This week there has been a lot of news about a flaw in Windows that could be used by web sites to easily gain access to a visitor’s Windows login name and password. When I tested this flaw it was downright scary. Using a test site for this flaw, the site was able to get my test Microsoft Account login name and the hash of its password in a few seconds. Then it took the site less than 30 seconds to crack the password! What is even scarier, is that this flaw is not new and was discovered in March 1997!
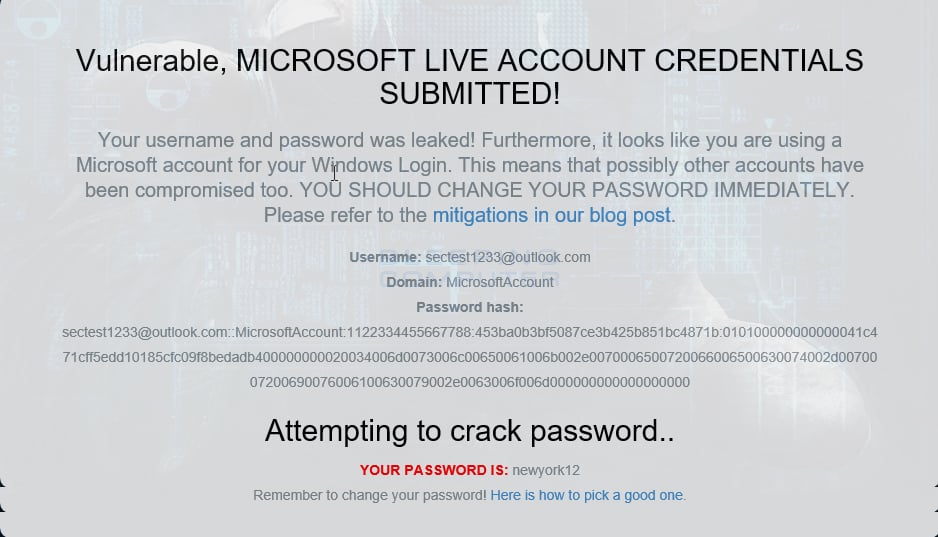
Yes. I changed the password already.
News about this flaw was recently reported again by VPN company Perfect Private and by ValdikSS, who is affiliated with the Russian VPN service ProtoVPN. They have both set up test sites that demonstrate this flaw so that visitors can determine if they are affected and should change their passwords. I have no idea what information they keep from these tests, so I would change your password if they are able to detect your info. Perfect Private has a test page here and ValdikSS has one here.
While in the past this flaw was serious, it has become downright dangerous now that more and more people are using Windows 10 and logging into Windows with a Microsoft Account. With the use of Microsoft Accounts, credentials that can be used on the Internet are now more readily exposed through this flaw. Furthermore, since so many users use the same credentials on their Microsoft account as they do on other services, a hacker could potentially gain access to many other sites that a victim uses. This means that a victim’s email accounts, bank accounts, government accounts, business accounts, etc could become compromised.
This bug works by somehow getting a user to open a remote SMB network share to access a file, When you connect to a SMB share, Windows automatically sends your user name and your hashed password to try to automatically login into the share. The problem is that this happens even when the share is located off of your network or over the Internet. See the problem now?
Essentially, all an attacker has to do is create a web page that contains a link to an image hosted on a SMB server under their control. They can then monitor the server for credentials being passed to it and then run password cracking programs on the exposed password hashes. As many people use extremely weak passwords, these programs can crack the passwords incredibly fast. When I say fast, I mean cracking a weak password in 4 seconds.
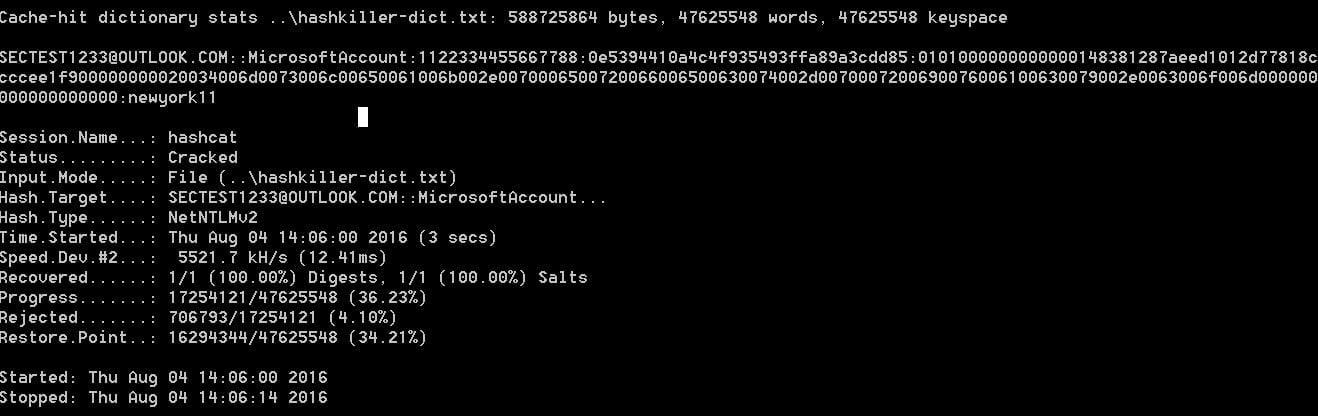
Unfortunately, Microsoft has not released an advisory regarding this flaw. When I, and other sites, have reached out to Microsoft, we all received the same token response.
