A new ransomware called DetoxCrypto has been discovered by MalwareHunterTeam that is currently being distributed under two different variants. The first variant looks like a generic ransomware but contains the interesting feature of taking a screenshot of your acting Windows screen when it is installed. The second variant is trying to take advantage of the immense popularity of PokemonGo, by hoping to trick people into installing it.
This ransomware appears to be either part of an affiliate system or being sold on darkweb sites as we are seeing different variants, with different themes, email addresses, and features. For example, one variant has a Pokemon theme, while another has a more generic ransom note, but takes a picture of your active Windows screen when it is installed.
All variants will encrypt your data using AES encryption, stop MySQL and MSSQL services, display a ransom note/lock screen, and play an audio file while the lock screen is showing. In order to pay the ransom, victims are instructed to contact an email listed in the lock screen for payment instructions.
Anatomy of the DetoxCrypto Ransomware
It is currently not known how this ransomware is distributed, but so far the variants we have observed all use a single distributed executable that contains other executables and files embedded within it. When the main distribution executable is run, it will extract a file called MicrosoftHost.exe, an audio file, a wallpaper background, and a third executable, whose name varies per variant of DetoxCrypto.
The MicrosoftHost.exe executable performs the actual encryption of the drive and stop the database servers on the victim’s computer. When encrypting files it will not append a different extension to it. It will also configure the Windows desktop background to use the embedded image file that is extracted.
The third file, which we have seen named Calipso.exe and Pokemon.exe, display the lock screen, play an audio file, and provide the ability to decrypt a victim’s file if the correct password is entered. This file appears is not static between each variant that we noticed, so it is possible that different distributors customize this file to perform their own desired tasks.
The two different variants we have seen so far is a Pokemon theme and a generic looking looking one, with an interesting screen capture routine. Both of these are described further below.
Calipso Variant
The Calipso variant of DetoxCrypto was discovered by Intel security researcher Marc Rivero López, When run it will extract numerous files to the C:\Users\[account_name]\Calipso folder as shown below.
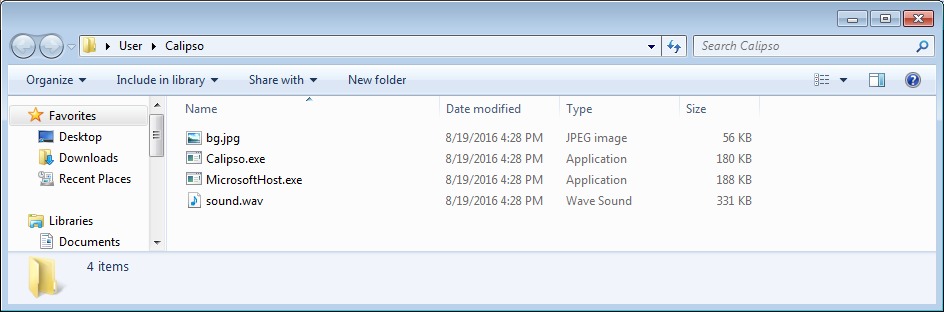
The ransomware will then encrypt the victim’s computer, display a lock screen, and play some music. The lock screen will instruct the victim to email motox2016@mail2tor.com in order to get payment instructions. A video of the lock screen and audio can be seen above.
When this ransomware is executed, it will also take a screenshot of the active screen and upload it to the developer.
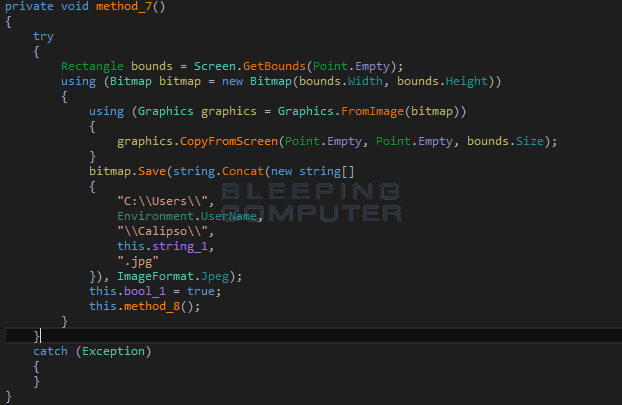
It is possible that based on what is contained in the screenshot, the ransomware developer may try to increase the price of the ransom if the image contains blackmail worthy content.
