A new ransomware that pretends to be from a fake organization called the Central Security Treatment Organization has been discovered by security researcher MalwareHunterTeam. When the Central Security Treatment Organization, or Cry, Ransomware infects a computer it will encrypt a victim’s files and then append the .cry extension to encrypted files. It will then demand approximately 1.1 bitcoins, or $625 USD, in order to get the decryption key.
Based on analysis by myself, MalwareHunterTeam, and Daniel Gallagher, this infection exhibits some interesting characteristics not commonly seen in ransomware. For example, like Cerber, this ransomware will send information about the victim to the Command & Control server using UDP. Furthermore, it will also use public sites such as Imgur.com and Pastee.org to host information about each of the victims. Last, but not least, it will query the Google Maps API to determine the victim’s location using nearby wireless SSIDs.
This ransomware is still currently being analyzed and it may be discovered that decryption is possible. Therefore, victims may want to monitor the Central Security Treatment Organization Support Topic for updates.
As with many ransomware infections, it is hard to provide a descriptive name, so for the purposes of this article the ransomware will be referred to as the Central Security Treatment Organization Ransomware, CSTO Ransomware, or Cry Ransomware.
Command & Control Server Communication Methods
When a victim is infected, the ransomware will compile a variety of information such as the Windows version, the service pack installed, the Windows bit-type, the user name, the computer name, and the type of CPU installed in the computer. This information will then be sent via UDP to 4096 different IP addresses, with one of them being the ransomware’s Command & Control server. The use of UDP packets is probably being done to obfuscate the location of the Command & Control server so that authorities cannot seize it.
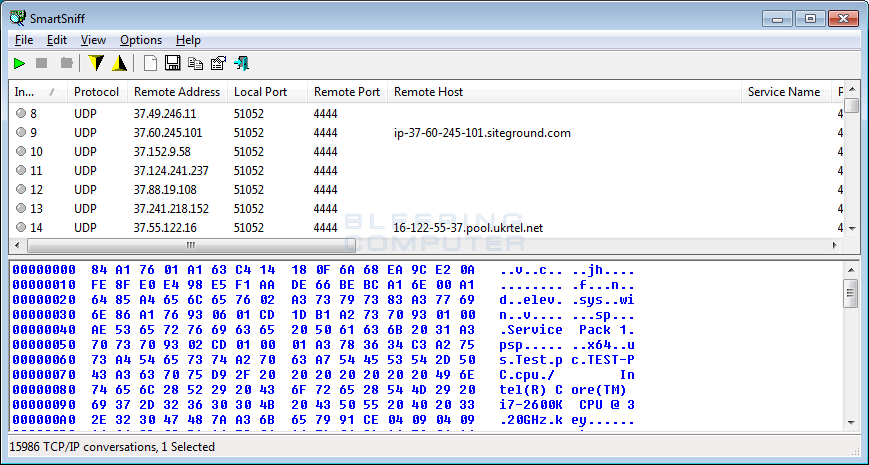
The Cry Ransomware will also upload the same information as well as a list of encrypted files to Imgur.com. It does this by compiling all of the information into a fake PNG image file and then uploading it to a designated Imgur album. Once the file has successfully been uploaded, Imgur will respond with a unique name for the filename. This filename then be broadcasted over UDP to the 4096 IP addresses to notify the Command & Control server that a new victim has been infected.
Finding a victim’s location based on nearby SSIDs
Using the Google Maps API, a user can determine the location of a querying device by the SSIDs of nearby wireless networks. This ransomware uses the WlanGetNetworkBssList function to get a list of nearby wireless networks and their SSIDs. It will then query the Google Maps API using these SSIDs to get the victim’s location.
It is unsure what this is currently being used for, but this information could be used to generate an image of the victim’s location using Google maps. This could then be used to further scare the victims into paying the ransom.
How the Central Security Treatment Organization Ransomware Encrypts Files
When this ransomware infects a computer it make a backup of certain shortcuts on the victim’s Windows desktop and save them in a folder on the desktop called old_shortcuts. The purpose of this folder is currently unknown.
