Brad Duncan, a security researcher for Rackspace, is well known for monitoring exploit kit activity and the payloads that are being distributed by them. In an article posted yesterday, Brad shows how the RIG-E (Empire) exploit kit has started to distribute a new ransomware called CHIP.
When a visitor browses to a site compromised with the RIG-E exploit kit, the injected script will try and exploit vulnerabilities in the visitors installed programs. If the kit can exploit a vulnerability it will download and install the payload, which in this case is the CHIP ransomware. This chain of events can be seen from in an image below from Brad’s article.

Source: https://www.malware-traffic-analysis.net/2016/11/17/index.html
According to a post on the BleepingComputer forums, each victim will download their own unique RSA-512 key from the ransomware’s command & control servers. This key will then be used to encrypt the AES encryption key used to encrypt the actual files. When a file is encrypted it will have the .CHIP extension appended to the file name. For example, when test.jpg is encrypted it would be renamed as test.jpg.chip.
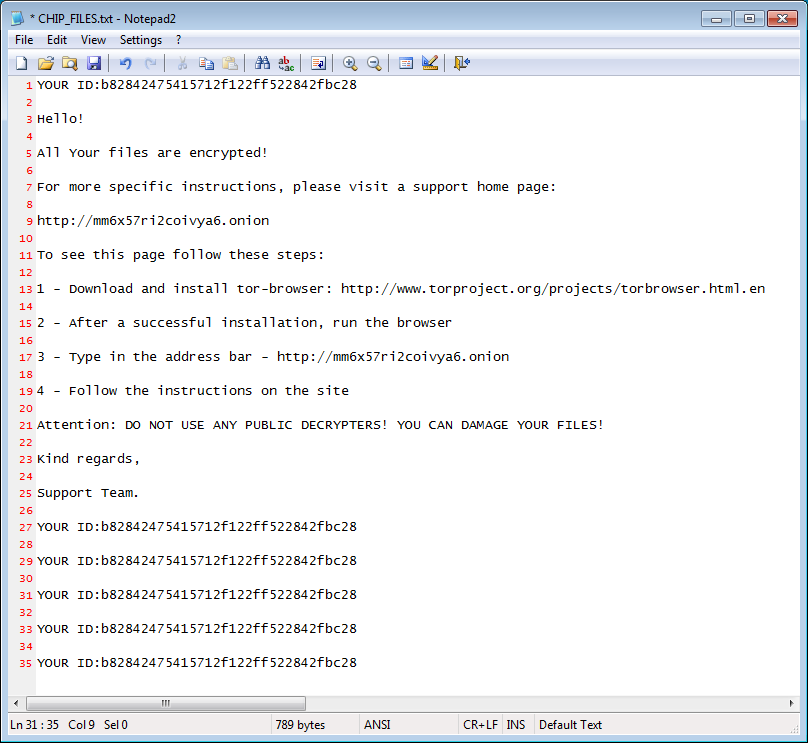
When the ransomware is done encrypting the files it will display a ransom note called CHIP_FILES.txt, which contains information such as the victim’s unique ID and instructions on connecting to the TOR Payment site for this ransomware.
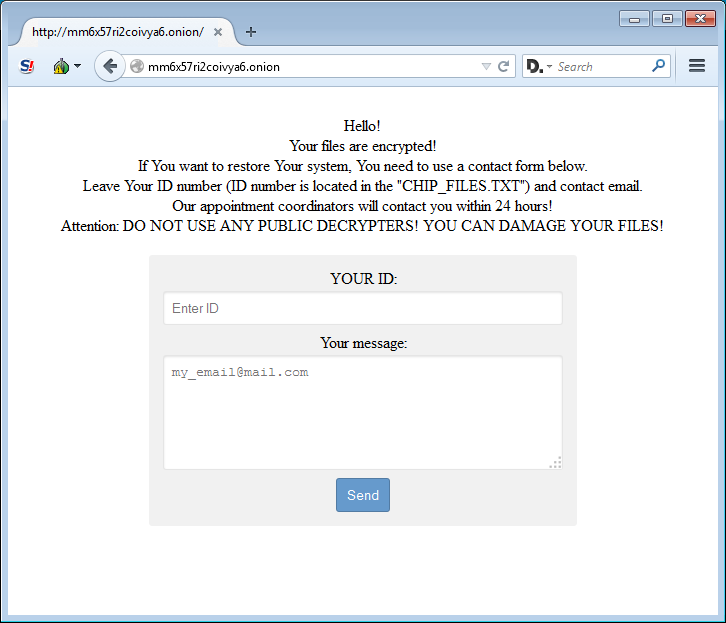
When the victim goes to the TOR payment site they will be prompted to leave enter their ID and a message in order to receive payment instructions.
At this time it is unknown how much they are asking for the ransom. As the victims are using unique RSA-512 encryption keys, though, it becomes highly unlikely to be able to decrypt this for free.
IOCs:
SHA256: aee03626b83a88b71b06899116cb7ce4b8092365103d69792b0c2d7153f24cb1Network Communication:
https://checkip.dyndns.org/
https://109.236.82.8/index.php
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











