The fix? No patch, just destroy all extensions. Black Hat Asia The most popular Firefox extensions with millions of active users are open to attacks that can quietly compromise machines and pass Mozilla’s automated and human security tests.
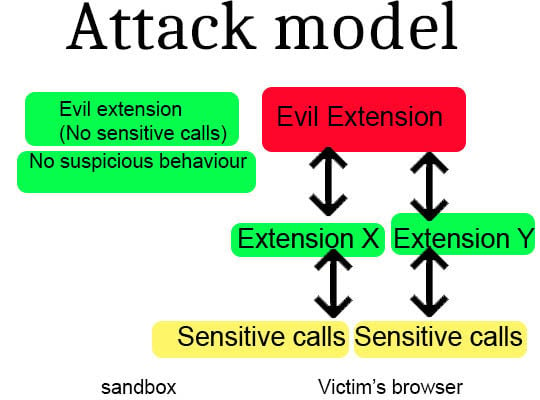
The extension reuse attacks exploit weaknesses in the structure of Firefox extensions such that malicious activity can be hidden behind legitimate functionality.
 Professor William Robertson (left) AND PhD Ahmet Buyukkayhan
Professor William Robertson (left) AND PhD Ahmet Buyukkayhan
For example, attackers could duplicate a popular but vulnerable extension to reuse attacks and write their own machine-pwning functionalities.
The researchers explained that extensions run with elevated privileges and access to information, so a malicious extension could steal private browsing data, passwords, and sensitive system resources.
The extensions vulnerable to the 255 reuse exploits found included NoScript with 2.5 million users, Video DownloadHelper with 6.5 million users, and GreaseMonkey with 1.5 million users. Adblock Plus with its 22 million users was unaffected.
Extension-reuse extensions permitted code execution vulnerabilities, event listener registration, and network access among other opportunities for attackers.
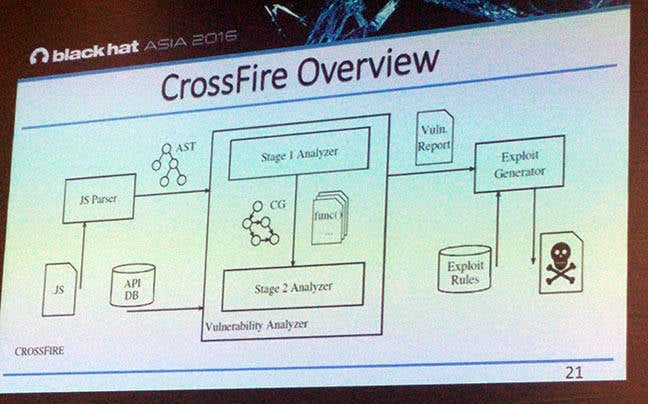
Boston University PhD Ahmet Buyukkayhan and Northeastern University Professor William Robertson presented the attacks at the Black Hat Asia hacking event in Singapore, releasing a framework dubbed Crossfire they used to identify extensions open to extension reuse vulnerabilities.
“We a have a lot of trust placed in browser vendors … but if you think about it, really squint your eyes, the extension framework really is a backdoor for potentially untrusted third parties to run code in a highly-privileged context,” Robertson says.
“We really shouldn’t have trust in the extension authors.
“The combination of automated analysis, manual review, and extension-signing – the vetting model that underpins all of Firefox’s extension security – if something goes wrong, then all bets are off.”
And things did go wrong. The pair were able to upload a malicious, but ultimately harmless proof-of-concept, extension to the Firefox extension shop even passing a requested more intensive ‘fully reviewed’ analysis. The extension dubbed ValidateThisWebsite contained 50 lines of code and no obfuscation.
“The more power vulnerable extensions have, the easier it is for an evil extension to work,” Buyukkayhan says.
“The full review is the highest level of security Mozilla has.”
The proof-of-concept feat was done with Crossfire which also sports a template function that make extension-reuse exploit development much faster.
That framework was supplied to Mozilla as part of a thorough research briefing at the end of which Firefox security wonks have committed to extra vigilance in extension review.
The disclosure of the new attack vectors, the product of an impressive two years’ research, come five months ahead of Mozilla’s pivot to model its extensions off the more secure Google Chrome model. Developers will still have 18 months from August to migrate to the WebExtensions hardened isolated model before the vulnerable legacy apps are nuked.
Mozilla already maintains a list of malicious extensions which sports 161 blacklisted items, a number that is likely to grow if attackers exploit the new extension-reuse model.
Source:https://www.theregister.co.uk/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