The ransomware will now encrypt the victim’s files and append the .cry extension to encrypted files. The files currently targeted by this ransomware are:
.#vc, .$ac, .00c, .07g, .07i, .08i, .09i, .09t, .1pa, .1pe, .3dm, .3ds, .3g2, .3gp, .3me, .3pe, .7z, .10t, .11t, .13t, .123, .210, .500, .2011, .2012, .2013, .2014, .2015, .2016, .2017, .aac, .aaf, .ab4, .ac2, .acc, .accd, .ach, .aci, .acm, .acr, .aep, .aepx, .aes, .aet, .afm, .ai, .aif, .amj, .arc, .as, .as3, .asc, .asf, .asm, .asp, .asx, .ati, .avi, .back, .bak, .bat, .bay, .bc8, .bc9, .bd2, .bd3, .bgt, .bk2, .bmp, .bpf, .bpw, .brd, .brw, .btif, .bz2, .c, .cal, .cat, .cb, .cd, .cdf, .cdr, .cdt, .cdx, .cf8, .cf9, .cfdi, .cfp, .cgm, .cgn, .ch, .chg, .cht, .clas, .clk, .cmd, .cmx, .cnt, .cntk, .coa, .cpp, .cpt, .cpw, .cpx, .crt, .cs, .csl, .csr, .css, .csv, .cur, .cus, .d07, .dac,.dat, .db, .dbf, .dch, .dcr, .ddd, .dds, .defx, .der, .des, .dgc, .dif, .dip, .djv, .djvu, .dng, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .drw, .ds4, .dsb, .dsf, .dtau, .dtd, .dtl, .dwg, .dxf, .dxi, .ebc, .ebd, .ebq, .ec8, .efs, .efsl, .efx, .emd, .eml, .emp, .ens, .ent, .epa, .epb, .eps, .eqb, .ert, .esk, .ess, .esv, .etq, .ets, .exp, .fa1, .fa2, .fca, .fcpa, .fcpr, .fcr, .fef, .ffd, .fim, .fla, .flac, .flv, .fmv, .fon, .fpx, .frm, .fx0, .fx1, .fxr, .fxw, .fyc, .gdb, .gem, .gfi, .gif, .gnc, .gpc, .gpg, .gsb, .gto, .gz, .h, .h10, .h11, .h12, .hbk, .hif, .hpp, .hsr, .html, .hts, .hwp, .i2b, .iban, .ibd, .ico, .idml, .iff, .iif, .img, .imp, .indb, .indd, .indl, .indt, .ini, .int?, .intu, .inv, .inx, .ipe, .ipg, .itf, .jar, .java, .jng, .jp2, .jpeg, .jpg, .js, .jsd, .jsda, .jsp, .kb7, .kd3, .kdc, .key, .kmo, .kmy, .lay, .lay6, .lcd, .ldc, .ldf, .ldr, .let, .lgb, .lhr, .lid, .lin, .lld, .lmr, .log, .lua, .lz, .m, .m3u, .m3u8, .m4a, .m4u, .m4v, .m10, .m11, .m12, .m14, .m15, .m16, .mac, .max, .mbsb, .md, .mda, .mdb, .mdf, .mef, .mem, .met, .meta, .mhtm, .mid, .mkv, .ml2, .ml9, .mlb, .mlc, .mmb, .mml, .mmw, .mn1, .mn2, .mn3, .mn4, .mn5, .mn6, .mn7, .mn8, .mn9, .mne, .mnp, .mny, .mone, .mov, .mp2, .mp3, .mp4, .mpa, .mpe, .mpeg, .mpg, .mql, .mrq, .ms11, .msg, .mwi, .mws, .mx0, .myd, .mye, .myi, .myox, .n43, .nap, .nd, .nef, .nl2, .nni, .npc, .nv, .nv2, .oab, .obi, .odb, .odc, .odg, .odm, .odp, .ods, .odt, .oet, .ofc, .ofx, .old, .omf, .op, .orf, .ost, .otg