A botnet of IoT (Internet of Things) devices created with the Linux/Moose malware is behind many bots that are plaguing social networks such as YouTube, Periscope, Twitter, and Instagram, above all.
Crooks are using this botnet of infected embedded devices to relay traffic they’ve sent from their command and control (C&C) servers to their targets, and are leveraging the infected device’s IP address to mask its real origin.
This traffic is related to social media fraud, an activity that describes the registration of fake accounts in order to boost the social media presence of other individuals. This usually involves adding fake followers to an account and giving fake “likes” to the content a person posts. Social media fraud is not illegal, per-se, but most social networks prohibit it.
Linux/Moose 2.0 resurfaces after one year
In 2015, security researchers from ESET discovered the Linux/Moose malware and the botnet behind it. ESET exposed the botnet’s social fraud activities, and soon after, the botnet died down, most likely shut down by its operators.
New research carried out by a team of Canadian researchers has revealed that the creators of the Linux/Moose malware have modified their code and made a comeback.
All changes are fairly superficial. Researchers say the modifications were added to make the botnet’s activity harder to detect, but its underlying modus operandi remained the same.
Linux/Moose targets Linux-based IoT devices
The Linux/Moose malware targets stripped-down Linux versions that operate on embedded systems running on the MIPS and ARM chip architectures. There is no support for Linux x86 systems, most likely to avoid detection by antivirus vendors, which have a strong presence on this platform.
The malware infects devices by accessing random IPv4 addresses, attempting to brute-force their Telnet port. Once it infects a device, it installs an SOCKS4 proxy and relays traffic it receives from its control server.
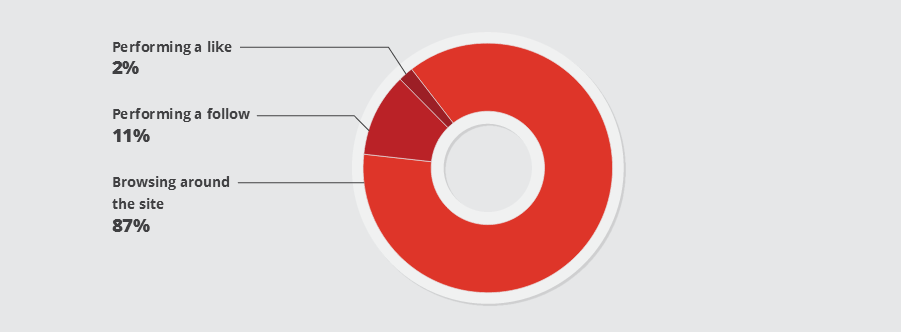
According to the team of researchers, the crooks use these bots to access various social media networks, create fake accounts, give likes, follow users or browse random content.
According to data gathered from several honeypots, browsing random content is the most common activity, but researchers say this is because the crooks are trying to make their bots appear as human and avoid spam filters.
The same honeypot data revealed that the operator behind the Linux/Moose botnet has conducted the most of his activity on Instagram.
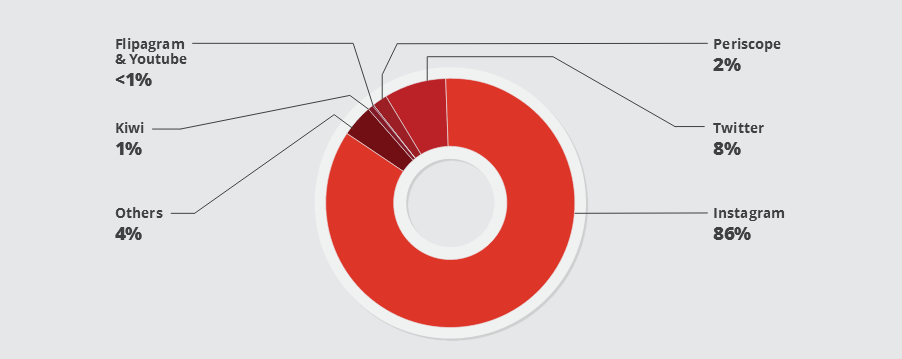
In a six-month period, researchers said that their honeypots picked up 1,732 fake Instagram accounts created via the Linux/Moose botnet. 72%, or 1,247 of these accounts, had been suspended by the end of the data gathering period, showing that most bots don’t survive indefinitely and Instagram’s support team catches the offenders.
