Millions of Office 365 business users likely effected. Starting June 22 at 6:44 a.m. UTC, Avanan’s Cloud Security Platform started to detect a massive attack against its customers that were using Office 365. The attack included a very nasty ransomware virus called Cerber, which was spread through email and encrypted users’ files. Once encrypted, Cerber demanded a ransom be paid in order to regain access to the user’s documents, photos and files. So nasty in fact, that this virus actually played an audio file, informing the user that the computer’s files have been encrypted while a warning message was displayed on screen. Based on Avanan’s analysis, Microsoft detected the attack and started blocking the attachment as of June 23 at 11:34 a.m. UTC.
While difficult to precisely measure how many users got infected, Avanan estimates that roughly 57 percent of organizations using Office 365 received at least one copy of the malware into one of their corporate mailboxes during the time of the attack. This attack seems to be a variation of a virus originally detected on network mail servers back in early March of this year. As it respawned into a second life, this time Cerber was widely distributed after its originator was apparently able to easily confirm that the virus was able to bypass the Office 365 built-in security tools through a private Office 365 mail account.
Here is a screenshot of the virus as detected by Check Point Sandblast in the Avanan Cloud Security Platform:
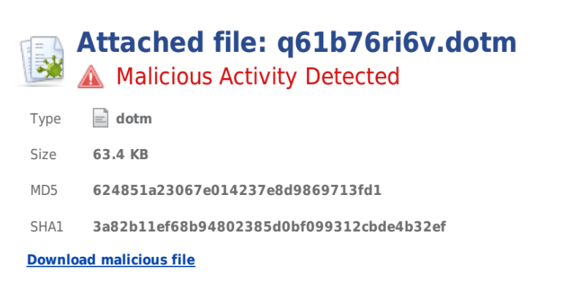
Avanan’s Cloud Security Platform immediately discovered the rebirth of this virus at customers using Check Point’s SandBlast solution through Avanan’s platform. Out of all Office 365 email users on the Avanan platform, 57 percent of organizations experienced the attack. The customers that activated Check Point’s SandBlast Zero-Day Protection on the Avanan Cloud Security Platform were able to block the attack before any infection occurred, as SandBlast identified the attack as a sophisticated zero-day ransomware. Traditional antiviruses/anti-malware tools were not able to detect this attack on cloud email program users at the time it occurred. Avanan’s security experts started to spot and correlate this same attack across multiple companies to conclude the extent and focus of this attack.
Additional facts:
- Cerber Ransomware – Similar to other ransomware, Cerber spreads via phishing emails. Once infected, a victim’s files become encrypted using the AES-265 and RSA encryption method, which is currently unbreakable, and they receive a message saying they need to pay a ransom of 1.24 bitcoins or ~500 USD to get their files back
- If Cerber had been allowed to reach these users, for any who opened the attachment it would have executed and the business costs would have been significant. Blocking this malware proactively with SandBlast protected Avanan customers from this threat
“Many users of cloud email programs believe they ‘outsourced’ everything to Microsoft or Google, including security,” explains Gil Friedrich, CEO of Avanan. “The reality is that hackers first make sure their malware bypasses major cloud email providers’ security measures, and so most new malware goes through cloud email programs undetected. This is why the majority of the users of Avanan’s Cloud Security Platform activate advanced malware protection layers such as Check Point SandBlast—a best practice that proved very effective in this incident and many prior incidents in protecting against even the most sophisticated and evasive attacks.”
“We are continuing to see a significant increase in the complexity of malware targeting business networks, and this attack is an excellent example. By utilizing several exploit kits, it was able to bypass traditional sandboxes. It also speaks to the effort hackers are putting into creating new zero-day attacks and the challenges businesses face in securing their networks against cybercriminals,” said Nathan Shuchami, head of threat prevention, Check Point. “Our SandBlast Zero-Day Protection product provides organizations the advanced threat prevention they need to stop malware at the pre-infection stage to ensure they are effectively secured against the latest threats.”
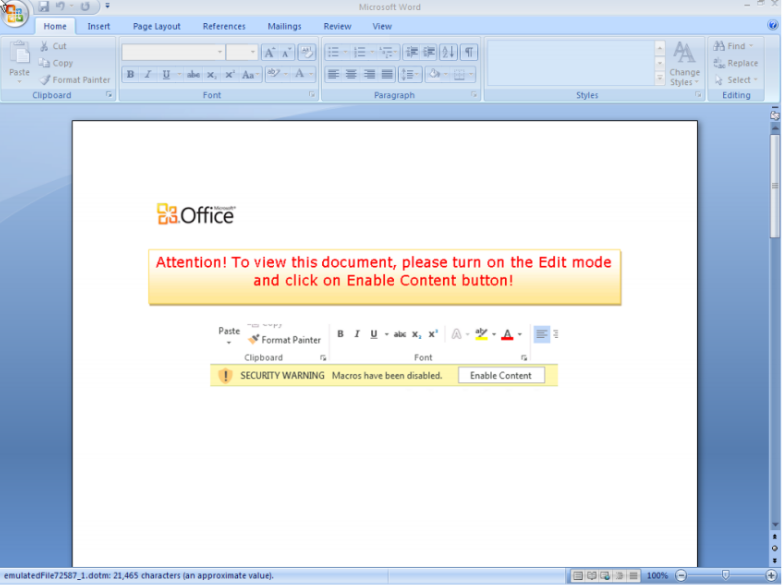
Screenshot of the virus as it appeared to infected users:
Source:https://www.avanan.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