We are all Pokemons Variant

The Pokemon themed variant of DetoxCrypto is distributed as an executable called Pokemongo.exe. When executed the ransomware will extract numerous files to the C:\Users\[account_name]\Downloads\Pokemon folder as shown below.
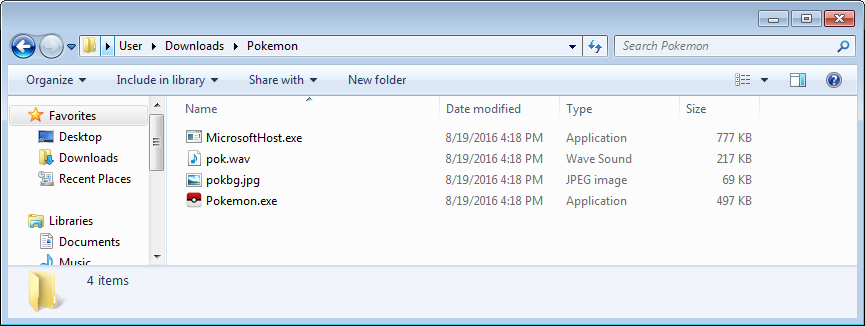
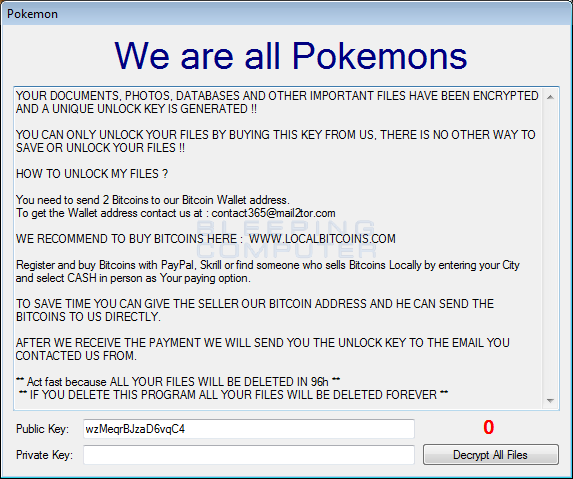
The ransomware will then encrypt the victim’s computer, display a lock screen, and play some music. The text of the lock screen is:
We are all Pokemons
YOUR DOCUMENTS, PHOTOS, DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED AND A UNIQUE UNLOCK KEY IS GENERATED !!
YOU CAN ONLY UNLOCK YOUR FILES BY BUYING THIS KEY FROM US, THERE IS NO OTHER WAY TO SAVE OR UNLOCK YOUR FILES !!
HOW TO UNLOCK MY FILES ?
You need to send 2 Bitcoins to our Bitcoin Wallet address.
To get the Wallet address contact us at : contact365@mail2tor.com
WE RECOMMEND TO BUY BITCOINS HERE : WWW.LOCALBITCOINS.COM
Register and buy Bitcoins with PayPal, Skrill or find someone who sells Bitcoins Locally by entering your City and select CASH in person as Your paying option.
TO SAVE TIME YOU CAN GIVE THE SELLER OUR BITCOIN ADDRESS AND HE CAN SEND THE BITCOINS TO US DIRECTLY.
AFTER WE RECEIVE THE PAYMENT WE WILL SEND YOU THE UNLOCK KEY TO THE EMAIL YOU CONTACTED US FROM.
** Act fast because ALL YOUR FILES WILL BE DELETED IN 96h **
** IF YOU DELETE THIS PROGRAM ALL YOUR FILES WILL BE DELETED FOREVER **The lock screen for this variant can be seen below.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