, .otp, .ots, .ott, .p08, .p7b, .p7c, .p12, .paq, .pas, .pat, .pcd, .pcif, .pct, .pcx, .pd6, .pdb, .pdd, .pdf, .pem, .per, .pfb, .pfd, .pfx, .pg, .php, .pic, .pl, .plb, .pls, .plt, .pma, .pmd, .png, .pns, .por, .pot, .potm, .potx, .pp4, .pp5, .ppam, .ppf, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .pr0, .pr1, .pr2, .pr3, .pr4, .pr5, .prel, .prf, .prn, .prpr, .ps, .psd, .psp, .pst, .ptb, .ptdb, .ptk, .ptx, .pvc, .pxa, .py, .q00, .q01, .q06, .q07, .q08, .q09, .q43, .q98, .qb1, .qb20, .qba, .qbb, .qbi, .qbk, .qbm, .qbmb, .qbmd, .qbo, .qbp, .qbr, .qbw, .qbx, .qby, .qbz, .qch, .qcow, .qdf, .qdfx, .qdt, .qel, .qem, .qfi, .qfx, .qif, .qix, .qme, .qml, .qmt, .qmtf, .qnx, .qob, .qpb, .qpd, .qpg, .qph, .qpi, .qsd, .qsm, .qss, .qst, .qtx, .quic, .quo, .qw5, .qwc, .qwmo, .qxf, .r3d, .ra, .raf, .rar, .raw, .rb, .rcs, .rda, .rdy, .reb, .rec, .resx, .rif, .rm, .rpf, .rss, .rtf, .rtp, .rw2, .rwl, .rz, .s7z, .s12, .saf, .saj, .say, .sba, .sbc, .sbd, .sbf, .scd, .sch, .sct, .sdf, .sdy, .seam, .ses, .set, .shw, .sic, .skg, .sldm, .sldx, .slk, .slp, .sql, .sqli, .sr2, .srf, .ssg, .stc, .std, .sti, .stm, .str, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .t00, .t01, .t02, .t03, .t04, .t05, .t06, .t07, .t08, .t09, .t10, .t11, .t12, .t13, .t14, .t15, .t99, .ta1, .ta2, .ta4, .ta5, .ta6, .ta8, .ta9, .tar, .tax, .tax0, .tax1, .tax2, .tb2, .tbk, .tbp, .tdr, .text, .tfx, .tga, .tgz, .tif, .tiff, .tkr, .tlg, .tom, .tpl, .trm, .trn, .tt10, .tt11, .tt12, .tt13, .tt14, .tt15, .tt20, .ttf, .txf, .txt, .u08, .u10, .u11, .u12, .uop, .uot, .v30, .vb, .vbpf, .vbs, .vcf, .vdf, .vdi, .vmb, .vmdk, .vmx, .vnd, .vob, .vsd, .vyp, .vyr, .wac, .wav, .wb2, .wi, .wk1, .wk3, .wk4, .wks, .wma, .wmf, .wmv, .wpd, .wpg, .wps, .x3f, .xaa, .xcf, .xeq, .xhtm, .xla, .xlam, .xlc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xpm, .xqx, .yuv, .zdb, .zip, .zipx, .zix, .zka, ._vcDuring this process it will also delete the system’s Shadow Volume Copies using the command:
vssadmin delete shadows /all /quietIn order to provide persistence, the ransomware will create a random named scheduled task that will trigger when the user logs into Windows.
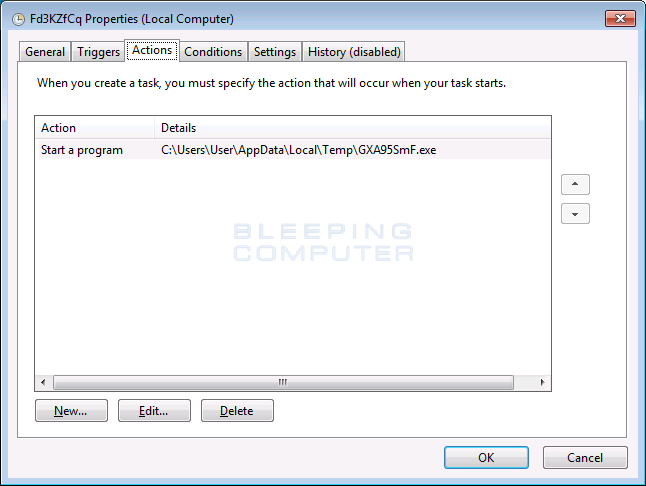
Finally, the ransomware will create ransom notes named !Recovery_[random_chars].htmland !Recovery_[random_chars].txt on the victim’s desktop.
