Twenty years ago, the first Word macro malware spread across the planet.
Embedded inside a Word document, and rather unhelpfully given a kick start by being shipped on a Microsoft CD ROM, the Concept virus proved that people were much more willing to open unsolicited .DOC files than something more obviously suspicious like an .EXE attachment.
It would be great to think that after two decades of fighting malware in Word documents, users would have learnt to be more cautious or – heaven forbid – Microsoft might have rethought the wisdom of embedding a macro programming language inside the Word document format.
But macro malware hasn’t gone away, as today’s example shows.
Someone is spamming out malicious emails, pretending that they come from your photocopier.
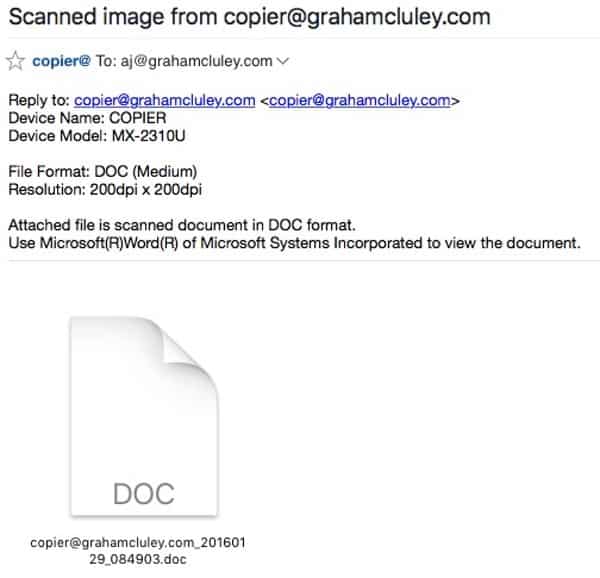
The emails which appear to come from copier@example.com (where example.com is your email’s domain name), claim to be a scanned image from your printer.
In the case of the malicious email I received, the message pretends to be from a Sharp multi-functional printer called the MX-2310U.
Like many modern office printers these days, the MX-2310U doesn’t just limit itself to printing. It can also fax, photocopy and scan.
I, of course, don’t own a Sharp MX-2310U, and it definitely isn’t attached to my network. So there was no way I was going to open the unsolicited .DOC file I had been sent.
Which is just as well, because if I had launched the attachment then Microsoft Word would have prompted me to enable macros.
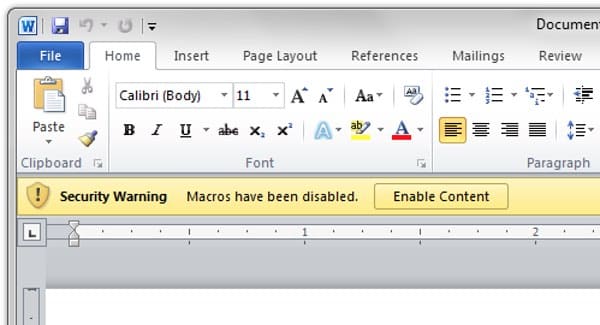
And if I had fallen for that, the malicious macro code would have attempted to download a banking Trojan horse onto my computer. Conrad Longmore on the Dynamoo blog reports that the criminals behind this campaign are using it to infect Windows PCs with a version of the Dridex malware.
Source:https://www.grahamcluley.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











