The Exotic Ransomware is a new infection released by a malware developer going by the alias of EvilTwin or Exotic Squad. Discovered on October 12th by MalwareHunterTeam, the Exotic Ransomware will encrypt all files, including executables, in targeted folders on a victim’s computer. When finished it will display a Jigsaw Ransomware-like ransom note that demands $50 USD to decrypt the files.
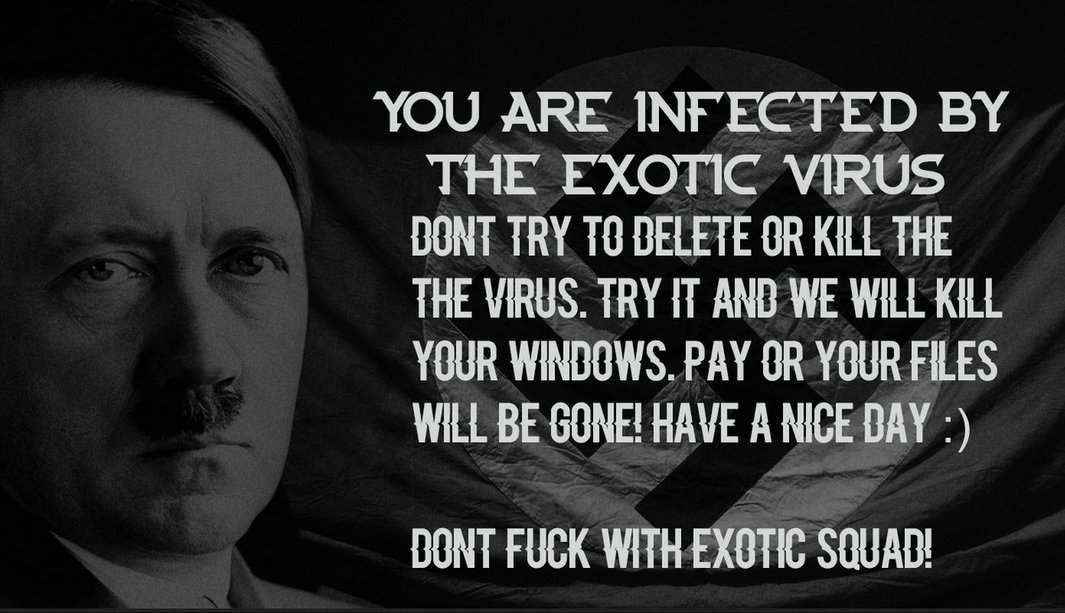
In general, there is nothing particularly innovative about this ransomware, but it does contain an annoying feature. This is the constant encryption of new files in the targeted folders, which is described in the next section.
Constant checking for new files kills CPU
Most ransomware typically are installed, perform an encryption of the targeted file types, and then uninstall itself. It is uncommon, if not rare, for a ransomware to continue running and encrypt new files as they are created.
Exotic, on the other hand, does exactly that. While running, it will constantly look for new files to encrypt in the targeted folders and encrypt them when discovered. It does this by constantly looping through the various folders and simply encrypting any targeted files that are not encrypted. This, though, utilizes a lot of CPU and thrashes the hard drive, making the computer almost unusable.
The Exotic Ransomware Encryption Process
Thanks to MalwareHunterTeam, I was able to get a copy of the source code for the Exotic Ransomware to see exactly how it works. When the ransomware starts it will scan certain folders for files that have specific extensions. When it encounters a targeted file extension, it will encrypt the file using AES-128 encryption, rename the file, and append the .exotic extension to them. For example, a file called test.jpg could be encrypted as the file name 87as.exotic.