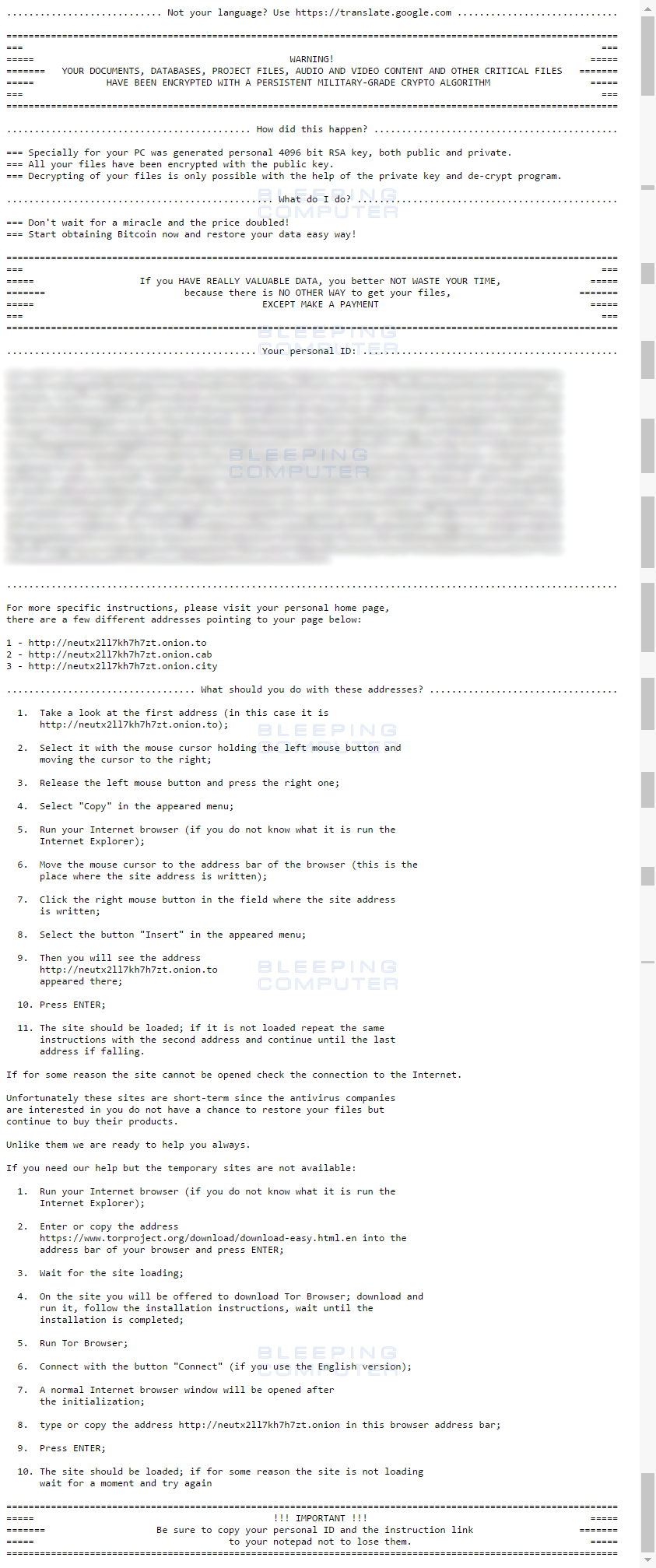
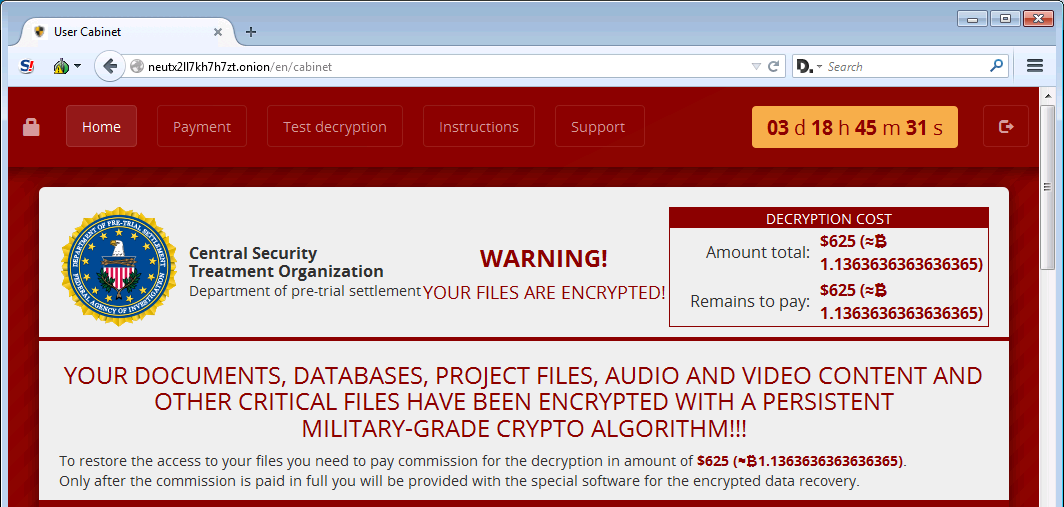
This ransom note will contain the victim’s personal ID and instructions on how to access the TOR payment site as shown above. Information about this Payment site can be found Central Security Treatment Organization’s payment site can be found in the next section.
