Will Dormann, a Vulnerability Analyst for the US-CERT Coordination Center (CERT/CC), is advising Microsoft to continue developing EMET because Windows 10 does not provide the same protection measures, in spite of the company’s claims.
EMET, which stands for Enhanced Mitigation Experience Toolkit, was launched in 2009 as a standalone application that users could install separately from Windows and bolster the defenses of their operating systems. Earlier this month, Microsoft announced that it moved the EMET End-of-Life date from January 27, 2017, to July 31, 2018.
In its announcement, the company alluded that Windows 10 is as secure as EMET, just because many of EMET’s features had been embedded in the operating system’s core.
Microsoft didn’t embed all of EMET’s features in Windows 10
Dormann disagrees with Microsoft’s statements. The security expert says that Microsoft did not integrate all of EMET’s protection features.
He goes on into detail and splits EMET’s protection features into two categories, System-Wide Protection and Application-Specific Protection, and explains that Microsoft only embedded a few of these in Windows 10, mostly at the OS core level.
The problem is that despite feature some of the EMET OS-level protection features, EMET is a fantastic security tool because of its multiple application-level defenses.
These application-specific EMET mitigations are applied as a runtime-injected library into the processes of other apps. Microsoft has not embedded all of EMET’s application-level defenses into Windows 10, as Dormann highlights via a simple table.
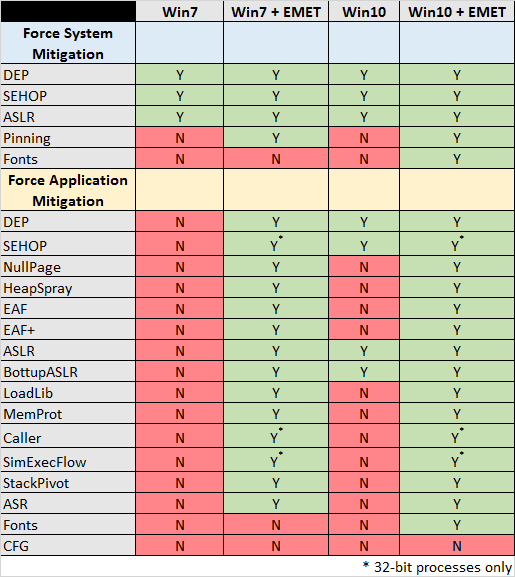
Dormann’s table shows that even an older Windows 7 OS with EMET installed is far better protected than an out-of-the-box Windows 10, which Microsoft claims is more secure.
EMET had another role
He also highlights another problem, and that’s the slow adoption of new technologies in user software.
“The problem is that the application needs to be specifically compiled to take advantage of CFG,” which is Control Flow Guard, one of EMET’s security features embedded in Windows 10.
“Out of all of the applications you run in your enterprise, do you know which ones are built with CFG support?” Dormann asks. “If an application is not built to use CFG, it doesn’t matter if your underlying operating system supports CFG or not.”
EMET’s role was to force these extra security features upon applications that didn’t have them or the developers didn’t bother taking advantage of them.
Companies and users should continue deploying EMET
Furthermore, the security experts recommend that companies continue to use and deploy EMET after the cut-off date.
“Just because Microsoft will stop supporting EMET after July 31, 2018 does not mean that the application will stop working beyond that date. It will likely continue to operate in the same way that it has been working all along. This EOL date simply means that you will not be able to get assistance from Microsoft after that date.”
Let’s just hope Microsoft decides to open-source the EMET code. There are some people interested in continuing its development.
Source:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.












