Security researcher BloodDolly recently discovered a new file encrypter called Alfa Ransomware, or Alpha Ransomware, which is from the developers of Cerber. As BloodDolly is still currently analyzing this ransomware, not much is known about this ransomware at this time. Preliminary reports, though, indicate that files encrypted by Alfa Ransomware are not decryptable.
For those who wish to discuss or need help with Alfa Ransomware, we have created a dedicated Alfa Ransomware Help and Support topic in our forums.
Is it Alfa Ransomware or Alpha Ransomware?
This ransomware currently utilizes two different names in the ransom note and the TOR payment site. For example, in the ransom note, as shown in the next section, the ransomware will call itself Alpha Ransomware. While in the TOR payment site, it refers to itself as Alfa Decryptor with its own custom logo as shown below. Based on the development of a actual Alfa logo, my guess is that it will ultimately be called Alfa Ransomware.
How Alfa Ransomware Encrypts a Victim’s Files
It is currently unknown how Alfa Ransomware is distributed, but when infected the ransomware will scan all the local drives for certain file types. When it finds a targeted file extension it will encrypt the file and append the .bin extension to the encrypted file. For example, test.jpg will be encrypted to the filename test.jpg.bin. The file types currently targeted by the Alfa Ransomware are:
.c, .h, .m, .ai, .cs, .db, .nd, .pl, .ps, .py, .rm, .3dm, .3ds, .3fr, .3g2, .3gp, .ach, .arw, .asf, .asx, .avi, .bak, .bay, .cdr, .cer, .cpp, .cr2, .crt, .crw, .dbf, .dcr, .dds, .der, .des, .dng, .doc, .dtd, .dwg, .dxf, .dxg, .eml, .eps, .erf, .fla, .flvv, .hpp, .iif, .jpe, .jpg, .kdc, .key, .lua, .m4v, .max, .mdb, .mdf, .mef, .mov, .mp3, .mp4, .mpg, .mrw, .msg, .nef, .nk2, .nrw, .oab, .obj, .odb, .odc, .odm, .odp, .ods, .odt, .orf, .ost, .p12, .p7b, .p7c, .pab, .pas, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .pps, .ppt, .prf, .psd, .pst, .ptx, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .r3d, .raf, .raw, .rtf, .rw2, .rwl, .sql, .sr2, .srf, .srt, .srw, .svg, .swf, .tex, .tga, .thm, .tlg, .txt, .vob, .wav, .wb2, .wmv, .wpd, .wps, .no, .xlk, .xlr, .xls, .yuv, .back, .docm, .docx, .flac, .indd, .java, .jpeg, .pptm, .pptx, .xlsb, .xlsm, .xlsx
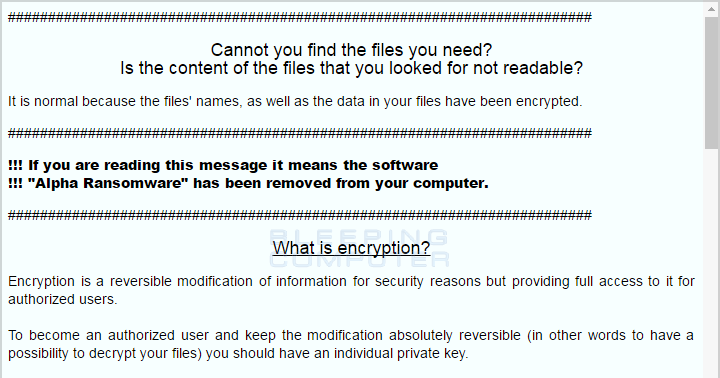
While encrypting the files, it will also create two ransom notes called README HOW TO DECRYPT YOUR FILES.HTML and README HOW TO DECRYPT YOUR FILES.TXT in the Documents and Desktop folders. These ransom notes contain information on what has happened to the victim’s files, links to the TOR payment sites, and a victim’s unique ID that must be used to login to the payment site.
