The Dridex banking trojan might be involved in fewer attack campaigns, but its developers are still outfitting it with some new functionalities, including the ability to target crypto-currency wallets.
Nicholas Griffin, senior security researcher at Forcepoint, explains Dridex relies on two lists to target users’ banking credentials:
“These lists have gradually expanded over the months and years, and now include back-end payment and point-of-sale software, online banking software, and a recently added list of crypto-currency wallet managers.”
But that’s not all the latest version of the banking Trojan has to offer.
Dridex also collects several pieces of information from each infected computer and sends it to its command-and-control (C&C) server. That data includes the infected computer’s name, user name, OS installation date and version, and a list of installed software.
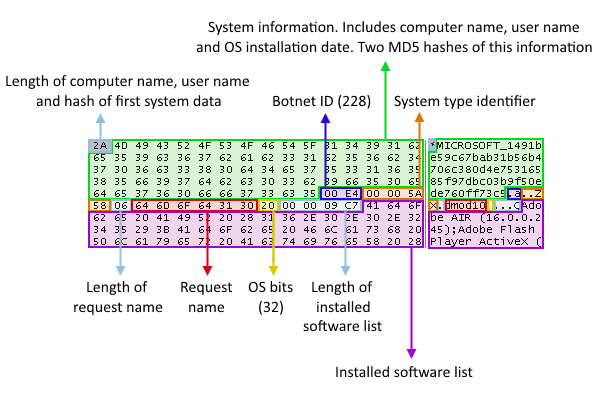
If that information passes a series of criteria, the C&C server responds with the malware payloads. If it doesn’t, it sends over a 403 HTTP error code. The C&C server can take it one step further and even blacklist a machine to prevent researchers from taking a look at the malware’s internals.
Finally, Dridex has moved to a multi-layered encrypted binary format to further complicate analysis.
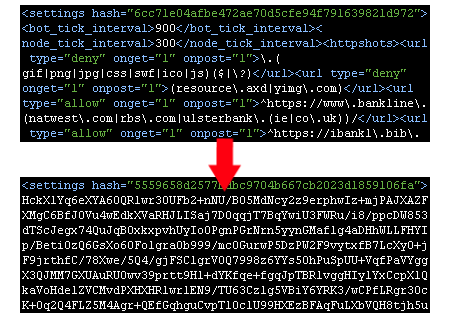
But as Griffin explains, that doesn’t prevent researchers from accessing the malware’s main configuration file:
“Despite the protections put in place by the Dridex developer(s), it is still very much possible to reconstruct the Dridex settings configuration file received by the core module. This configuration file includes the list of banking websites to capture data from and inject code into when infecting a user’s browser.”
For years, Dridex has been one of the most prolific banking trojans. That changed in October 2015, when the UK’s National Crime Agency partnered with the FBI and other security partners to sinkhole the malware.
At that point, Dridex slowed down, but didn’t cease, its activity. The banking trojan experienced aresurgence in the late-2015, only to decline once again after the Necurs botnet temporarily went offline. It’s currently still active, but its distributors have since begun using their infrastructure to spread Locky ransomware instead.
Given Dridex’s persistence, users should exercise caution around suspicious email attachments and URLs and disable Microsoft Office macros by default.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











