Venmo has patched multiple flaws that could have allowed an attacker to steal as much as $2,999.99 from unsuspecting victims using Siri.
Venmo is a mobile app that allows friends to exchange payments between one another in a simplified way. Those with the app can pay a friend for covering a dinner bill, for example. They can also send them a “charge” payment request for outstanding expenses, with a weekly charge limit set at $2,999.99.
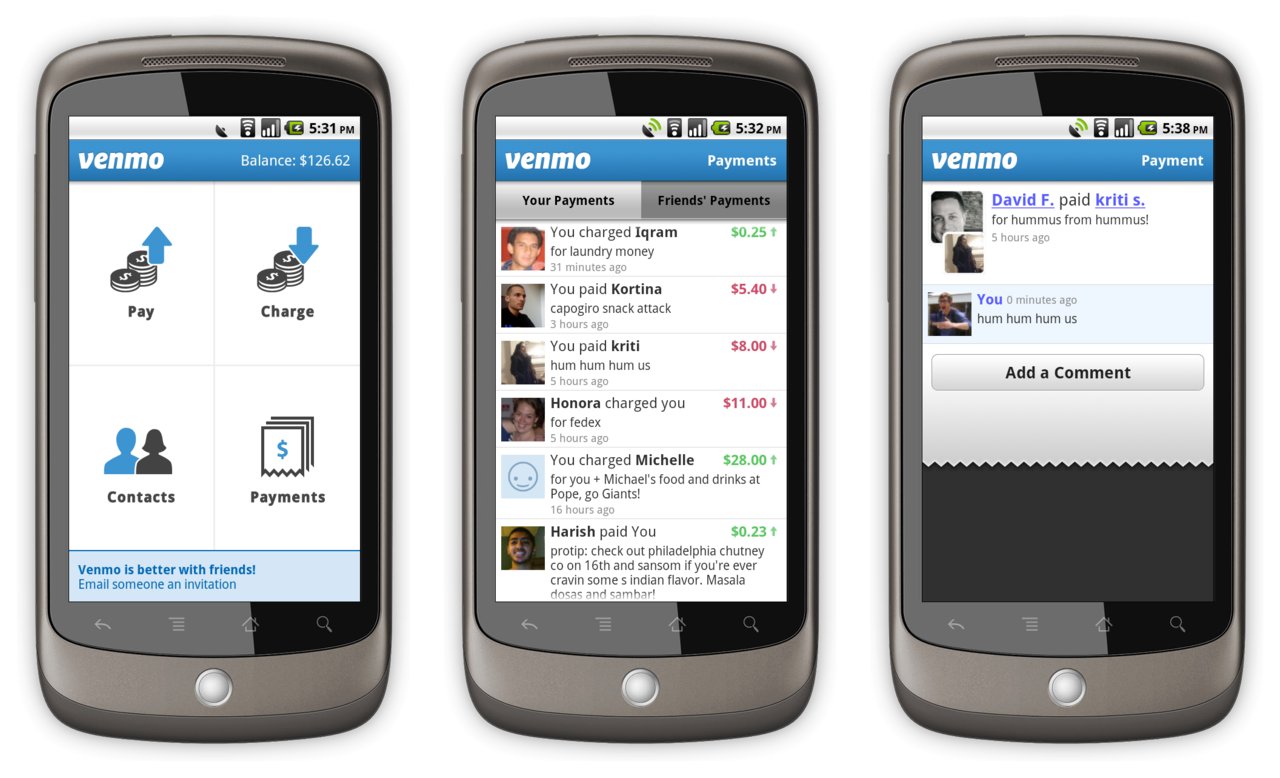
The friend must accept the “charge” request in order to submit a payment. But Martin Vigo, product security engineer for Salesforce.com, found a way to execute that action for a victim, and all without ever unlocking a compromised device.
Vigo came across the vulnerabilities while using the Venmo app to pay back a friend for a bottle of gin. He found he could pay his friend simply by responding with a 6-digit code to a SMS message sent to his phone.