We’re aware of this information gathering technique, which was previously described in a paper in 2015. Microsoft released guidance to help protect customers and if needed, we’ll take additional steps.
– a Microsoft spokesperson
Unfortunately, to mitigate this flaw, there is not a lot of good info out there. Microsoft didn’t really offer anything useful that I could get to work and Perfect Private advises you to stay away from Microsoft Edge and Internet Explorer. I knew there was a better way, so I dug around and found a way that prevented this information from being disclosed.
Preventing Edge and Internet Explorer from disclosing your Login Information
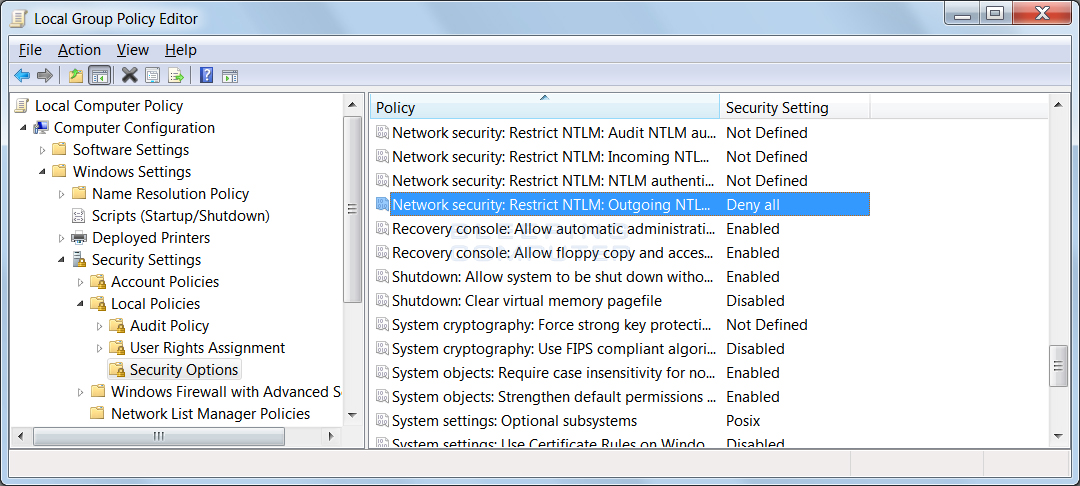
In order to prevent Microsoft Edge and Internet Explorer from leaking your account credentials, you need to enable a particular policy on the computer called Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers. This policy will prevent Windows from sending credentials to remote servers when accessing a SMB share. Though I tested this on my computer with absolutely no problems, this could cause issues in a corporate environment. Therefore, please perform tests before putting this change into production. There is another policy that I will describe below that should allow you to whitelist certain servers so that credentials are sent as normal.
To enable this policy, you should open the Group Policy Editor and navigate to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers as shown below.
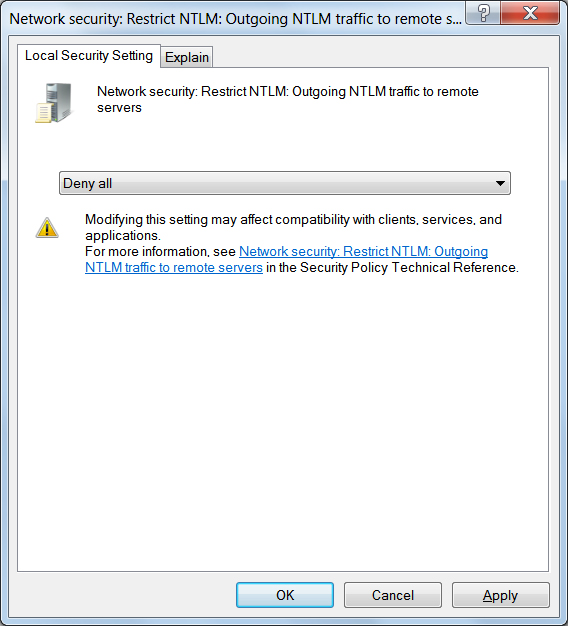
To enable this policy, double-click on the Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers and configure it to Deny all as shown below. You can also select Audit All to generate Windows event logs that show what remote servers you are sending credentials. This can be used to create a whitelist in the other policy described later in the article.