Nevertheless, correlating data from the botnet’s activity and prices for Instagram likes and Instagram followers advertised online via various marketplaces, researchers created a simple graph through which they could estimate the botnet’s revenue, based on its potential size.
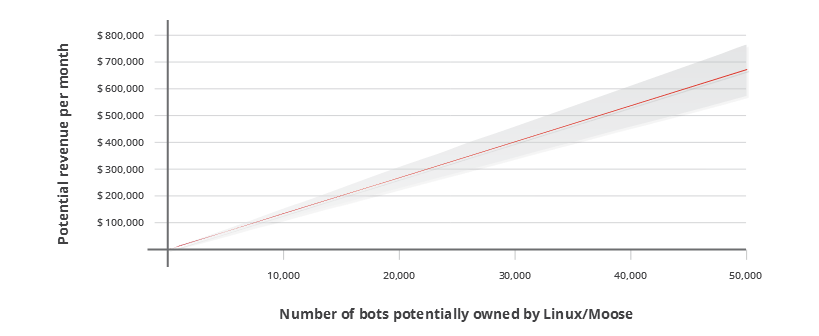
The estimated revenue is for $13.05 per bot per month, which makes this a very profitable operation, even more profitable than using the IoT botnet for DDoS attacks.
A benefit of using the Linux/Moose botnet for social fraud instead of DDoS attacks is that law enforcement isn’t generally interested in pursuing social media spam, compared to the effort they put in tracking someone that has shut down online businesses through destructive DDoS attacks.
Who buys Instagram followers?
Because their honeypot servers allowed the research team to sniff the botnet’s commands, researchers were also able to see what the bots were doing, allowing them to create a database of people that purchased fake social media followers and likes.
Researchers say that both businesses and individuals have bought followers and likes through the botnet, which was advertised online on the public Internet.
Magazines, clothes shops, car shops, food-related companies, interior design firms, makeup shops, electronic shops, and shoe shops made up the bulk of the “enterprise” clientele.
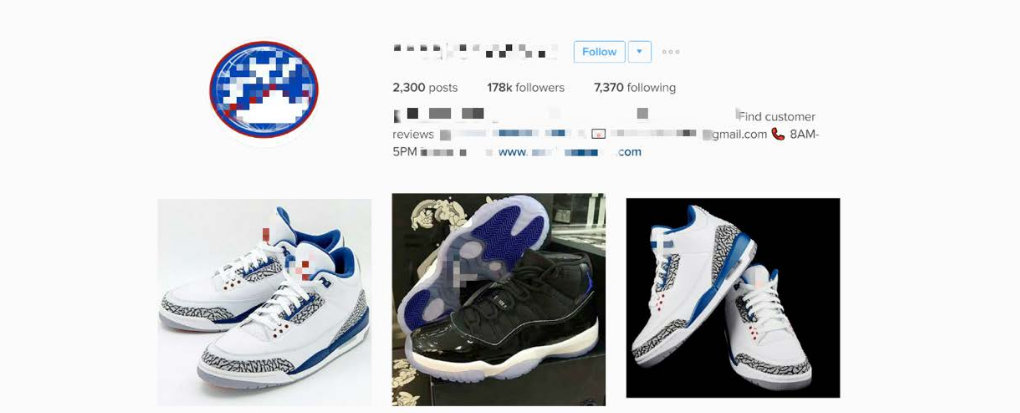
Among individuals, the customer list included web designers, tattooists, hairdressers, entrepreneurs, and photographers.
Furthermore, individuals not associated with a specific business also used the botnet. This includes models, singers, musicians, actors, bloggers, and TV personalities.
Researchers say that none of these people or businesses were “famous” and their actions of purchasing social media followers and likes seems to have been driven by their own ego, hence the research paper’s name of “EGO MARKET: When People’s Greed for Fame Benefits Large-Scale Botnets,” which was presented at this year’s Black Hat Europe security conference.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











