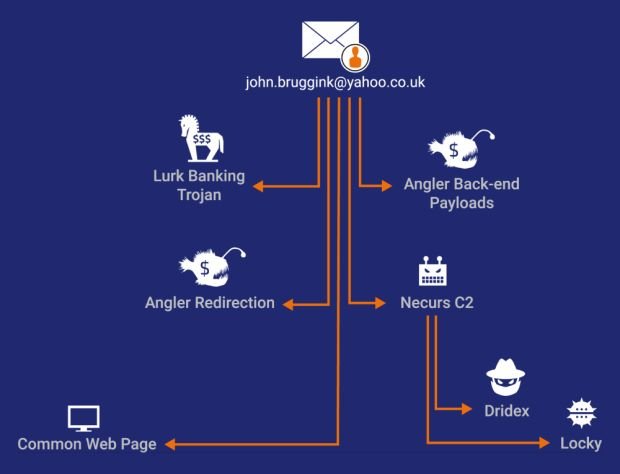
Email address found used for registering C&C domain names for Lurk, Angler, and Necurs infrastructure.
As many infosec professionals have initially suspected, there is a connection between the arrests made by Russian police at the end of May and the ulterior downfall of the Angler Exploit Kit infrastructure.
According to Cisco’s Talos team, these connections go deeper in the heart of the crimeware underground than previously considered.
The Lurk gang arrests and the subsequent “coincidences”
At the end of May, Russian authorities announced they arrested 50 suspects they believed to be involved in the creation and distribution of the Lurk banking trojan that stole around $30 million from Russian banks.
A week after these arrests, several security firms announced that Angler, the most popular exploit kit in the cyber-crime market, has ceased all activity.
A week later, the Necurs botnet also stopped all activity, but eventually came back to life three weeks later.
The connection between all these incidents
The Cisco Talos team says that all these downtimes are not accidental. According to an analysis of various domain names used by these three cyber-crime infrastructures, Cisco says it uncovered a common link between all.
The company says that 85 percent of the 125 C&C (command and control) servers used by the Lurk banking trojan were registered by a man utilizing the email address john[.]bruggink@yahoo[.]co[.]uk.
In research published last February, this very same email address was used to register Angler payload delivery domains in a cyber-crime campaign that spread the Bedep clickfraud malware.
That same research from February also discovered the same email address used to register a small number of domains used for the C&C servers of the Necurs botnet.
The Lurk group one of the crimeware’s scene biggest players
While Necurs eventually reappeared, Angler did not. Necurs’ reappearance may also have to do with the fact that this is one of the biggest sources of spam that deliver the Dridex banking trojan and the Locky ransomware, operations conducted by a supposedly different group altogether.
There are ties and collaborations between different cyber-crime groups just like partnerships between legitimate businesses. While it may have taken the Dridex gang around three weeks to navigate around the problems caused by the Lurk gang’s arrest, they did manage to restore Necurs, a botnet which has been historically spreading Dridex and Locky.
The john[.]bruggink@yahoo[.]co[.]uk email address does not show a clear line interconnecting different malware operations but looks more like a root. When Russian authorities pulled it out, it pulled out Angler and Lurk, but not Necurs, even if they took down some of its servers along the way.
“One thing this does show is that despite all the variety and different actors making use of these technologies there potentially was a much smaller group responsible for a far larger chunk of the crimeware space than previously estimated,” writes Cisco’s Nick Biasini.
All that’s left for Russian authorities is to bring down the Dridex gang, considered the most professional and well-organized cyber-crime ring on the Web.
Note: The demise of the Nuclear exploit kit has nothing to do with these arrests. Check Point security researchers say that Nuclear’s shutdown was a voluntary gesture after they published an in-depth report about the exploit kit’s inner-workings.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











