Recently a massive DDoS attack has disconnected a large portion of users from the Internet, hackers exploited IoT devices. Is your router secure?
“Are we ready to live in a world where all devices are exposed to cyber attacks?”
That is how I opened my presentation in QurtubaCON16 – cyber security event at Córdoba City (Spain) – and how I will open the next event: HoneyCON16 (Guadalajara, Spain) at November 11th. My intention is that every person takes their own conclusions about the risks that everybody assumes every time we connect our devices to the internet.
Have you ever wondered happens in your home router and that threats lurk in the moment you press the power button?
In this article, I intend to analyze the attacks and the cybersecurity events I have received in my personal router in Spanish ISP. This information may lead you to become aware of the high risk of having these devices connected to the web, even when we expose our lives on social media.
I have exposed my personal router to possible attacks because home routers haven’t been receiving the appropriate attention and, in some cases, people use to let them on during the entire year. People use to let these devices completely exposed and they don’t realize that sometimes administrator control panel is vulnerable and they are vulnerable to certain attacks or have different security flaws that have not been patched or by our Internet provider or by the device manufacturer.
We recommend you to visiting https://routersecurity.org/ to find more information about bugs and detected vulnerabilities in the last years to home routers and some recommendations.

In recent years, there has been news about vulnerabilities in routers distributed in Spain that show the seriousness of the matter:
- https://www.hackplayers.com/2015/02/250k-routers-de-telefonica-mismas-clav es-ssh.html
- https://www.muycomputer.com/2015/03/20/700-000-routers-adsl-isp-vulnerable s
- https://www.redeszone.net/2015/01/06/los-routers-de-movistar-adb-pirelli-p-dg a4001n-tienen-un-grave-fallo-de-seguridad/
- https://www.pcworld.es/seguridad/un-estudio-espanol-descubre-60-vulnerabilid ades-en-22-modelos-de-routers
What if an attacker gains access to the DNS settings of your router and modifies it?
It is not just about losing our privacy (because a cybercriminal could monitor your internet navigation); it is about letting an attacker to theft your identity, for example, in your personal bank or company website to obtain your credentials. This is just an example of what could really happen.

In many cases, the received attacks are automatic, so, if your router is in the cybercriminal range you could be a potential victim. The typical excuse “I am nobody” is not valid. You only need to be on the range – it doesn’t need to be an personal attack. The greater the number of potential victims greater the percentage of success.
To recollect all this events and cyberattacks, I usually use a sensor to redirect all the traffic that goes to my public IP that corresponds to my own router. I monitor all incoming activity in TCP and UDP range. I also monitor ICMP packets. I consider as suspicious every traffic addressed to my IP and I follow any attempt of connection to my TCP port.
Keep in mind that an IP address of a possible attacker by itself is not a relevant fact, since you can use different techniques to hide the real IP source or even the attacker can use a device already breached for his attack through him. At no time did I spread my IP address to receive attacks.
Data collection occurred between Wednesday, October 6 at 6PM and Thursday, October 24 at 6PM.
Once data collection time have finished, I present you the results:

