Is it a bug or is it a backdoor? Lenovo, and possibly other PC vendors, is exposed to a UEFI bug that can be exploited to disable firmware write-protection.
If the claims made by Dmytro Oleksiuk at Github are correct, an attacker can “disable flash write protection and infect platform firmware, disable Secure Boot, [and] bypass Virtual Secure Mode (Credential Guard, etc.) on Windows 10 Enterprise.”
The reason Oleksiuk believes other vendors are also vulnerable is that the buggy code is inherited from Intel. He writes that the SystemSmmRuntimeRt was copied from Intel reference code.
Lenovo complains in its advisory that it tried to make contact with Oleksiuk before he published the vulnerability.
The company says the vulnerable System Management Mode software came from an upstream BIOS vendor – making it likely that other vendors getting BIOS software from the same outlet will also be vulnerable.
There’s also a hint that Lenovo agrees with a speculation by Oleksiuk, that the code may be an intentional backdoor: “Lenovo is engaging all of its IBVs as well as Intel to identify or rule out any additional instances of the vulnerability’s presence in the BIOS provided to Lenovo by other IBVs, as well as the original purpose of the vulnerable code” (emphasis added).
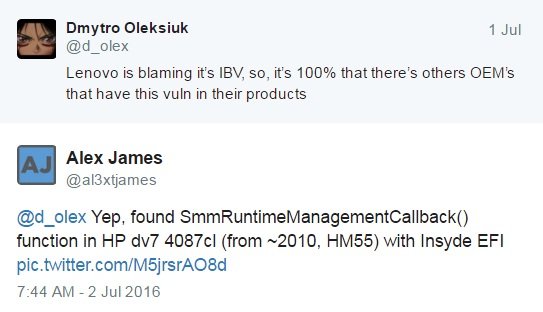
A follower of Oleksiuk said on Twitter the vulnerable code is also present in a 2010-era HP Pavillion machine:

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.