Now that you have restricted outgoing NTML traffic, Windows will no longer send your NTLM credentials to remote shares. You can test this, by going to one of the credential leak test sites described earlier in the article. It should now say the computer is not vulnerable.
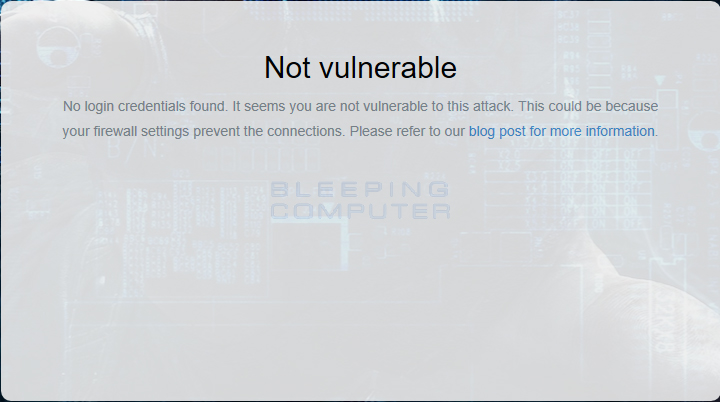
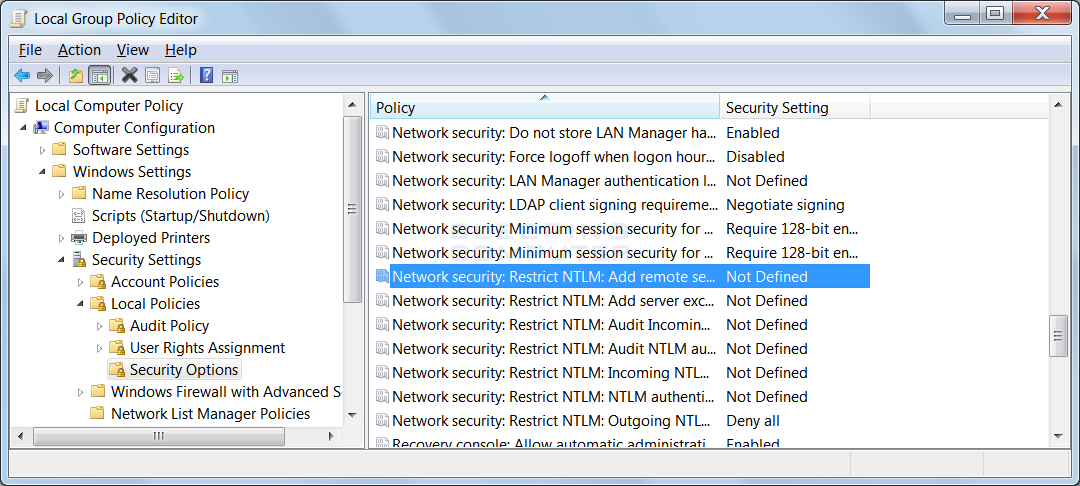
For those who need to send credentials to a remote server, you can add certain servers to a whitelist through the To enable this policy, you should open the Group Policy Editor and navigate to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication as shown below.
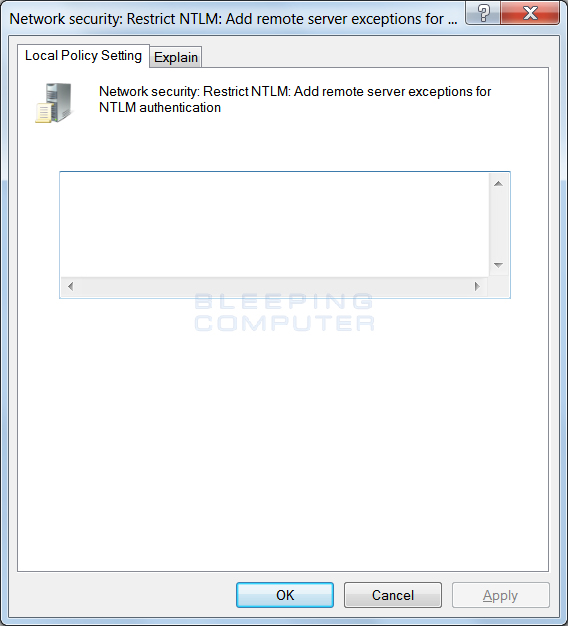
To enable this policy, double-click on the Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication and add the servers that you wish to whitelist. This will allow the credentials to be sent to these servers as normal.
Your computer will now be protected from the NTML Credentials Leak, while at the same time being able to use remote SMB servers as needed.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











