A new ransomware called Alma Locker has been discovered by Proofpoint researcher Darien Huss that encrypts a victim’s data and then demands a ransom of 1 bitcoin within five days. There has been a lot of ransomware released lately, but thankfully most of them have been broken implementations or have had suspended command and control servers. Though Alma Locker still has some bugs in its implementation, it is one of the few released lately that has a working TOR command & control server and a secure encryption algorithm.
Unfortunately, at this time there are no known weaknesses in Alma Locker that can be exploited to decrypt a victim’s files for free. With that said, I and others will continue to look for weaknesses and if you have any questions or comments, feel free to post them in the Alma Locker Ransomware Help & Support Topic.
How Alma Locker Encrypts a Computer
The Alma Locker ransomware is currently being distributed via the RIG exploit kit. Once installed, Alma Locker will generate a random 5 character extension that will be appended to encrypted files and a unique 8 character vicitm ID. This victim ID is derived from the serial number of the C:\ drive and the MAC address of the first network interface.
Alma Locker will now search the victim’s drive letters for files with certain extensions and encrypt them using AES-128 encryption. When it encrypts a file it will append the previously generated extension to encrypted files. For example, if the extension associated with a victim is .a5zfn, then a file named test.jpg would be encrypted to a file named test.jpg.a5zfn.
The data files targeted by Alma Locker are:
.1cd, .3ds, .3gp, .accdb, .ape, .asp, .aspx, .bc6, .bc7, .bmp, .cdr, .cer, .cfg, .cfgx, .cpp, .cr2, .crt, .crw, .csr, .csv, .dbf, .dbx, .dcr, .dfx, .dib, .djvu, .doc, .docm, .docx, .dwg, .dwt, .dxf, .dxg, .eps, .htm, .html, .ibank, .indd, .jfif, .jpe, .jpeg, .jpg, .kdc, .kwm, .max, .mdb, .mdf, .odb, .odc, .odm, .odp, .ods, .odt, .orf, .p12, .p7b, .p7c, .pdf, .pef, .pem, .pfx, .php, .png, .pps, .ppt, .pptm, .pptx, .psd, .pst, .pub, .pwm, .qbb, .qbw, .raw, .rtf, .sln, .sql, .sqlite, .svg, .tif, .tiff, .txt, .vcf, .wallet, .wpd, .xls, .xlsm, .xlsx, .xml
While encrypting files, Alma Locker will skip files located in folders containing the following strings:
$recycle.bin
system volume information
program files
programdata
program files (x86)
windows
internet explorer
microsoft
mozilla
chrome
appdata
local settings
recycler
msocache
Unlock_files_
During the encryption process, Alma Locker will send the following base64 encoded information to the ransomware’s Command & Control server: AES-128 private decryption key, encrypted file extension, user name, name of active network interface, the system Locale ID (LCID), operating system version, victim ID, security software registered with Windows, and the time stamp of when the program was started.
When it has finished it will display a ransom note explaining what has happened to the victim’s files.
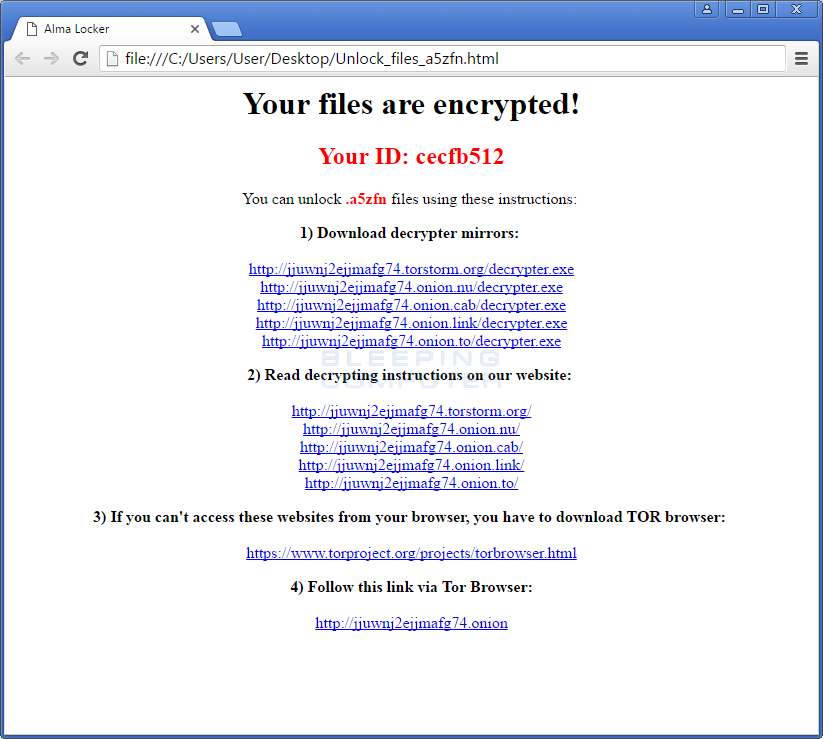
The ransom note contains links to the TOR payment site and a link to download a decryptor. When this decryptor is run, it will connect to the Command & Control server and retrieve information such as the current ransom amount, whether a payment has been received, and how many hours left in the five day countdown.
