The Check Point Mobile Threat Prevention team has long stressed how dangerous it can be to get apps from places other than the Apple App Store and Google Play Even with well-known third-party app stores the problem of security has become more obvious than ever.
A great example of this is Qihoo 360, a Chinese company known for its anti-virus software and mobile apps store and that unintentionally whitelisted malwareas part of a complex cyberattack.
A complex attack straight out of a spy novel
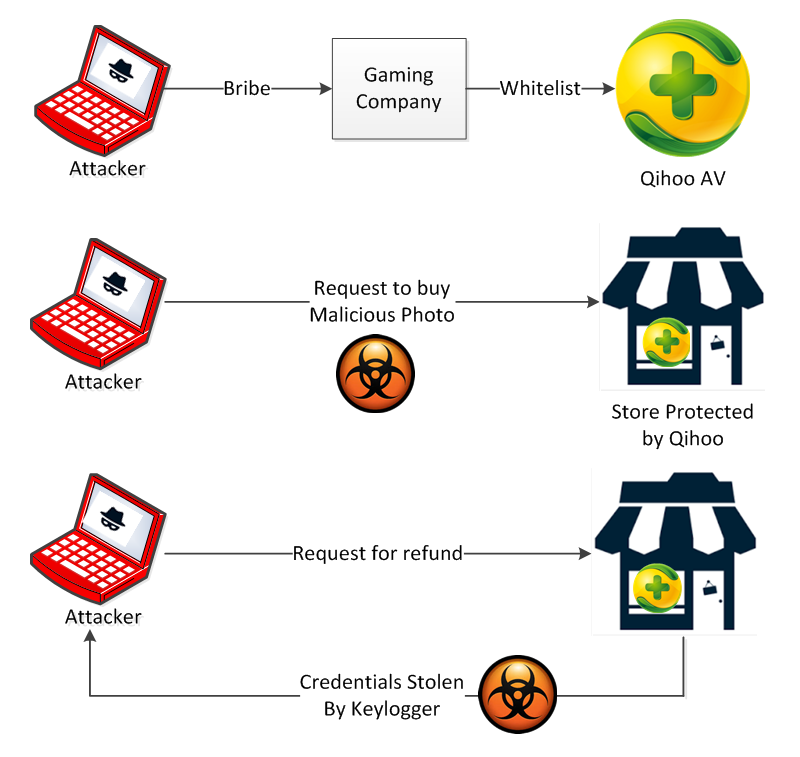
The attack itself was quite extensive. Cyber criminals bribed employees of a Chinese gaming company into including their malware among the legitimate apps it sent to Qihoo 360.
These apps passed Qihoo’s inspection and were whitelisted, allowing them and the contraband malware to run on machines protected by the wide-spread and free anti-virus solution offered by Qihoo for mobile and PC. Once this phase was complete, the attackers could initiate their true malicious activity.
Attackers would disguise themselves as customers of the popular Chinese marketplace website Taobao.com. Taobao.com is a marketplace similar to eBay, but operates much differently.
Customers browse buyer listings of products and, when they find something they want to buy, they initiate the purchase by sending a picture of that item back to the buyer using Aliwanwang, an instant messaging app. Money is then exchanged using Alipay, Aliwanwang’s payment platform.
An attacker, disguised as a Taobao.com customer, would take a seller’s legitimate photo and inject it with a whitelisted Trojan. The seller would open the picture on a PC and become infected because the Trojan would not be detected by Qihoo anti-virus.
The attacker would then request a refund from the seller, requiring the seller to log in to their Alipay account. The Trojan would then keylog their credentials, allowing the attacker to steal money from the seller’s account.
Why is this important to mobile security?
There are two major points in this attack which are worth further discussion:
First is how even primitive malware can managed to infiltrate a “secure” network. Even known malware has a way of inflicting damage. And because simple AVs use known malware signatures, they cannot be relied upon as a sole protection against malware.
Many AVs use a whitelist approach to avoid false positive detection, but the way these whitelists are generated and, like as we saw in the Qihoo 360 case, they can be compromised.
The second and more interesting point are the different methods third-party app stores use to protect users. The Qihoo incident is similar in a way since Qihoo’s whitelisting review was easily bypassed, leaving Qihoo AV users exposed to attacks. So app stores that you might believe to be safe may, in fact, really not be as safe as you’d think.
This subject was recently explored in length by one of our colleges, Avi Bashan, in a Dark Reading Article. In his analysis, Bashan demonstrates how malware manages to repeatedly infiltrate the Apple App Store and Google Play, and explains why the defenses of these stores remain deficient.
We already know that the mobile threat landscape often mirrors that of the PC world. So if malware can be installed on machines protected by Qihoo and can infiltrate into its own app store, this example illustrates how important it is to avoid third-party stores and to instead at least rely on stores with more reliable security.
But even still, stores like the App Store and Goolge Play aren’t immune to threats. It’s only a matter of time before attackers turn their full attention to infiltrating the app stores users trust most.
Source:https://blog.checkpoint.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