The Central Security Treatment Organization Ransomware’s TOR Payment Site
The ransom notes created by the Central Security Treatment Organization Ransomware contain links to a TOR payment site that has a Window title of User Cabinet. When a user visits this site, they will be prompted to login using the personal code from their ransom note.
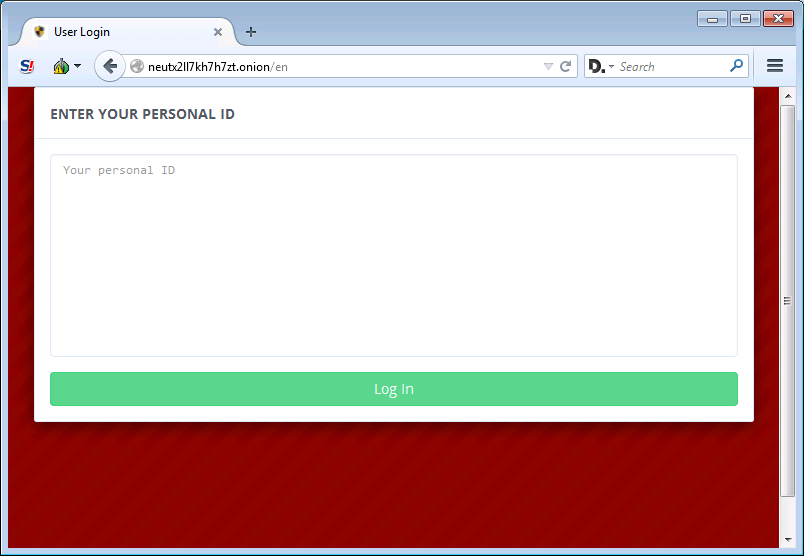
Once a victim logs in, they will be shown a page that states that it is part of some fake organization called the Central Security Treatment Organization and will contain the ransom amount that a victim must pay.