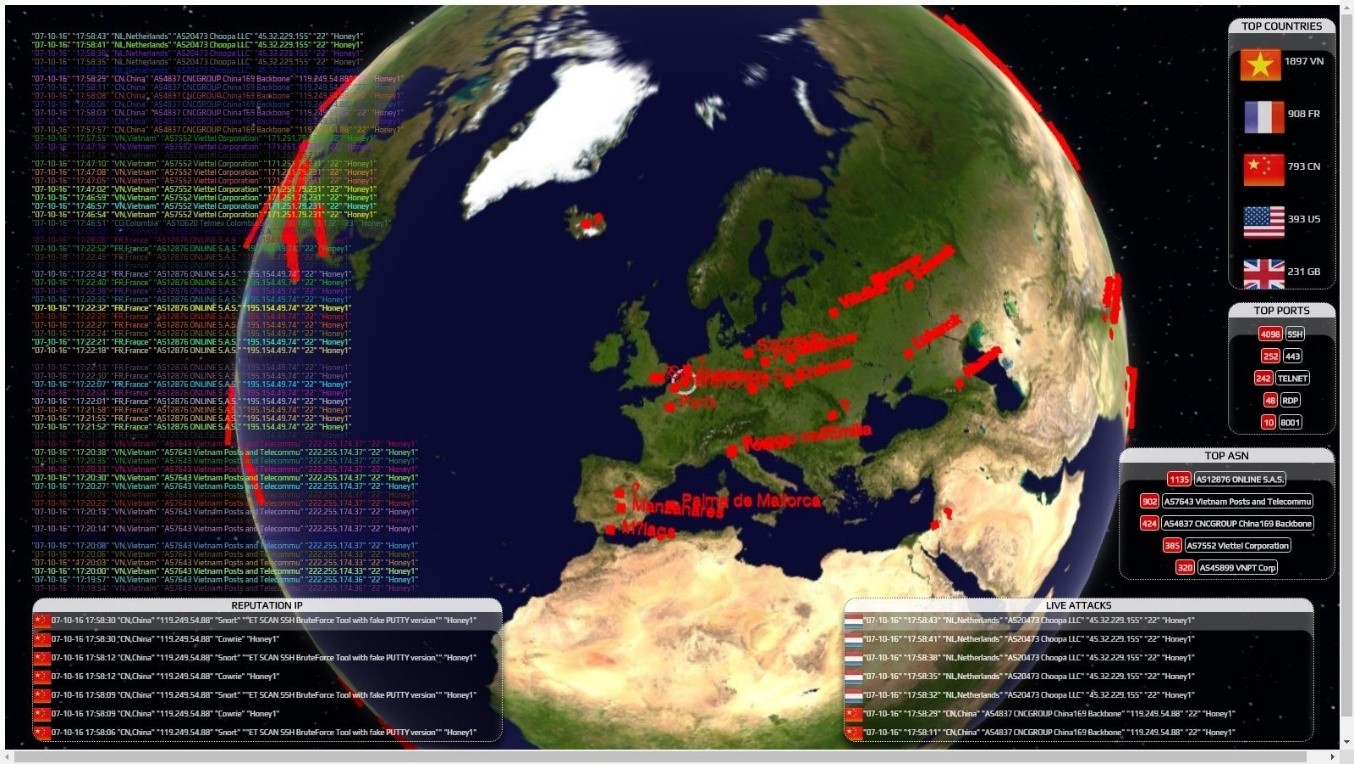
In 24 hours they produced a total of 20,070 events to my home router, which I consider as 4678 attacks. There has been a total of 92 different countries from which connections have received a total of 349 different ports.
More than half of the events were received from Asia. Among the ports that have received more connections, we highlight the SSH, Telnet, 443, 2323, RDP, VNC, 8080 among other services. If I ever have published that my services were exposed, we could ask ourselves what they are looking for and how they found me. We can know it if we perform an analysis of everything that has occurred.

Among the origins of events, it is normal lately find Vietnam on top. The answer to this can be found in details in the following article: https://securityaffairs.co/wordpress/52015/hacking/mirai-botnet.html
It happens due to a large number of infected IOT devices with MIRAI that have among their targets Spanish IP.


The graph above shows the traffic received from attacks (not all the events) during these 24 hours of analysis (Origin country, ASN, IP and port):

Some highlights countries by the number of attacks carried out (A, IP, and Port):



Most of the attacks have received European and Asian origin. We have also received a small share of attacks from Spain.


Analyzing some of the IPs that have attacked my router I could find the following web administration panels corresponding to cameras and routers:




Some of them do not need credentials for access and others have default credentials. They have visited my router (or perhaps any team behind that network), are connected to my decoy ports have downloaded malware samples have tried to include me in their botnet, they have used my gateway for attacks, including other activities.
There have been downloaded several samples of malware, including Mirai:

But it has not been the only malware that has tried to download. You can see below the demonstration of the large number of downloads using Wget that have attempted:
Once all the data were observed, you should ask yourself if your home router could be attacked or not. Don’t ask if it was attacked or not: ask when it will be. Thinking about the information presented in this article, maybe you are a little more aware that it will happen to you soon or later. I hope this time you have not your router exposed, have your credentials too weak and have exposed more information than necessary. Maybe you’ve already been attacked and still don’t know.
If you do not have these tips in mind, perhaps your IP address would appear on the next list.
Best regards.
These one and more articles are available at www.fwhibbit.es
My talk about honeypots:
Source:https://securityaffairs.co/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











