A new ransomware called Alpha Ransomware was discovered and analyzed this week by Katja Hahn, S!Ri, MalwareHunterTeam, and Michael Gillespie. This ransomware encrypts your data with AES-256 encryption and then demands $400 USD in the iTunes Gift Cards in order to get your files back. Thankfully a decryptor for this infection was able to be created due to a discovered flaw.

This ransomware also continues the strange trend of using easily traceable payment methods like a iTunes Gift Card. Like TrueCrypter, who accepted Amazon Gift Cards, the acceptance of this type of payment seems foolish as it easily traceable compared to a currency like bitcoins.
Remove and Decrypt .encrypt files from the Alpha Ransomware
The good news is that Michael Gillespie was able to create a decryptor for this ransomware so a victim can get their files back for free. To use this decryptor, simply download it from the following link and execute it:
https://download.bleepingcomputer.com/demonslay335/AlphaDecrypter.zip
Once executed, the decryptor screen will open and you can select the C: drive and then decrypt your files.
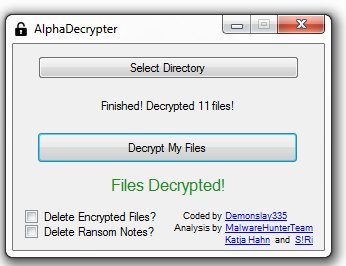
When using this decryptor, you can also put a checkmark to delete the ransom notes as this ransom will leave many notes throughout your drive.
The Alpha Ransomware Encryption Process
When this ransomware infects your computer it will place the main executable at %APPDATA%\Windows\svchost.exe and create an autorun called Microsoft. This autorun allows the ransomware to continue the encryption process if the computer is rebooted. This ransomware executable will automatically be removed after the ransomware finishes encrypting the victim’s data.
This ransomware has somewhat of a bizarre encryption routine. On the computer’s SystemDrive, which is usually the C: drive, it will only encrypt certain file types in the Desktop, My Pictures, and Cookies folders. All other folders on the SystemDrive will not be encrypted. The targeted file types for the SystemDrive are:
.3ds, .3fr, .3pr, .ab4, .ac2, .accdb, .accde, .accdr, .accdt, .acr, .adb, .agd1, .ai, .ait, .al, .apj, .arw, .asm, .asp, .aspx, .awg, .backup, .backupdb, .bak, .bat, .bdb, .bgt, .bik, .bkp, .blend, .bmp, .bpw, .c, .c, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfp, .cgm, .cib, .class, .cls, .cmd, .cmt, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cs, .csh, .csl, .css, .csv, .dac, .db, .db3, .dbf, .db-journal, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .der, .design, .dgc, .djvu, .dng, .doc, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dwg, .dxb, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fh, .fhd, .fpx, .fxg, .gif, .gray, .grey, .gry, .h, .h, .hbk, .hpp, .html, .ibank, .ibd, .ibz, .idx, .iiq, .incpas, .jar, .java, .jpeg, .jpg, .js, .kc2, .kdbx, .kdc, .kpdx, .lua, .mdb, .mdc, .mef, .mfw, .mmw, .moneywell, .mos, .mpg, .mrw, .myd, .ndd, .nef, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nwb, .nx1, .nx2, .nyf, .odb, .odf, .odg, .odm, .odp, .ods, .odt, .orf, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pat, .pcd, .pdf, .pef, .pem, .pfx, .php, .pl, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .ps, .psafe3, .psd, .ptx, .py, .ra2, .raf, .raw, .rdb, .rtf, .rw2, .rwl, .rwz, .s3db, .sas7bdat, .sav, .sd0, .sd1, .sda, .sdf, .sldm, .sldx, .sln, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stw, .stx, .svg, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .txt, .vb .vbs, .wb2, .x3f, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .ycbcraOn all other fixed disks, and not network or removable drives, it will encrypt any file it finds, including executables. When encrypting the data it will use AES-256 encryption and append the .encrypt extension to the name of the encrypted file. For example, test.jpg will become test.jpg.encrypt.
During the encryption process, the ransomware will create ransom notes called Read Me (How Decrypt) !!!!.txt in each folder a file is encrypted. The text of this ransom note is:
Greetings,
We’d like to apologize for the inconveniences, however, your computer has been locked. In order to unlock it, you have to complete the following steps:
1. Buy iTunes Gift Cards for a total amount of $400.00
2. Send the gift codes to the indicated e-mail address
3. Receive a code and a file that will unlock your computer.
Please note:,
– The nominal amount of the particular gift card doesn’t matter, yet the total amount have to be as listed above.
– You can buy the iTunes Gift Cards online or in any shop. The codes must be correct, otherwise, you won’t receive anything.
– After receiving the code and the security file, your computer will be unlocked and will never be locked again.
Sorry for the inconveniences caused.
Due to a bug in the software, the email addresses that you are supposed to send payment to are not supplied. These are:
criptote@hmamail.com
referas@hmamail.com
terder@hmamail.com
utera@hmamail.com
criptotak@hmamail.comFinally, the ransomware will change your desktop wallpaper to the following image.

As already stated, nobody should pay the ransom for this ransomware as a free decryptor was released. If anyone needs help with this ransomware or would like to discuss it, a support and help topic has been created here: Alpha Ransomware (.encrypt) Support Topic – Read Me (How Decrypt) !!!!.txt.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











