If you click on the gear button in Gmail and after you will see two modules there one with a name of ” Account and Import ” > ” Send Mail As ” and Forwarding Module was affected. This is a logical vulnerability which allowed me to hijack email addresses from Gmail. Any Gmail address which is associated or connected with Gmails SMTP was vulnerable to this security issue. It could be @gmail.com or @googlemail.com or @googleemail.com etc. We are aware of the fact that Gmail gives us report regarding the mail delivery if email was sent or not, Likely if we send email to any email addresses which dose not exist or is offline Gmail will bounce back a message with a subject of Delivery Status Notification which contains the reason why Gmail actually failed to deliver your email to the recipient.
- If recipients smtp is offline
- If recipient have deactivated his email
- If recipient dose not exist
- If recipient exists but have blocked us
- Cases could be even more
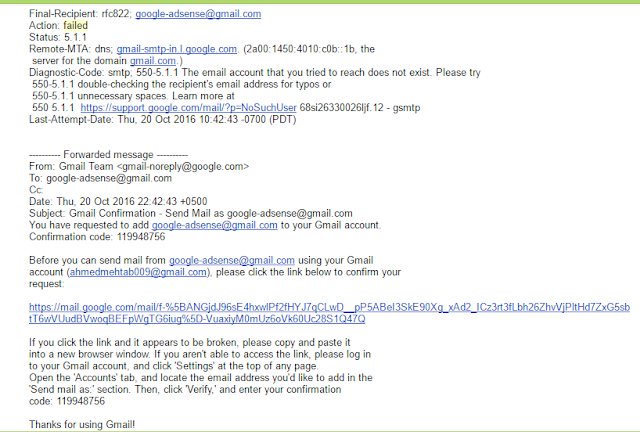
- Attacker try’s to confirm ownership of xyz@gmail.com
- Google sends email to xyz@gmail.com for confirmation
- xyz@gmail.com is not capable to receive email so email is bounced back to Google
- Google gives attacker a failure notification in his inbox with the verification code
- Attacker takes that verification code and confirms his ownership to xyz@gmail.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











