The flaw, which allows a malicious website to extract user passwords, is made worse if a user is logged in with a Microsoft account.
A previously disclosed flaw in Windows can allow an attacker to steal usernames and passwords of any signed-in user — simply by tricking a user into visiting a malicious website.
But now a new proof-of-exploit shows just how easy it is to steal someone’s credentials.
The flaw is widely known, and it’s said to be almost 20 years old. It was allegedly found in 1997 by Aaron Spangler and was most recently resurfaced by researchers in 2015 at Black Hat, an annual security and hacking conference in Las Vegas.
The flaw wasn’t considered a major issue until Windows 8 began allowing users to sign into their Microsoft accounts — which links their Xbox, Hotmail and Outlook, Office, and Skype accounts, among others.
Overnight, the attack got larger in scope, and now it allows an attacker to conduct a full takeover of a Microsoft account.
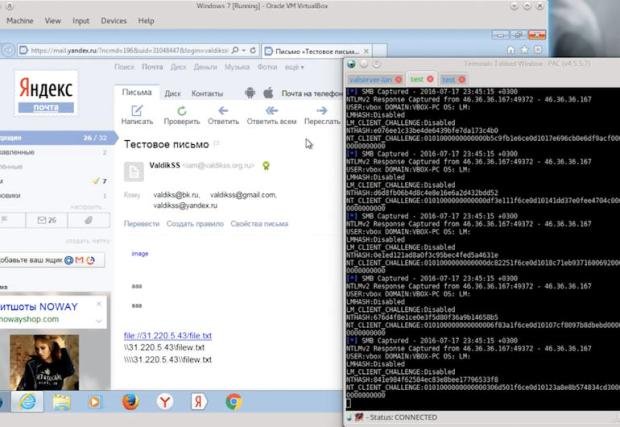
The flaw works because Internet Explorer and Edge (on Windows 10) allow a user to access local network shares but don’t fully block connections to remote shares.
To exploit this, a hacker has to trick a user into visiting a specially rafted web page in Internet Explorer or Edge (on Windows 10) that points to their own network share. The browser will silently send usernames and hashed passwords to the network share, which can then be scooped up and stolen.
If passwords are weak, they can be easily unscrambled and used to log in to user accounts.
The flaw can also be triggered by sending a trick email to a victim who uses Microsoft Outlook.
Perfect Privacy, a virtual private networking (VPN) provider, said in a blog post that VPN connections are also affected. If a user visits a site while they’re connected to a VPN, their credentials will also leak, potentially affecting the anonymity of the user.
The group set up a proof-of-exploit page that churns back your username, domain, and hashed password — which it then tries to crack (if it’s an easy-to-guess password, it’ll take just seconds).
We were able to verify on three computers in our lab using separate disposable Microsoft account logins. It’s not immediately clear where any submitted data goes, so we strongly recommend that you do not submit your own credentials to the site.
There’s a simple mitigation, according to the group. Don’t use Internet Explorer, Edge, or Microsoft Outlook, and don’t log in to Windows with a Microsoft account.
Chrome and Firefox users aren’t affected.
A Microsoft spokesperson suggested that the company would not patch the flaw.
“We’re aware of this information gathering technique, which was previously described in a paper in 2015. Microsoft released guidance to help protect customers and if needed, we’ll take additional steps,” the spokesperson said.
Source:https://www.zdnet.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.