While many email providers, clients, and anti-spam engines have become adept at detecting spam, malicious messages sent via high-profile, legitimate providers are much harder to catch. Threat actors continue to look for new ways to bypass these engines and, in the latest example of innovative approaches to malware distribution, have managed to co-opt PayPal services in a small campaign.
Proofpoint analysts recently noticed an interesting abuse of legitimate service in order to deliver malicious content. Specifically, we observed emails with the subject “You’ve got a money request” that came from PayPal. The sender does not appear to be faked: instead, the spam is generated by registering with PayPal (or using stolen accounts) and then using the portal to “request money.” We are not sure how much of this process was automated and how much manual, but the email volume was low.
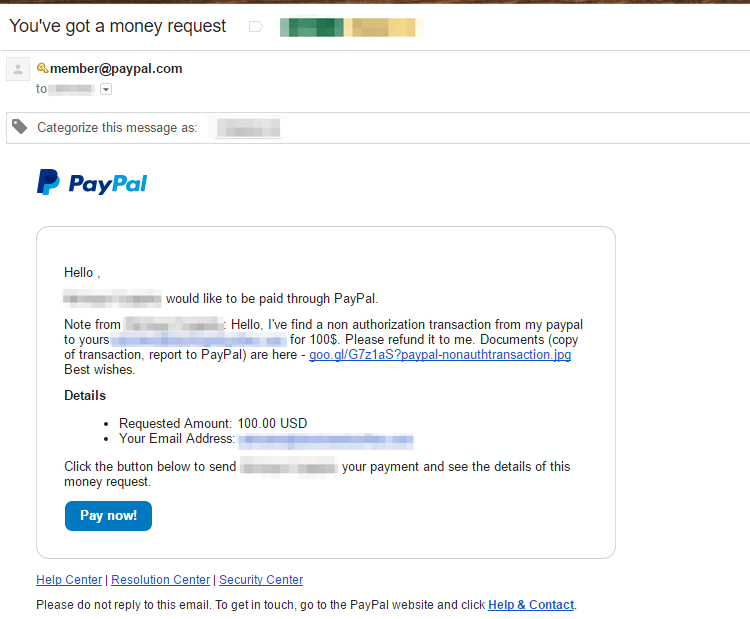
Figure 1: Email delivering malicious content
Although the actual email address is obscured in Figure 1, this message was sent to a Gmail inbox. Gmail failed to block the email since it appears legitimate. PayPal’s money request feature allows adding a note along with the request, where the attacker crafted a personalized message and included a malicious URL. In a double whammy, the recipient here can fall for the social engineering and lose $100, click on the link and be infected with malware, or both.
If the user does click on the Goo.gl link, they are redirected to katyaflash[.]com/pp.php, which downloads an obfuscated JavaScript file named paypalTransactionDetails.jpeg.js to the user’s system. If the user then opens the JavaScript file, it downloads an executable from wasingo[.]info/2/flash.exe. This executable is Chthonic, a variant of the Zeus banking Trojan. The command and control (C&C) for this instance is kingstonevikte[.]com. The following screenshot more clearly illustrates the sequence of events:
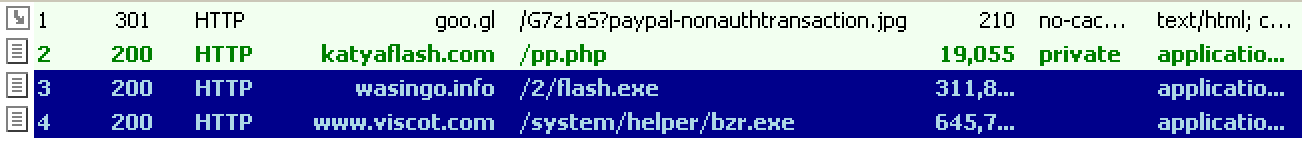
Figure 2: Network traffic generated starting with user clicking on the malicious URL and opening the downloaded JavaScript
It is also interesting that Chthonic downloads a second-stage payload, a previously undocumented malware “AZORult” which we are currently investigating:

Figure 3: Logo used internally by the AZORult module
Conclusion
Although the scale of this campaign appeared to be relatively small (this particular example was only detected through one of our spamtraps; as of the writing of this blog, the malicious link has only been clicked 27 times according to Google Analytics for the URL shortener), the technique is both interesting and troubling. For users without anti-malware services that can detect compromised links in emails and/or phone homes to a C&C, the potential impact is high. At the same time, the combined social engineering approach of requesting money via PayPal from what appears to be a legitimate source creates additional risk for untrained or inattentive recipients, even if they are not infected with the malicious payload.
Source:https://www.proofpoint.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











