Yesterday, a new ransomware called TrueCrypter was discovered by AVG malware analyst Jakub Kroustek. This ransomware encrypts your data using AES-256 encryption and then demands either .2 bitcoins or $115 USD in Amazon gift cards. When encrypting your data, TrueCrypter will append the .enc extension to all encrypted files. It is unsure if the sample that we looked at is a hoax, a test ransomware, or just a buggy program as it will automatically decrypt your files by simply clicking on the Pay button.
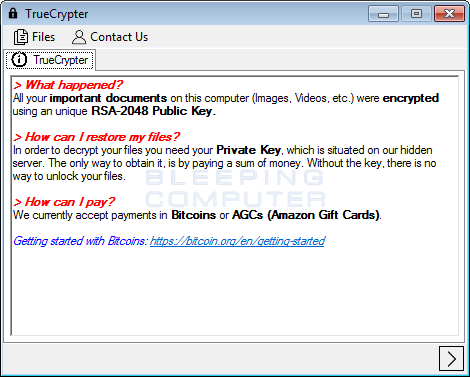
It is easy to remove TrueCrypter and Decrypt your Files
As already stated, the TrueCrypter program will encrypt your data files when it is installed. On the other hand, simply clicking on the pay button will cause it to decrypt these files and then remove itself from your computer.
To get started, from the main TrueCrypter interface, click on the > button at the bottom right of the screen. This will bring you the payment screen.
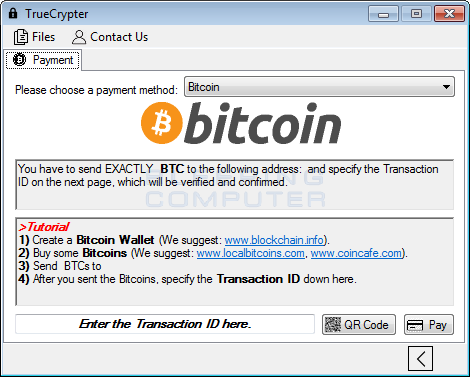
Simply click on the Pay button and confirm that the information is correct and TrueCrypter will automatically decrypt your files.
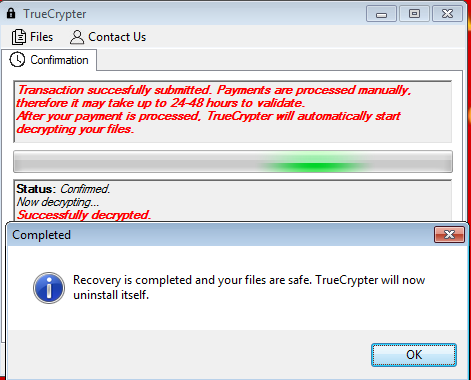
Once the files are decrypted, it will then proceed with removing itself from your computer.
For those who need help with this process, we have a support topic here: TrueCrypter Ransomware (.enc extension) Help & Support Topic
The odd acceptance of Amazon Gift Cards for a ransom Payment
Within the same week, we have seen two ransomware programs accept Amazon Gift Cards as a ransom payment. The first one was for a screenlocker in Android and now we have TrueCrypter. This is an odd choice of a ransom payment as the Amazon Gift Card funds can easily be tracked by Amazon. This, and the fact that the payment confirmation system is broken, makes me believe that this program was made by an amateur rather than a seasoned malware developer.
