More details have surfaced regarding a recent wave of brute-force attacks (dictionary attacks to be more accurate) that have targeted WordPress sites over the past few weeks.
The attacks, first detected and described by WordPress security firm WordFence, targeted WordPress sites across the globe, but most of the malicious traffic originated from a limited set of IP addresses, assigned to an ISP in the Ukraine.
WordFence said that it detected over 1.65 million daily brute-force attempts from a small-time ISP identified only as “Pp Sks-lugan,” of which, over 1.5 million came from eight IP addresses, most likely under the control of one single person.
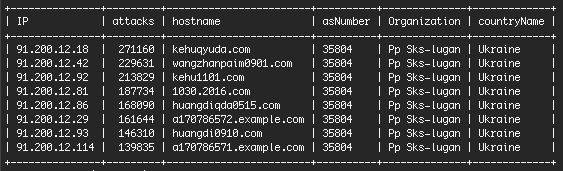
A few days later after WordFence made public their discovery, the company says that Ukrainian users have reached out and provided more information about the “naughty” ISP.
ISP located in the middle of the Ukraine civil war battlefield
A user by the name of Victor P. has tracked down the infringing ISP to a company named SKS-Lugan that existed for many years in the city of Alchevs’k.
According to a local business guide, the company’s CEO is a man named Lizenko Dmitro Igorovich, and SKS-Lugan has around 16 employees.
At the time of writing, Ukrainian authorities have no power over SKS-Lugan because the city of Alchevs’k is in an area controlled by pro-Russian forces in eastern Ukraine.
The city of Alchevs’k is right in the middle of the gray area created by the Ukrainian civil war.
![Ukraine conflict map [December 18, 2016]](https://www.bleepstatic.com/images/news/u/986406/attacks/WordPress/ukraine-map.png)
While Victor P. said the ISP is controlled “by Russia,” his remarks have no real evidence to suggest this is happening.
A more likely explanation is that the ISP’s owner(s), or whoever might be in charge at this time, has agreed to collaborate with cyber-crime syndicates and host servers that carry out malicious operations.
ISP’s IP addresses have been listed in spam block lists for years
In fact, the IP block assigned to the SKS-Lugan ISP has been involved in a large number of cyber-crime activities.
Currently, the ISP’s IP block list is featured in SBL (Spamhaus Block List), a large list that holds up-to-date information on IP addresses from where spam and other criminal activity originates.
The reasons why the IP block is listed is for “spammer & cybercriminal hosting (escalation)” and “ignoring reports, keeping spammers hosted for the money.”
According to the SBL page, some of these malicious operations have taken place even before the start of the Ukrainian war. It appears that the recently-discovered wave of brute-force attacks only shined a light on a long-lasting operation.
ISP has a long history of hosting cybercrime
According to the SBL, this is a small list of cyber-criminal activities hosted on the ISP’s IP block:
Neurevt infostealer botnet C&C server
Pony infostealer botnet C&C server
Tinba banking trojan botnet C&C server
Vawtrack banking trojan botnet C&C server
Smoke Loader botnet C&C server
FindPOS botnet C&C server
Madness botnet C&C server
Necurs botnet C&C server
Cutwail botnet C&C server
KINS botnet C&C server
Andromeda botnet C&C server
Vobfus worm botnet C&C server
Forum spam
Comment spam
Email spam
Carding sites
DDoS botnets
Illegal streaming sites
Are Russians controlling the ISP? … very unlikely!
While Russian President Vladimir Putin has acknowledged that Russian troops were on the ground in the Ukrainian war, it’s very unlikely that they’ve hijacked ISPs so they could brute-force WordPress sites.
Taking into account the ISP’s long history with cyber-criminal activities, it appears SKS-Lugan might be one of those bulletproof hosting companies that provide shelter for cyber-criminal operations.
The chaos created by the Ukrainian war most likely helped the ISP by thrusting it into the middle of a geographical zone where international law enforcement pacts don’t matter, and police forces can’t reach them.
There are no clues that the ISP might be tied to the recent Avalanche malware distribution network takedown by Europol and law enforcement agencies in various countries.
The Avalanche network had been created and coordinated by a Ukrainian man from the city of Poltava, Ukraine. Because authorities didn’t follow a proper legal procedure, a judge had to set the suspect free, who used this opportunity and fled.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











