The malware economy is alive and well! And cyber criminals are making big money by using this business model.
The re-emergence of Adwind RAT provides additional proof to support this. This Java-based malware has been spotted over the weekend in several targeted attacks against Danish companies.
Given that the malicious email employed to deceive victims is in English, the attackers will most likely not stop at Danish borders.
The RAT was last seen a few months ago, after having been apparently taken down in 2015. It infected almost half a million people and organizationsworldwide. Now it has surfaced again, proving that cyber criminals are not ready to give up on using it.
A zero percent detection rate associated with these attacks in bound to make potential targets anxious about the effectiveness of their current defenses:
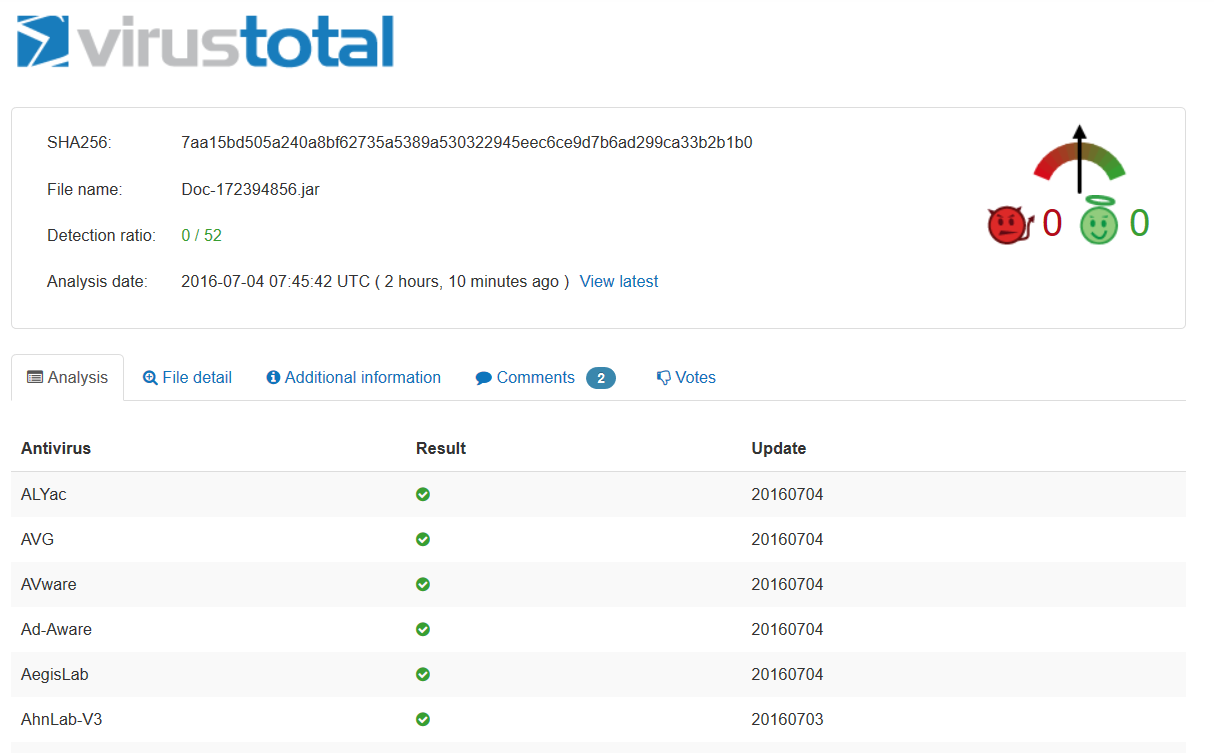
See full detection rates on VirusTotal.
Adwind RAT – cross-platform, multifunctional and plain destructive
For those yet unfamiliar with the term, here’s a quick definition to help put things into context:
Once the RAT is on the system, the attackers can remotely control the PC and gather key logs, webcam feeds, capture the audio feed, take screenshots and more.
Adwind is an especially insidious threat because it’s cross-platform and can perform this wide range of functions. Successful Adwind infections give online criminals a backdoor into PCs running Windows, OS X, Linux and even Android.
In the observed attacks, the spam email carrying Adwind is delivered with the following contents:
From: [spoofed / fake return address]
Subject Line: Order – Quotation Request
Attached:
Doc-172394856.jar
The .jar file is a Java archive, demonstrating that Java is still a key liability in computer systems everywhere. If an unsuspecting user activates the archive, the malicious code will be executed promptly.
The Adwind RAT can be run on any platform that supports Java Runtime Environment.
With 16 vulnerabilities in 2016 up to now, Java is already a culprit in many attacks against users and organizations all over the world. And we’re talking about serious security issues, which allow attackers to execute code, to overflow systems and gain privileges over the compromised system.
In the observed attacks, if the Adwind code is executed, the infected computer will be immediately recruited into a botnet.
This variant of Adwind RAT is configured to communicate with the following server [sanitized]: jmcoru.alcatelupd [.] Xyz.
This specific server has also been used in other RAT campaigns. Other campaigns have also employed various dynamic DNS services, such as:
cool [.] secure network [.] host
soycraft2 [.] duia [.] pw
bfbackup [.] baepaws [.] ru
loudpack101 [.] ddns [.] net
league [.] runescape [.] csgo [.] silicone routing [.] pw
airzwcvzq [.] nullroute [.] pw
manbks123 [.] ddns [.] net
machination [.] xinvasion [.] xyz
zarasrl2016 [.] ddns [.] net
airzwcvzq [.] nullroute [.] pw
The domains listed above and many others are all part of a wave of persistent attacks against a number of commercial and non-commercial organizations. Adwind has often been related to refined APT campaigns, so it’s no surprise that we should find this RAT in this context.
The objective of these type of attacks is always dual: to exfiltrate data from the compromised organizations and to open a backdoor which allows attackers to feed more malware into the affected machines.
Conclusion
We’ve seen it in ransomware attacks and it seems to be catching on in other malware campaigns as well. We’re talking about a new, more agile way to launch cyber attacks.
Online criminals seem to be turning their attention to more targeted attacksthat require a smaller infrastructure to carry out. This means less resources put into building infrastructure and a potentially bigger return on investment because of the targeted nature of the strike.
Avoiding large-scale campaigns also means thay have a higher chance of going undetected. This gives them more time to sit on the infected systems and extract more data from them.
The months spent between these resurges od Adwind could also signal that attackers are taking their time to prepare their strikes, to maximize their chances for success.
Surely, by the end of the year, we will be able to see if this tendency gains traction in the cyber criminal community. Unfortunately, we will probably have plenty of cyber attacks to analyse and draw conclusions from.
Source:https://heimdalsecurity.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











