Unlock92 infections going under the radar. A ransomware variant that appeared in early July this year and was initially cracked and decrypted has quietly resurfaced in mid-August and has been spamming users ever since, with a determination seen only in the market’s top ransomware families.
Known as Unlock92, this ransomware was in the media’s attention for a hot second, the time security researchers needed to crack its encryption algorithm and release a free decrypter to help victims recover their files.
While the vast majority of ransomware coders would give up on their code by this point, the Unlock92 team has continued to work on their craft, and returned with new versions, with much stronger encryption, which the free decrypter couldn’t handle.
First (weak) versions of Unlock92 seem to have been an accident
If we look at the big picture, the first Unlock92 version, the one that used weak encryption, seemed to be a fluke. The same gang behind Unlock92 had previously created the Kozy.Jozy ransomware, which used a strong RSA-2048 encryption system to lock the user’s files.
This same RSA-2048 system was later ported to current Unlock92 versions after researchers cracked the first variant. It looks like the first Unlock92 versions were only a test, and used a weaker encryption by accident, or intentionally, with the group fully capable of deploying a much stronger data encryption system at will.
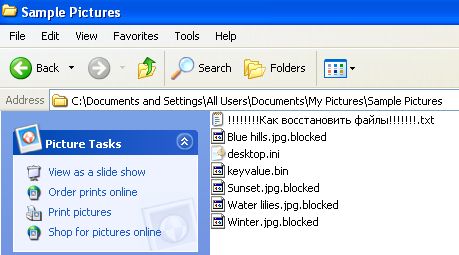
You can easily recognize the first Unlock92 versions based on the CRRRT extension it adds at the end of all encrypted files. The latter variants, the ones that can’t be decrypted, use the LOCKED or CCCRRRPPP extensions.
MalwareHunterTeam, an independent security researcher that has been keeping an eye on this ransomware since it came out, says the group behind this ransomware is very active, releasing new versions on a regular basis.
“They are very active. Every 1-2 days there’s a new sample,” he said. “The actor(s) behind this have not given up after a few samples like most of skids.”
“Actually, if you don’t count the big ones like Locky, Cerber, CryptXXX, and the ransomware kits, you won’t find much ransomware projects which keep going for months like this,” MalwareHunterTeam added.
Unlock92 targets only Russian-speaking users
The researcher is not the only one that has seen a rise in activity from this ransomware. The Dell Sonicwall Threat Research team has also detected a spike in the number of Unlock92 detections, for which it issued an alert on September 9.
The good news, or good for some of our readers, is that Unlock92 currently targets only Russian-speaking users.
Ransom notes are all available in Russian only. This includes all the TXT files Unlock92 leaves on infected computers, the user’s Desktop and his Start Menu. A rough translation of the Unlock92 ransom note is as follows:
“ Your files are encrypted with RSA- 2048 algorithm cryptographically . If you want to recover them, send one of the encrypted files and keyvalue.bin file to the e-mail address: unlock92@india.com If you do not receive a reply within 24 hours, then download the TOR browser from www.torproject.com and visit the following website: hxxp://ezxxxxxxxxxxxxxx.onion – the most current email address will be listed there. It is not possible to visit this website without a TOR browser. Attempts to self-recover files may irreversibly damage them! ”
Since there isn’t any geo-targeting filters in Unlock92’s source code, the group behind this threat appears to be using email address batches belonging to Russian users to target their victims. It would take very little effort for the group to translate the ransom notes to English and start targeting users all over the world, without any modification to the ransomware’s source code.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