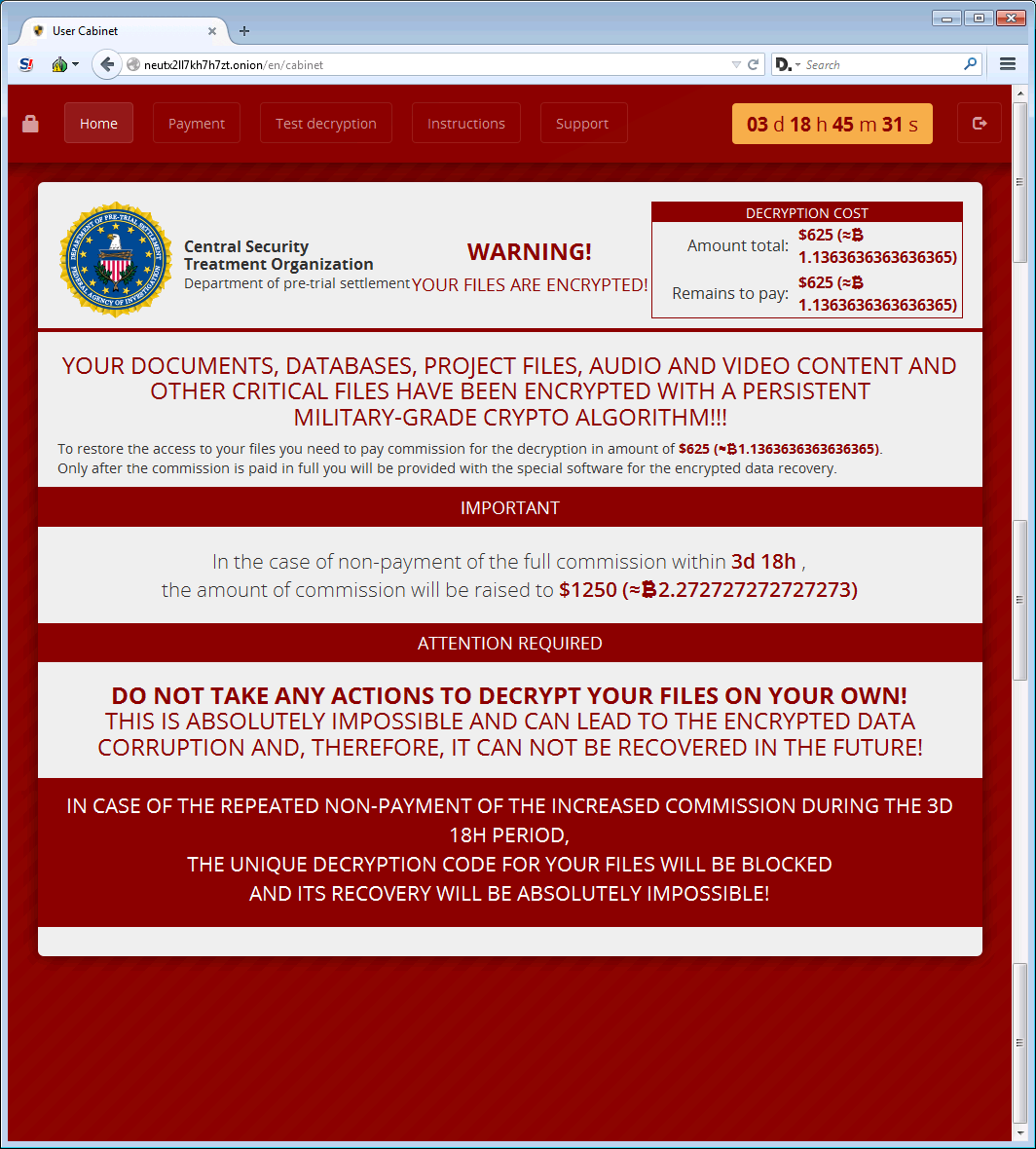
Other sections on the site include a payment page that lists the bitcoin address that the payment must be sent to. There is also a support page that a victim can use to communicate with the malware developers.
The payment site will also include a free decryption of one file to test that they can actually decrypt a victim’s files.
When a file is submitted to the free decryption, it will decode it while you wait.

In my tests, though, the free decryption failed and the decrypted file was not made available. With that said, if you do plan on paying the ransom, you may want to confirm that this feature works before doing so in order to test the decryption.
Files associated with the Central Security Treatment Organization Ransomware:
%UserProfile%\AppData\Local\Temp\[random_chars].exe
%UserProfile%\AppData\Local\Temp\[random_chars].tmp
%UserProfile%\AppData\Local\Temp\[random_chars].html
%UserProfile%\Desktop\!Recovery_[random_chars].html
%UserProfile%\Desktop\!Recovery_[random_chars].txt
%UserProfile%\Desktop\old_shortcuts\
C:\Windows\System32\Tasks\[random_chars]
Registry Entries associated with the Central Security Treatment Organization Ransomware:
HKCU\Software\[same_name_as_executable]IOCs:
SHA256: 33f66a95e01e2650ea47405031d4ced2ad25db971e65a92319296ccef62b7964Network Communication:
https://imgur.com
https://pastee.org/
https://maps.googleapis.com
UDP Traffic to ip addresses in the 37.x.x.x range
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