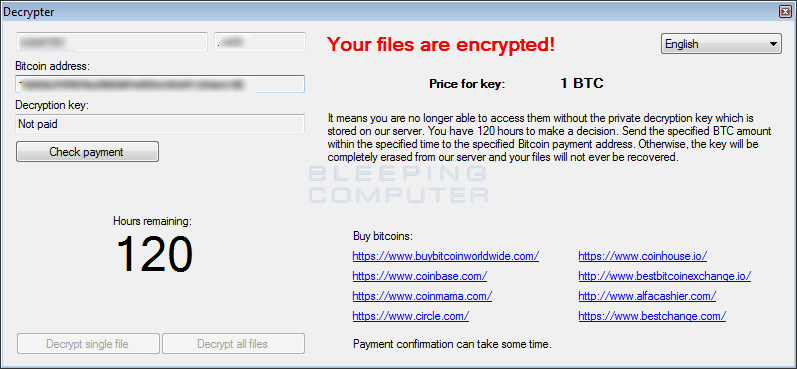
At this time it is unknown how much the ransom payment will increase once the initial 120 hour countdown has completed.
The Alma Locker Payment Site
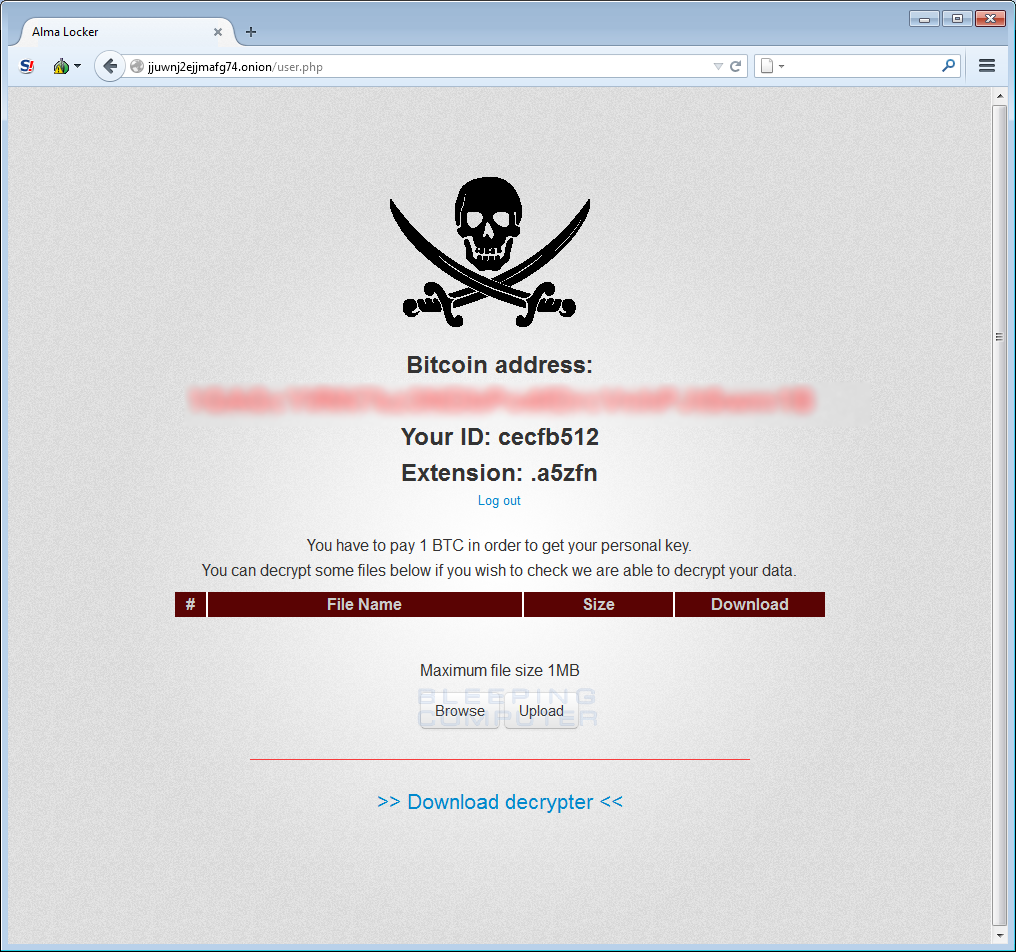
The ransom notes contain links to a TOR site where it states a victim can perform some test file decryptions to prove that they can decrypt your files.
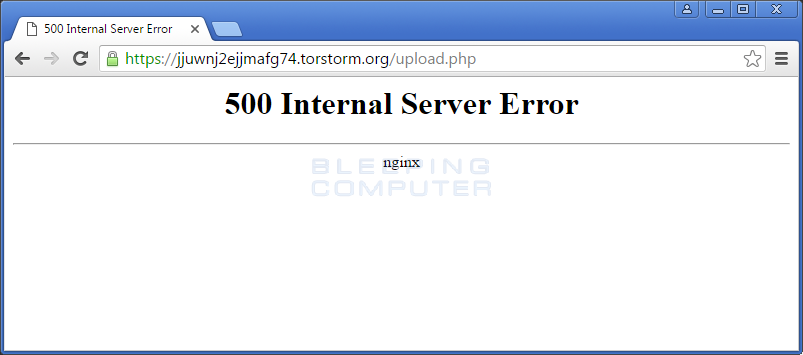
Unfortunately, it appears that this free decryption is currently not working as it only led to an internal server error as shown below.
Files associated with Alma Locker
Unlock_files_[random_extension].html
Unlock_files_[random_extension].txt
IOCs
Network: jjuwnj2ejjmafg74.onion
SHA256 Hashes: 11f2c3d0dbc00e65b90ab0b06dadf00a3d3ea4dc2fdbc9f3b4108c8e4e18a2ab
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