The current TOR payment sites for the Alfa Ransomware are https://alfadecrfgqkcw6m.onion and https://2uxzf2mxe23f3clc.onion. Please note that these are TOR sites and will not work within a normal browser.
The Alfa Ransomware will also create a autorun for the malware executable so that it is started every time a user logs into Windows. The autorun will be called MSEstl and the executable will be located in %UserProfile%\AppData\Roaming\Microsoft\Essential\msestl32.exe.
Finally, the ransomware will delete the Shadow Volume Copies on the victim’s computer so that they are unable to use them to recover their unencrypted files.
The Alfa Decryptor Site
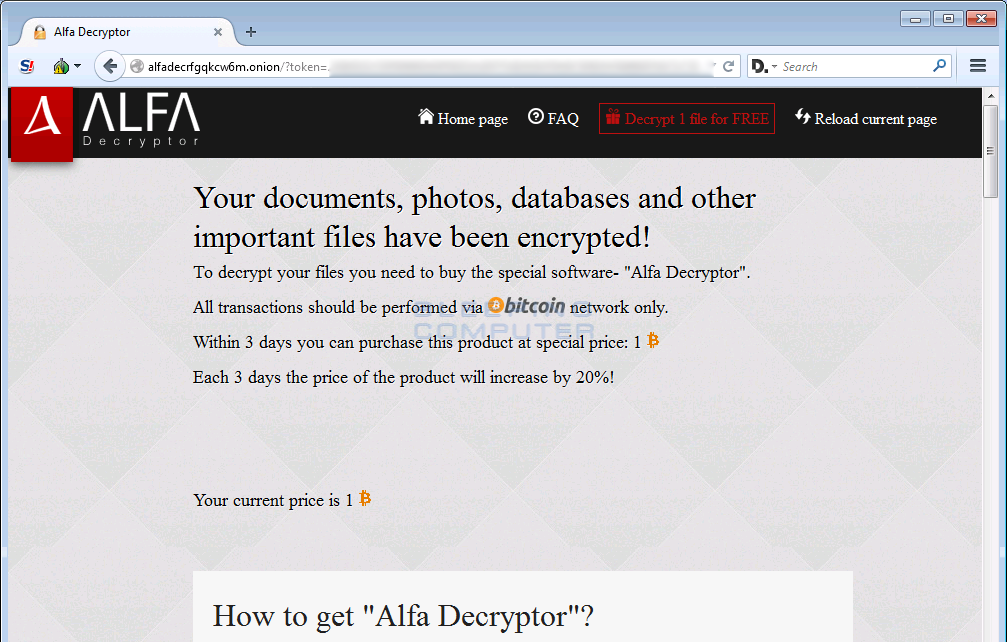
When a user goes to the TOR payment site, they will be shown a login form. In this form, they need to insert the victim’s ID listed in the ransom note. Once they login they will be presented with the Alfa Decryptor page as shown below. This page allows them to decrypt 1 file for free, find the ransom amount, the bitcoin address they must send the payment to, and the ability to check for payment status.
Once the payment has been completed, a decryptor will be made available to them on this page.
Also included in the Alfa Decryptor site is a Frequent Asked Questions page. This page is shown below.
.png)
As already stated, unfortunately at this time there is no way to decrypt files encrypted by Alfa Ransomware for free. If anything changes, we will be sure to post about it on the site. For those who wish to discuss this information or receive support, you can use our Alfa Ransomware Help and Support topic.
Files associated with the Alfa Ransomware:
%UserProfile%\AppData\Roaming\Microsoft\Essential\msestl32.exe
README HOW TO DECRYPT YOUR FILES.HTML
README HOW TO DECRYPT YOUR FILES.TXTRegistry entries associated with the Alfa Ransomware:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\MSEstl %UserProfile%\AppData\Roaming\Microsoft\Essential\msestl32.exe
HKCU\Software\Microsoft\Windows\CurrentVersion\[random]
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











