The Shark Ransomware Project that appeared in July 2016 has rebranded as the Atom Ransomware Affiliate Program, offering an improved service for crooks that want to start a life in cyber-crime.
We don’t know why the project rebranded, but there have been several reports from security vendors and various media publications that have broken down the project’s mode of operation and analyzed every facet of its service. Ransomware operators don’t like public exposure, so it might be safe to say that the Shark team, now Atom, is looking for a fresh start.
Just like Shark, the service is still available on the public Internet, which is strange because most of its rivals prefer the anonymity and safety provided by the Tor network.
The Atom homepage still runs on WordPress, but unlike its predecessor, hides its admin panel login much better. Nevertheless, if you look at the site’s homepage, you still find traces of the Ninja Forms WordPress plugin code.

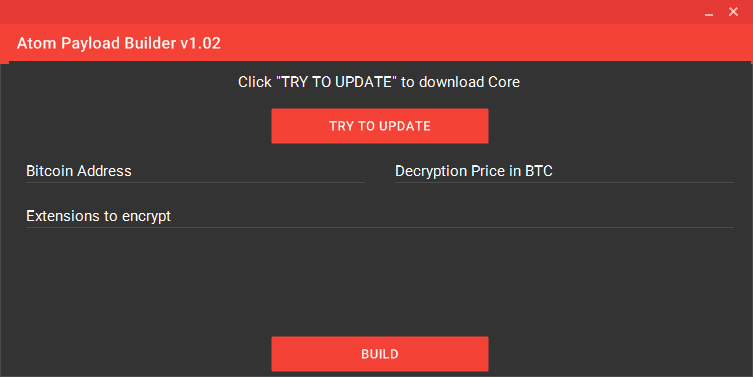
The biggest change between Atom and Shark is the new Atom Payload Builder, a downloadable EXE that allows crooks to compile their customized version of the Atom ransomware.
The main difference between the Atom builder and the old Shark one is that it generates a fully working payload executable, rather just a configuration code that was used as an argument to the Shark exe file. This greatly reduces the complexity of getting a ransomware build up and running for a distributor.
At the time of writing, the builder is at version 1.02, and features three options: a Bitcoin address where the user wants to receive his cut from the profits, the ransom demand fee (in Bitcoin), and the list of file extensions that should be targeted for encryption.
After users compile their own version of the ransomware, they are free to decide on the distribution method they wish to use. Options include exploit kits, email spam, IM spam, and others. Atom devs don’t provide any clues or hints as to how the payload should be distributed, but rather leave it up to their affiliates.
What they provide is a unique ransomware affiliate ID that is hardcoded inside their version of the Atom ransomware. The ID is sent to the Atom RaaS master server with each infection and allows the Atom team to track infections across different users.
Using this tracking code, an affiliate can view data about their installs inside a web panel that they can access from the Atom homepage. This panel shows the number of victims infected by an Atom variant with that particular ID, how many of the victims paid, and what amount of money the crook has earned.
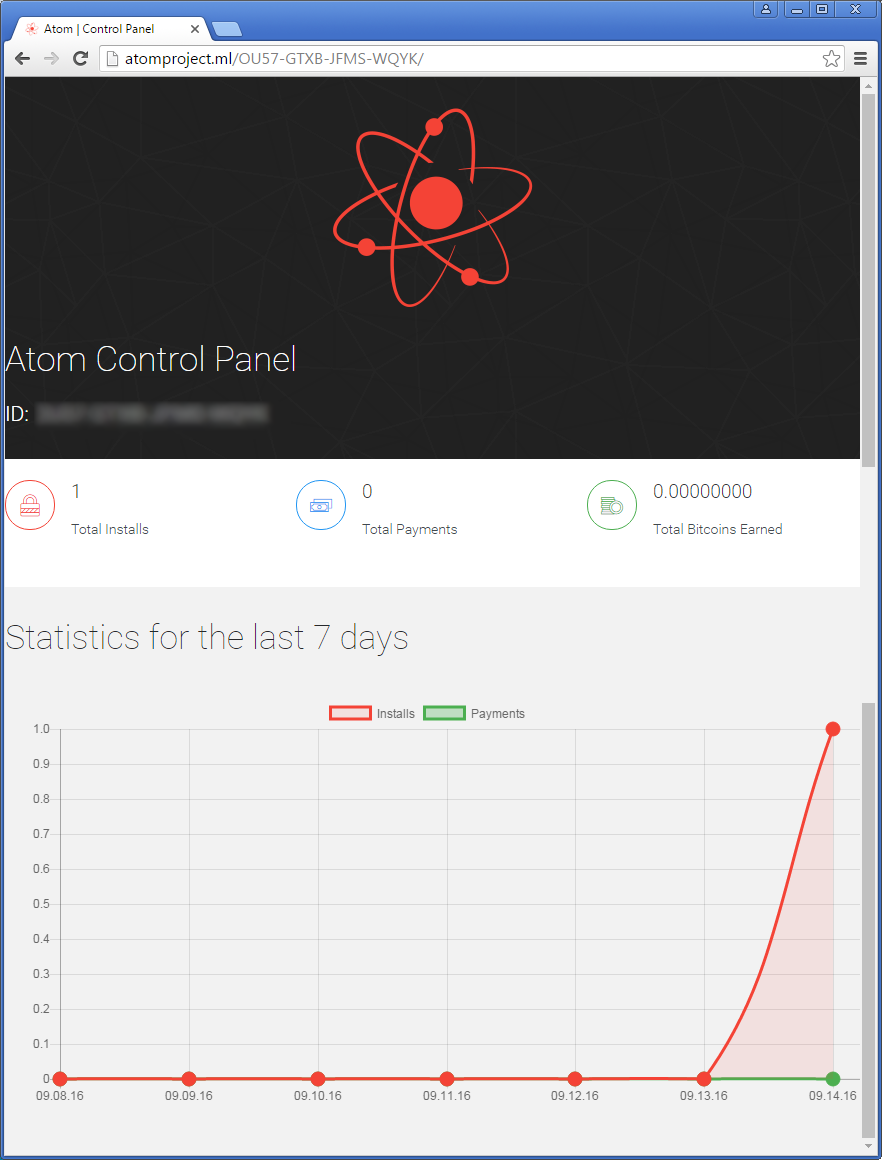
Just like Shark, the Atom team requires a 20 percent cut from the ransom demand each victim pays. There is no guarantee that people entering this informal business agreement with the Atom team would ever receive their money. All Atom ransom payments are actually sent to the Bitcoin wallet controlled by the Atom team, which then “promises” to redirect money to its users.