That’s when the security researcher remembered Apple devices with iOS 9 by default enable Siri to send SMS messages when they are locked. He also recalled Apple comes with the “Text message Preview,” which allows a user to see a text and part of the content.
“If we combine these two, I am able to see the SMS with the code and can reply using Siri,” Vigo explains in a blog post. “All this without unlocking the device. All this out of the box. WIN?!?”
All that remained was activing SMS texts on a victim’s phone. Sure enough, the researcher discovered an attacker could send the word “Start” to 86753, and the service would be activated. From there, an actor could submit a charge request to a victim, ask Siri to tell them the six-digit code sent to the compromised device, and complete the payment.
Vigo demonstrates this process can take less than two minutes in a proof-of-concept demonstration video found below:
https://youtu.be/2BmN7NCMES4
But that’s not all. By brute forcing codes, Vigo found that Venmo used time-based protection to require a user try again in 5 minutes if they had sent over too many invalid codes. This meant an attacker could potentially brute force a charge payment from a victim.
As the researcher explains:
“Anyway, the point is, after 5 tries I had to wait about 5 minutes till I could try another 5 times. The codes are six digits long so we have 1 million possibilities and we can try 5 codes every 5 minutes. Do the math. Possible but not feasible.”
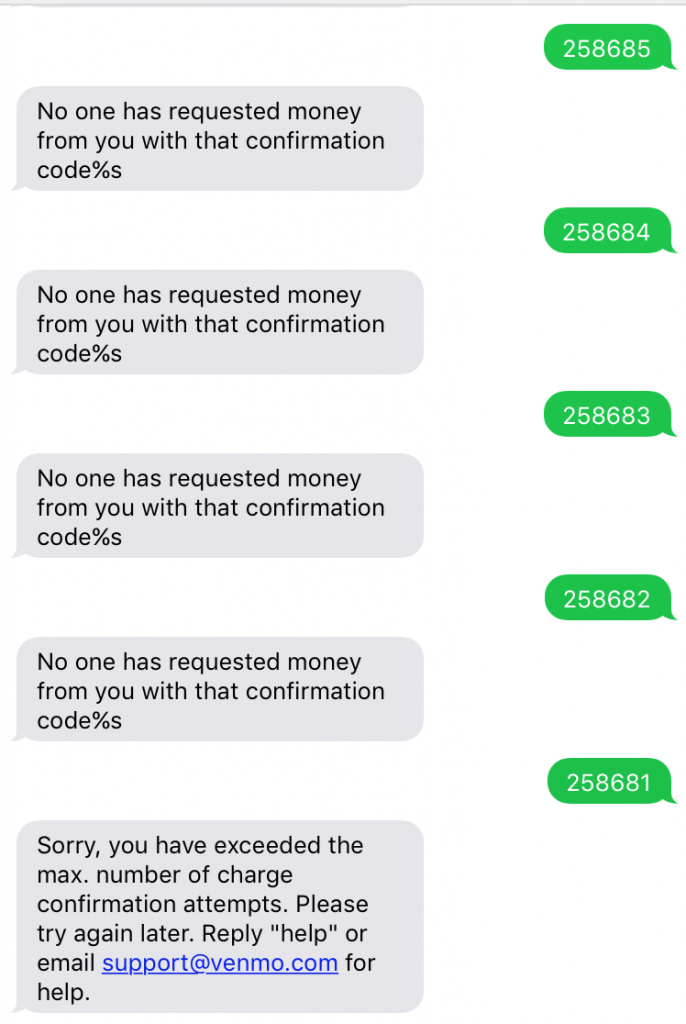
Combined with the revelation that each new charge request comes with its own code and does not invalidate old requests, an attacker could theoretically send the same request to multiple victims via user enumeration. That would improve the attacker’s chances of guessing the right code.
Venmo questioned the logic of some of Vigo’s findings. Nevertheless, after receiving notice of the issues in June, the developers of the app decided to kill the “reply-to-pay” functionality, which in essence prevents attackers from replicating Vigo’s exploit.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