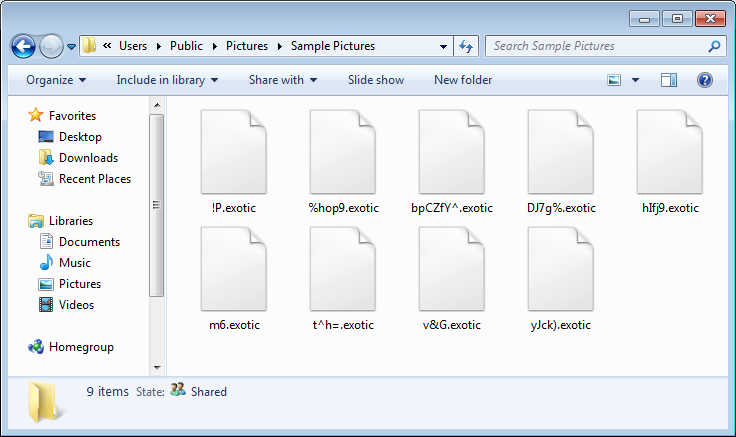
As previously mentioned, when Exotic encrypts a computer it is currently only targeting specific folders. These folders are:
%UserProfile%\Desktop
%UserProfile%\MyMusic
%UserProfile%\Personal
%UserProfile%\MyVideos
%UserProfile%\Contacts\
%UserProfile%\Downloads\
%UserProfile%\MyPictures
/vmware-host/
%UserProfile%
The file types that Exotic will encrypt are:
.txt .exe .text .cur .contact .ani .xls .com .url .ppt .src .cmd .tgz .fon .pl .lib .load .CompositeFont .png .exe .mp3 .mkv .veg .mp4 .lnk .zip .rar .7z .jpg .sln .crdownload .msi .vb .vbs .vbt .config .settings .resx .vbproj .json .jpeg .scss .css .html .hta .ttc .ttf .eot .camproj .m4r .001 .002 .003 .004 .005 .006 .007 .008 .009 .au .aex .8be .8bf .8bi .abr .adf .apk .ai .asd .bin .bat .gif .3dm .3g2 .exe .3gp .aaf .accdb .aep .aepx .aet .ai .aif .arw .as .as3 .asf .asp .asx .avi .bay .bmp .cdr .cer .class .cpp .contact .cr2 .crt .crw .cs .csv .dll .db .dbf .dcr .der .dng .doc .docb .docm .docx .dot .dotm .dotx .dwg .dxf .dxg .efx .eps .erf .fla .flv .iso .idml .iff .ini .sik .indb .indd .indl .indt .ico .inx .jar .jnt .jnt .java .key .kdc .m3u .m3u8 .m4u .max .mdb .mdf .mef .mid .mov .mpa .mpeg .mpg .mrw .msg .nef .nrw .odb .odc .odm .odp .ods .odt .orf .p12 .p7b .p7c .pdb .pdf .pef .pem .pfx .php .plb .pmd .pot .potm .potx .ppam .ppj .pps .ppsm .ppsx .ppt .pptm .pptx .prel .prproj .ps .psd .pst .ptx .r3d .ra .raf .raw .rb .rtf .rw2 .rwl .sdf .sldm .sldx .sql .sr2 .srf .srw .svg .swf .tif .vcf .vob .wav .wb2 .wma .wmv .wpd .wps .x3f .xla .xlam .xlk .xll .xlm .xls .xlsb .xlsm .xlsx .xlt .xltm .xltx .xlw .xml .xqx
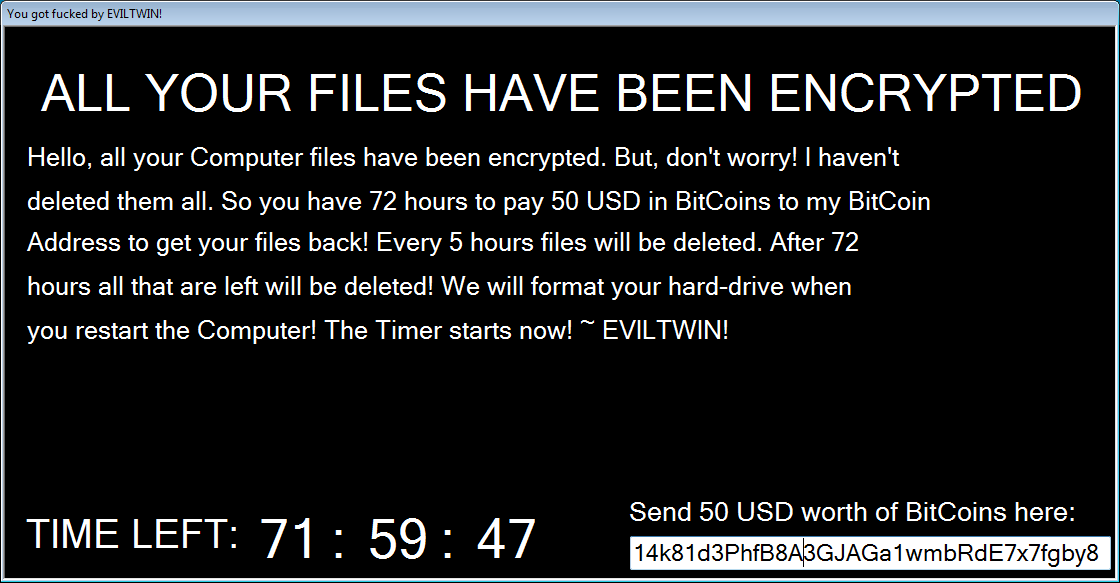
The ransomware will then download a background image for the lock screen from https://mitteoderso.de/image.png and save it into the %Temp% folder. The ransomware will then display the lock screen as shown in the video above and the image below.
While the program is running it will look for certain processes and terminate them if found. The processes terminated by Exotic are:
taskmgr
cmd
procexp
procexp64
regedit
CCleaner64
msconfig
Finally, the ransomware will continue to monitor the folders listed above for new unencrypted files and encrypt them. When the timer reaches 0, Exotic will shutdown the computer.
The ransomware will also copy itself to the%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.exe file, but will just become encrypted by the ransomware. Therefore, on reboot the ransomware will no longer be active.
As already stated, this ransomware appears to be currently in development mode, so you should not be seeing it in the wild as of yet. If anyone does encounter it, please let us know in the comments.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