The TrueCrypter Encryption Process
When TrueCrypter is installed it will first check if the process is running under a Vmware, VirtualBox, or Sandboxie. If it is, it will then terminate the process and not continue. It then checks for certain processes associated with security programs. If it detects one of these processes, it will terminate it. The list of processes is searches for are:
antilogger, wireshark, charles, fiddler, netmon, reflector, sbiectrl, taskmgrThe TrueCrypter ransomware will then connect to the https://ask.fm/innocentask001 page, which contains a Caesar-21 encoded string. This string when decoded will contain configuration information such as the Command & Control TOR server address, ransom payment amounts, and the bitcoin address to use. For example, the encrypted string is currently:
XjwajwZwq=myyu://r2htkyphj5l4ldef.tsnts.lv GnyhtnsFiiwjxx=1337XkOg91bRK7Z7yUDXJf2KGyUw7uEcon GnyhtnsFrtzsy=0.2 FrfetsFrtzsy=115which decodes to:
ServerUrl=https://m2coftkce5g4gyza.onion.gq BitcoinAddress=1337SfJb91wMF7U7tPYSEa2FBtPr7pZxji BitcoinAmount=0.2 AmazonAmount=115It will then begin encrypting the files on the victim’s hard drives with AES-256 encryption. When it encrypts a file it will encrypt it with a unique AES key and then encrypt that key using RSA. This RSA encrypted AES decryption key is then stored at the end of the encrypted file. TrueCrypter will then append the .enc extension to the encrypted file and store the filename in the %AppData%\Microsoft\TrueCrypter\encrypted.dat file.
The file types targeted by TrueCrypter are:
.xlsx, .xls, xlsm, xltx, xltm, xlsb, xlam, .ods, .sxc, .csv, .tsv, .doc, .docx, .docm, .dot, .dotx, .dotm, .rtf, .odt, .txt, .msg, .odt, .pages, .rtf, .wpd, .wps, .pwi, .xml, .pot, pps, ppt, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .thmx, .pdn, .bmp, .gif, .jpg, .jpeg, .jpe, .jfif, .png, .tif, .tiff, .tga, .dds, .dib, .psd, .eps, .pdf, .tga, .ico, .gif, .mov, .mp4, .mp3, .avi, .wmw, .veg, .arw, .cr2, .crw, .dcr, .dng, .fpx, .mrw, .nef, .org, .pcd, .ptx, .raf, .raw, .rw2, .asp, .aspx, .cer, .cfm, .csr, .css, .htm, .html, .js, .jsp, .php, .rss, .xhtml, .7z, .7zip, .cbr, .deb, .gz, .pkg, .rar, .rpm, .sitx, .tar.gz, .zip, .zipx, .gzip, .tar, .c, .cc, .cxx, .class, .cpp, .cs, .dtd, .fla, .h, .hpp, .java, .lua, .m, .pl, .py, .sh, .sln, .swift, .vb, .vcxproj, .xcodeproj, .csproj, .resx, .config, .prproj, .asm, .inc, .jad, .json, .rc, .scpt, .src, .as, .mx, .au3, .bash, .sh, .bsh, .csh, .lex, .litcofee, .hxx, .d, .shtml, .xhtm, .xht, .hta, .ini, .reg, .jss, .jsm, .jsx, .ts, .tsx, .kix, .pas, .pp, .p, .inc, .lpr, .pm, .pmx, .php3, .php4, .php5, .phps, .phpt, .phtml, .ps, .ps1, .psm1, .pyw, .pyc, .r, .s, .splus, .rb, .rbw, .bat, .vbs, .cmd, .db, .sqlite, .sqlite3, .sql, .bookmarks, .indexDuring this encryption process it will also set Windows wallpaper to %AppData%\Microsoft\TrueCrypter\background.jpg and delete the shadow volume copies on the computer.
Last, but not least it will store configuration information in the %AppData%\Microsoft\TrueCrypter\TrueCrypter.xml file. This information is whether the computer was encrypted, if the key was sent to the Command & Control server, and the public RSA key used to encrypt the AES keys.
A big thanks to MalwareHunterTeam and Michael Gillespie for helping to analyze this infection.
Files associated with TrueCrypter
%AppData%\Microsoft\TrueCrypter\
%AppData%\Microsoft\TrueCrypter\background.jpg
%AppData%\Microsoft\TrueCrypter\Encrypted.dat
%AppData%\Microsoft\TrueCrypter\TrueCrypter.exe
%AppData%\Microsoft\TrueCrypter\TrueCrypter.xml
Registry entries associated with TrueCrypter
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\TrueCrypter %AppData%\Microsoft\TrueCrypter\TrueCrypter.exe
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