There is no honor among ransomware operators, as it was recently proven by the operator of the Petya and Mischa ransomware, who leaked the decryption keys for one of his rivals that ran the Chimera RaaS project.
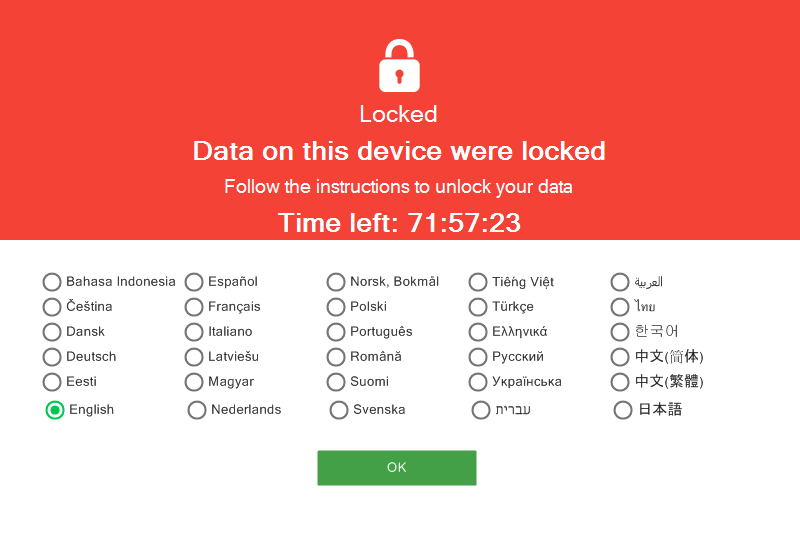
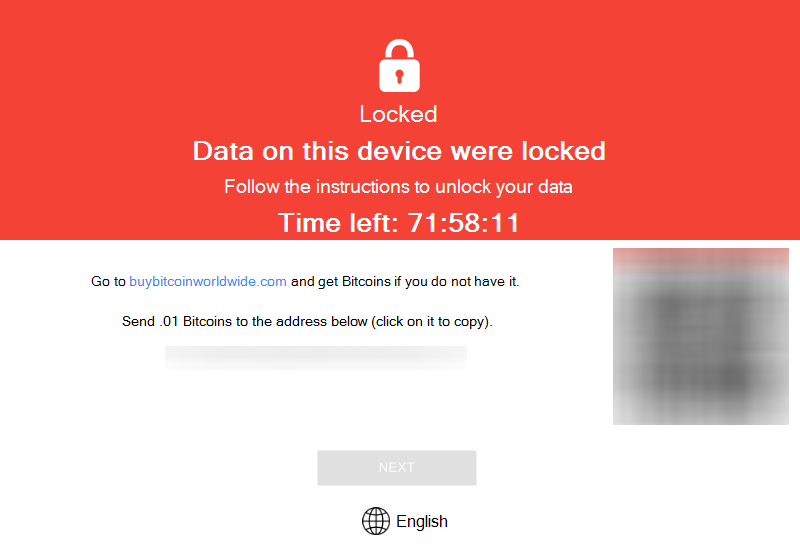
When an Atom ransomware infection takes hold, the ransomware starts an EXE file which doubles as the ransom note and the ransomware decrypter.
The ransomware locks the user’s files via the AES-256 algorithm and uses HTTPS to send the decryption key and a unique victim ID to the RaaS C&C servers.
This initial beacon also includes the settings customized by each RaaS user, such as the ransomware campaign ID, the ransom decryption fee, and the crook’s Bitcoin address.
Though the Atom service offers a professional looking web site, its focus seems to be the availability of its service to as many crooks as possible. This may explain why its operators chose to host their website on the public Internet and not on the Dark Web. This may leave the door open for potential bugs in the ransomware code that may allow security researchers to crack Atom in the near future.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











