Corporate cybercrime and information theft has become a very lucrative business for malware developers. Not only does it allow them to steal corporate secrets to sell to the highest bidder, but it can also provide them with undisclosed financial reports that that can be used on the stock market
BleepingComputer was recently sent a sample by one of its visitors of a computer infection that steals certain file types by uploading them to to a server under the developer’s control. This allows the malware developer to have full access to a victim’s files in order to harvest information such as corporate secrets, passwords, financial information, and tax information.
Anatomy of the Attack
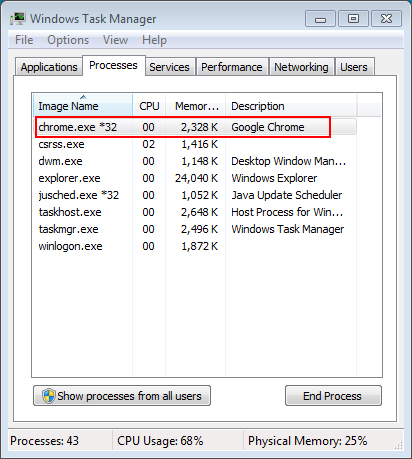
When the malware first runs it will configure itself to automatically start on login by configuring an entry in the Windows Registry. It will then inject itself into a running process, such as a web browser process. For example, this malware injected itself into Chrome as shown below.
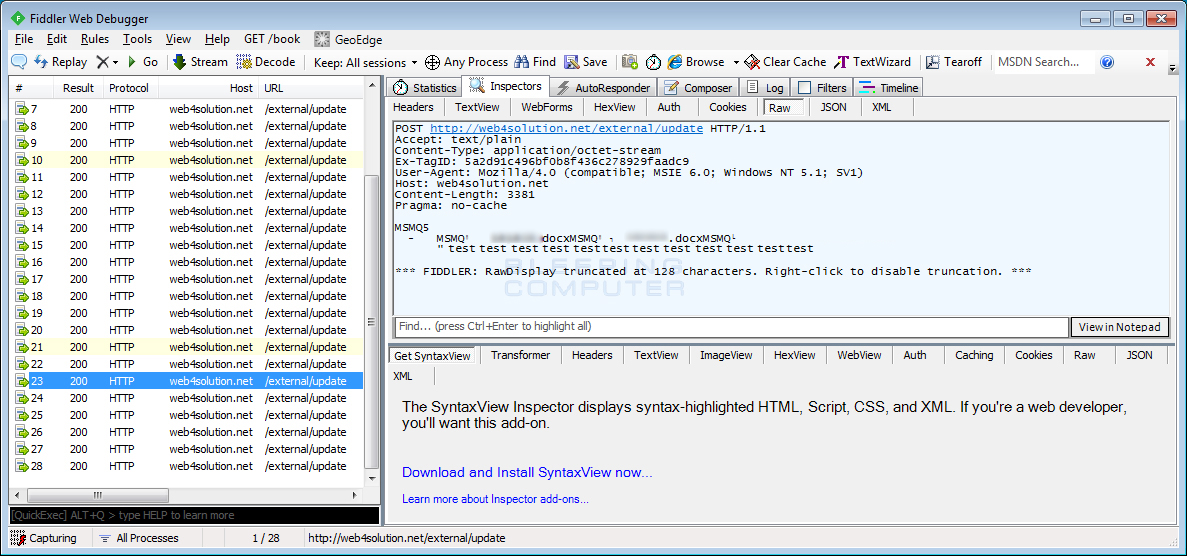
The malware will now start sending information to the Command & Control. When communicating it will use the Windows Message Queuing protocol (MSMQ) over HTTP to send messages to the Command & Control server currently located at web4solution.net.
When visiting the web4solution.net domain, you previously were shown a web site for a company called WebSolutions. When I contacted WebSolutions, it was discovered that the C2 server domain had been using an IFRAME to display the legitimate company’s web site to visitors. Though the C2 is still active, the IFRAME has since been blocked.
The first two messages sent by the malware will contain information about the victim’s computer and the programs installed on it. The information sent will include:
- Victim’s computer name
- User name
- Version of Windows
- Installed Service Pack
- List of programs found under HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall registry key. The included information from this key will be the contents of the DisplayName, DisplayVersion, and InstallLocation
values.
It will then proceed to scan the entire drive, starting with the user’s Desktop folder for files that contain the following extensions:
INP, SQL, PDF, RTF, TXT, XLSX, XLS, PPTX, PPT, DOCX, DOCIf it detects a file with one of the above extensions, it will upload the entire file to the Command & Control server.
Of particular note, is the targeted INP extension, which is commonly associated with the design and engineering program called Abaqus/CAE. According to Wikipedia:
Abaqus is used in the automotive, aerospace, and industrial products industries. The product is popular with academic and research institutions due to the wide material modeling capability, and the program’s ability to be customized. Abaqus also provides a good collection of multiphysics capabilities, such as coupled acoustic-structural, piezoelectric, and structural-pore capabilities, making it attractive for production-level simulations where multiple fields need to be coupled.
Based on the targeted file types, especially the specialized INP extension, it indicates that the malware is targeting corporations in order to steal corporate information and trade secrets.
For every file that is uploaded, the path and filename will be added to the C:\Users\[username]\uninst.dll file. This file will have its permissions changed so that no user is able to access it.
At this time, the malware is currently detected by 34 out of 55 security programs according to it’s VirusTotal report, but none of them are properly identifying it as of yet. Currently, most are identifying it as a generic trojan or downloader, rather than as an information stealer.
Files associated with this Trojan:
%UserProfile%\uninst.dllRegistry Keys Associated with this Trojan
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\igfxtray [\path\to\trojan.exe]Network Connections made by this Trojan
https://web4solution.net/external/updateIOCs:
SHA256: d6d64c61dada8b5ccfa970356057a6c2c7697f084922744c5a2e29aff079647b
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











