode Map" = "00000000 00000000 17000000 00003800 000038e0 00005be0 00005ce0 00003600 00001d00 00001de000000f000000010000001c0000003e0000003b00000044000000450000003d0000005de000000000"
HKEY_CURRENT_USER\Control Panel\Accessibility\StickyKeys "Flags" = 506
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" "System"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion" "rgd_bcd_condition" = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" "EnableLUA" = 0
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











