By mid-July 2016, the Afraidgate campaign stopped distributing CryptXXX ransomware. It is now distributing the “.zepto” variant of Locky. Afraidgate has been using Neutrino exploit kit (EK) to distribute malware after Angler EK disappeared in early June 2016. As we previously reported, this campaign continues to utilize gate domains using name servers from afraid.org.
Changing Payloads
As early as June 29, 2016, we saw the Afraidgate campaign deliver Locky ransomware. This campaign switched between delivering CryptXXX and Locky ransomware during the next two weeks. July 11, 2016, was the last time we saw Afraidgate deliver CryptXXX. Since then, this campaign has been consistently delivering Locky.
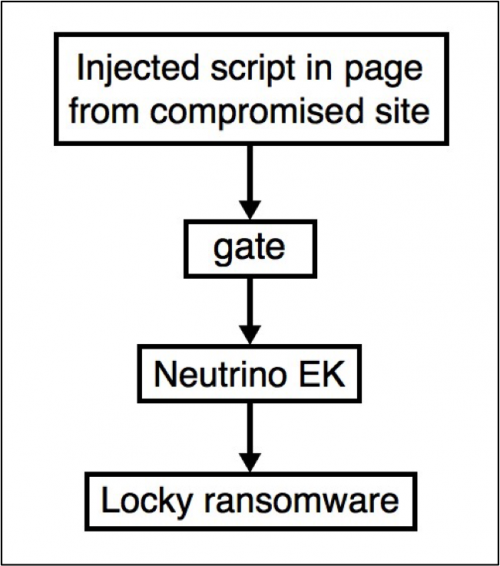
Figure 1: Flow chart for an infection from the Afraidgate campaign.
This variant of Locky uses a .zepto file extension for any encrypted files. We started seeing this Zepto variant of Locky after a three-week outage of the Necurs botnet ended on June 21, 2016. Locky had been absent during the outage, but after the botnet returned, Locky also reappeared with new anti-sandboxing and evasion techniques.
Some security vendors have named this new variant Zepto ransomware, but they still highlight its similarities with the previous Locky variant.
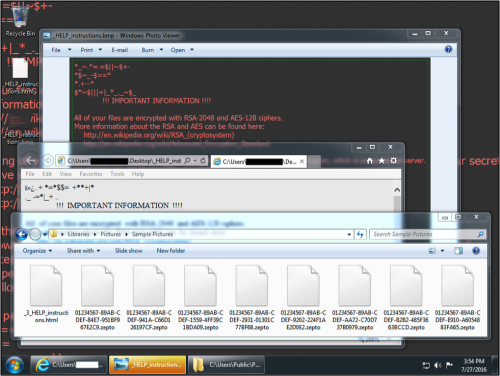
Figure 2: Desktop of a Windows host infected with the Zepto variant of Locky.
From Angler EK to Neutrino
Like most campaigns, Afraidgate switched to Neutrino EK after Angler EK disappeared in early June 2016. We have seen two other large-scale campaigns also move from Angler to Neutrino EK: the EITest and pseudo-Darkleech campaigns. For now, Neutrino appears to be distributing the majority of ransomware for EK-based infections. Outliers still exist, like Magnitude EK distributing Cerber ransomware. Rig EK has also been noted for an occasional ransomware infection. But the bulk of EK-based ransomware infections are most often attributed to Neutrino EK.
Example of an Afraidgate Infection

Figure 3: Traffic from an Afraidgate infection filtered in Wireshark.
As noted in our previous post on EK fundamentals, EK-based campaigns start with a compromised website. Pages from the compromised site have injected script that, in this case, lead to an Afraidgate domain behind the scenes.

Figure 4: Injected script in page from a compromised website.
After the victim’s computer connects to the URL on an Afraidgate domain, the server returns more Javascript with an iframe leading to a Neutrino EK landing page.

Figure 5: Afraidgate domain leading to the Neutrino EK landing page.
Neutrino EK domains for this campaign tend to use .top as the top level domain (TLD). Otherwise, we see no surprises. Neutrino is a well-known EK that has been documented by others.
Conclusion
Domains, IP addresses, and other indicators associated with Neutrino EK and Locky are constantly changing. We continue to investigate this activity for applicable indicators to inform the community and further enhance our threat prevention platform.
Source:https://researchcenter.paloaltonetworks.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











