A new DetoxCrypto Ransomware variant called the Nullbyte Ransomware has been discovered by Emsisoft security researched xXToffeeXx that pretends to be the popular Pokemon Go bot application called NecroBot, When infected, the ransomware will encrypt a victim’s files and then demand .1 bitcoins to decrypt the files. Thankfully, Michael Gillespie was able to create decryptor so that victims can get their files back for free.
This ransomware is distributed from a Github project that pretends to be a rebuilt version of the NecroBot application in the hopes that people will download it thinking it was the legitimate application.
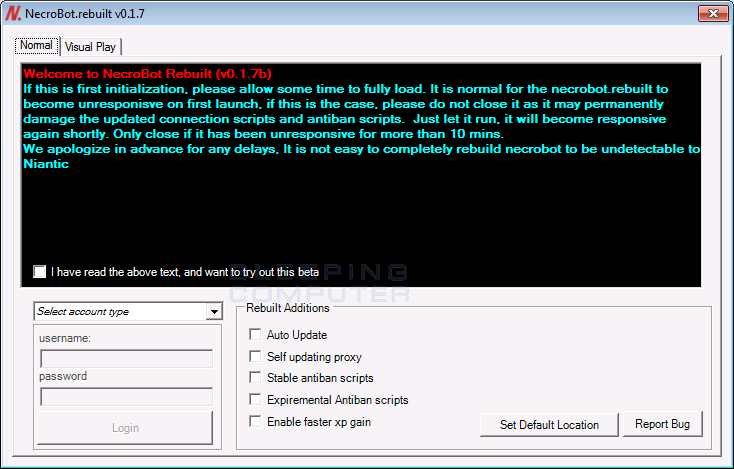
When someone downloads and executes the application it will show the standard NecroBot interface asking for the victim to login.
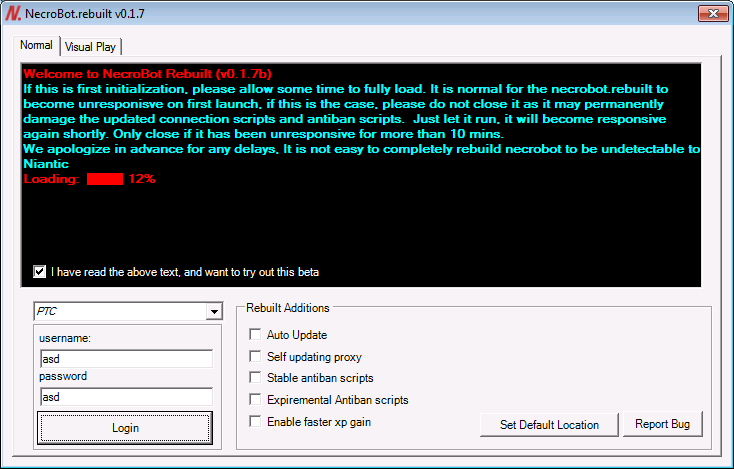
If any login info, real or fake, is entered and the Login button is pressed, the program wil pretend to try and login to the NecroBot servers. In the background, though, the ransomware will steal the entered credentials by uploading them to the command and control server and then begin to encrypt a victim’s files.
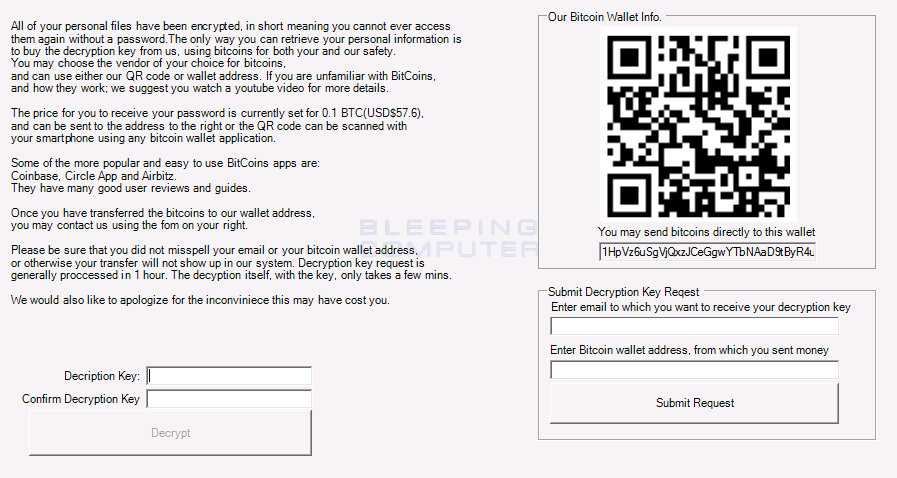
When finished, the ransomware will display its lock screen that prompts a user to pay .1 bitcoins to decrypt the files.
The Nullbyte Ransomware Encryption Process
According to further analysis by MalwareHunterTeam, the Nullbyte ransomware will encrypt files using AES encryption and then append the _nullbyte extension to encrypted files. For example, test.jpg would become test.jpg_nullbyte when the file is encrypted.
When encrypting files, the Nullbyte ransomware will encrypt any file located in the following folder:
%USERPROFILE%\Documents
%USERPROFILE%\Downloads
%USERPROFILE%\Favorites
%USERPROFILE%\Pictures
%USERPROFILE%\Music
%USERPROFILE%\Videos
%USERPROFILE%\Contacts
%USERPROFILE%\DesktopWhile running, this ransomware will also terminate the chrome, cmd, taskmgr, firefox, iexplore, and opera processes, This is done to make it difficult to remove the ransomware or search for help on the web.
Last, but not least, the ransomware will generate a screenshot of the currently active Windows screens and upload it to the ransomware’s command & control server. At this time, it is unknown how the screenshot is used, but it could be used for possible information theft or blackmailing.
Decrypting the Nullbyte Ransomware
Thankfully, Michael Gillespie was able to create a decryptor for the Nullbyte Ransomware. Instructions on how how to use the decryptor can be found in the Nullbyte Ransomware Help and Support Topic.
Below is a screenshot of the decryptor decrypting files encrypted by this ransomware.
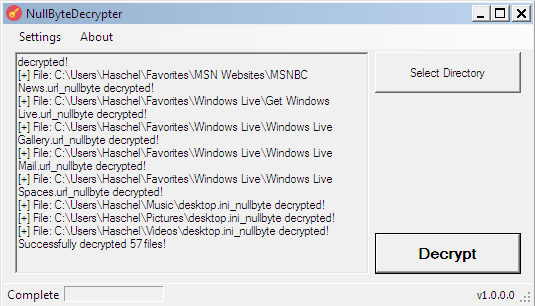
Files associated with the Nullbyte Ransomware
%UserProfile%\Desktop\DecryptInfo.exe
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost32.exe
%UserProfile%\Documents\bg.jpg
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DecryptInfo.exe
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\enhost32.exeIOCs:
SHA256: 96992b32a1bd469dfb778d8d2d1a24dbc41d5adc11d05efa659e6c85de0f50adNetwork Traffic:
https://tools.feron.it/php/ip.php
ftp://ftp.taylorchensportfolio.netai.net/DECRYPTINFO-LAUNCHED
ftp://ftp.taylorchensportfolio.netai.net/DECRYPT-REQUEST
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











