The notorious Jigsaw Ransomware has rebranded itself as CryptoHitman and now uses the character from the popular Hitman video games and movies. In addition to adding the Hitman character to its locker screen, CryptoHitman also covers the lock screen with pornographic images that are definitely not safe for work.
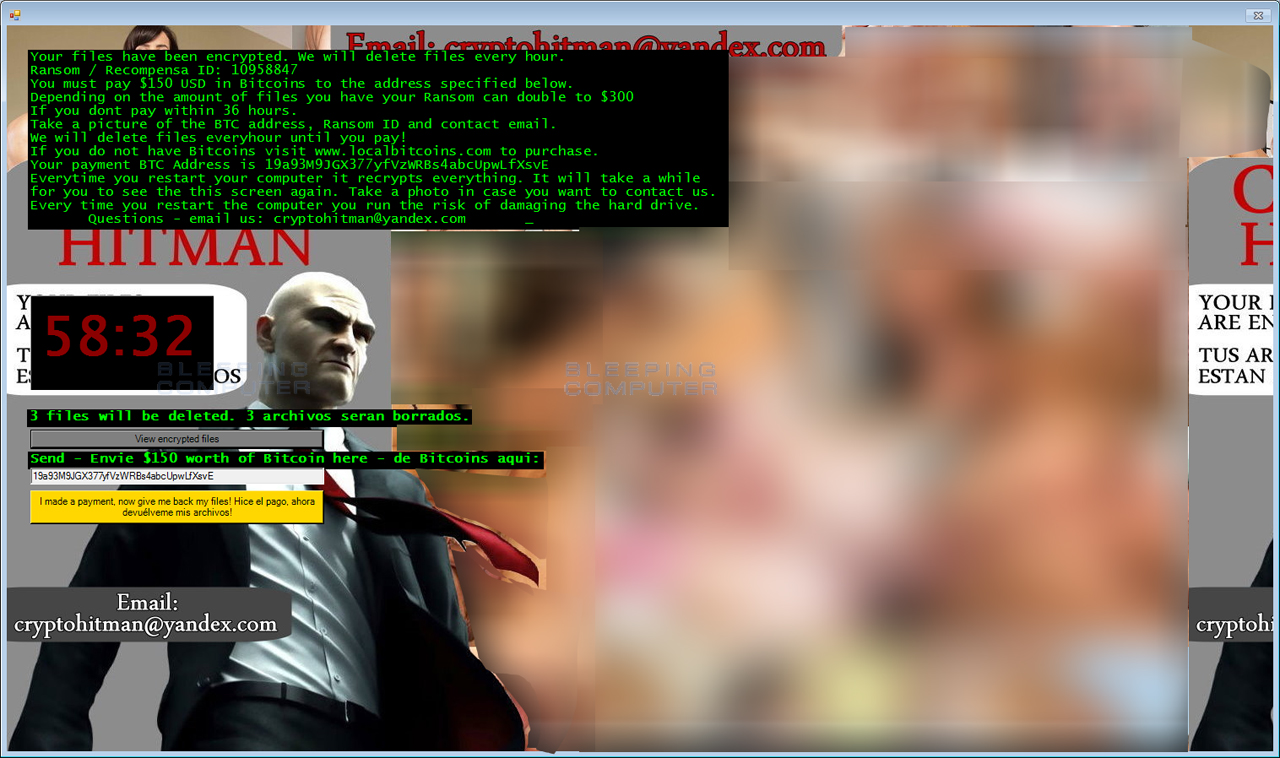
Like the previous Jigsaw ransomware infections, CryptoHitman will encrypt your data with AES encryption and demand a ransom payment before it will decrypt your files. In order to pay this ransom you will be required to send payment to cryptohitman@yandex.com.
Unfortunately, this version will still delete your files every time you restart the process and when the timer runs down to zero.
The only major differences is the new pornographic locker screen, the use of the Hitman character, the new .porno extension that is added to all encrypted files, and new filenames for the ransomware executables. Otherwise, this ransomware performs the same as the original Jigsaw Ransomware.
A big thanks to Fletch Sec for sharing the sample! Last, but not least, the owners of the Hitman franchise are not affiliated to this ransomware at all!
How to decrypt and remove the Jigsaw Ransomware
Thankfully, DemonSlay335was able to modify his existing Jigsaw Ransomware decryptor to also decrypt files encrypted by CryptoHitman. To decrypt your files, the first thing that you should do is terminate the%LocalAppData%\Suerdf\suerdf.exe
and %AppData%\Mogfh\mogfh.exe processes in Task Manager to prevent any further files from being deleted. You should then run MSConfig and disable the startup entry related to these executables.
Once you have terminated the ransomware and disabled its startup, let’s proceed with decrypting the files. The first step is to download and extract the Jigsaw Decryptor from the following URL:
https://download.bleepingcomputer.com/demonslay335/JigSawDecrypter.zip
Then double-click on the JigSawDecrypter.exe file to launch the program. When the program launches you will be greeted with a screen similar to the one below.
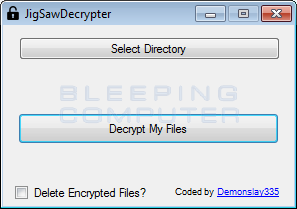
To decrypt your files simply select the directory and click on the Decrypt My Files button. If you wish to decrypt the whole drive, then you can select the C: drive itself. It is advised that you do not put a checkmark in the Delete Encrypted Files option until you have confirmed that the tool can properly decrypt your files.
When it has finished decrypting your files, the screen will appear as below.
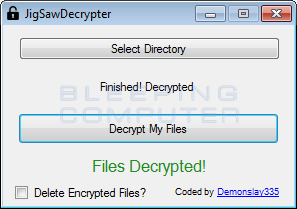
Now that your files are decrypted, I suggest that you run an antivirus or anti-malware program to scan your computer for infections. If you need help decrypting CryptoHitman files, you can ask for help in this support topic: CryptoHitman Ransomware Support and Help Topic (.Porno Extension Jigsaw variant).
Files associated with the CryptoHitman:
%LocalAppData%\Suerdf\
%LocalAppData%\Suerdf\suerdf.exe
%AppData%\Mogfh\
%AppData%\Mogfh\mogfh.exe
%AppData%\System32Work\
%AppData%\System32Work\Address.txt
%AppData%\System32Work\dr
%AppData%\System32Work\EncryptedFileList.txtRegistry entries associated with the CryptoHitman:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\mogfh.exe %AppData%\Mogfh\mogfh.exe
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











