The Merry X-Mas Ransomware is here and it’s not bringing you any presents. First discovered by @dvk01uk with the help of @Techhelplistcom, it is being named the Merry Christmas, or Merry X-Mas, Ransomware due to the title of the infection’s ransom note.
Victims who become infected with this ransomware will have their files encrypted and then be shown a ransom note that wishes them a Merry Christmas while demanding they pay a ransom to get their files back.
It is not Santa’s Elves distributing the Merry X-Mas Ransomware
The Merry X-Mas ransomware is currently being distributed through SPAM emails that pretend to be a consumer complaint from the Federal Trade Commission. These emails will state that the recipient’s company is violating the CCPA, or Consumer Credit Protection Act, and contains a link to the supposed document containing the complaint.
If recipients look closely, though, they will see that the email is coming from the domain ftc.gov.uk, which does not exist. The Federal Trade Commission is a USA agency and is not in the United Kingdom.
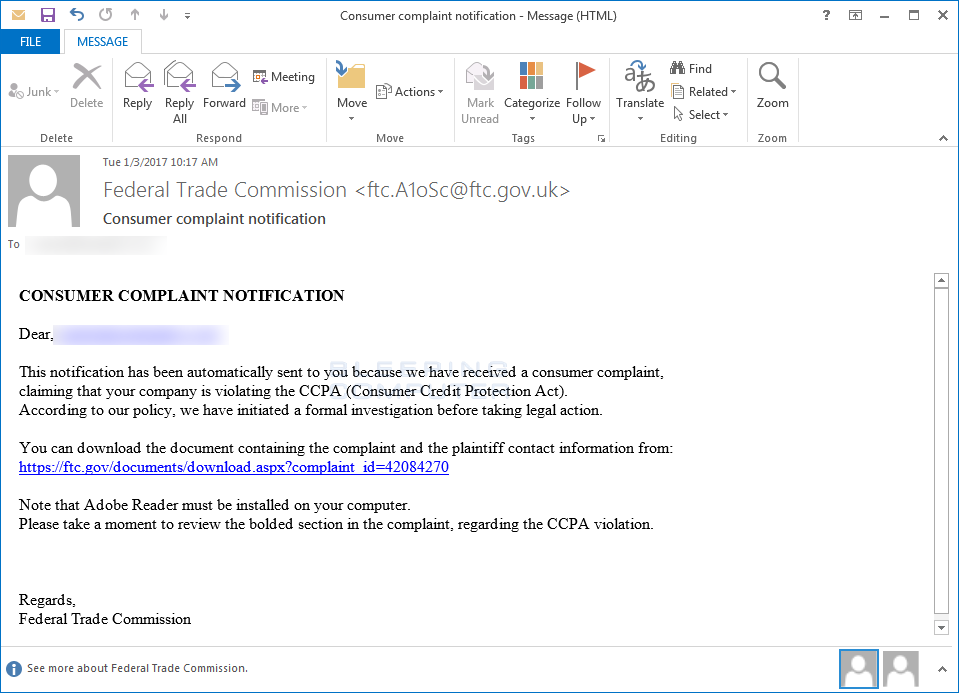
Though the supposed link to the complaint looks like the legitimate FTC web site, in reality it is a hidden link to a domain under the control of the malware developer called govapego.com.
When a recipient clicks on this link, it will download a zip file containing a file called complaint.pdf.exe. As Windows has extensions disabled by default, many recipients will instead see a document called COMPLAINT.pdf, as shown below, think it’s a legitimate PDF file, and therefore open it. Due to this, as part of our Ransomware Protection Guide, it is strongly suggested that you enable the viewing of Windows extensions.
Once the file is opened, the installer will silently sit in the background for a short period of time and then begin the encryption process.
How the Merry X-Mas Ransomware Encrypts a Computer’s Files
When the ransomware program is first executed, it will run in the background and remain idle for a short period of time. It will then connect to the URL https://onion1.host/cd/copy/gate.php and upload information about the victim’s computer. The information uploaded is the user name, computer name, running processes, installed programs, the local time, and various hardware information about the computer.
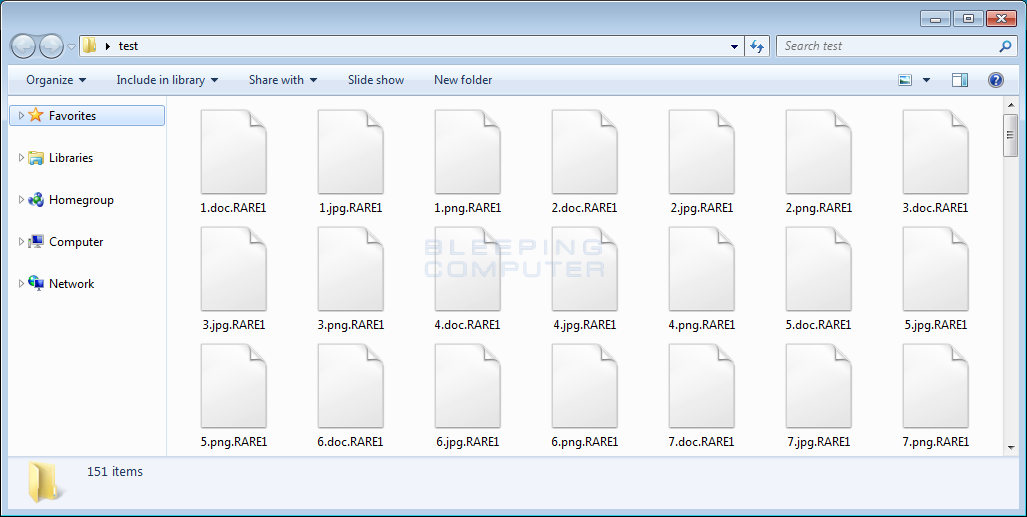
It will then scan the local drives on the computer and encrypt files that match certain targeted extensions, which were provided by Fabian Wosar of Emsisoft and listed at the end of this article. When a file is encrypted, the Merry X-Mas ransomware will add either the .PEGS1, .MRCR1, or .RARE1 extensions to the file name depending on the variant that is being installed. For example, for the the variant I tested, when a file named test.jpg is encrypted it would be renamed to test.jpg.RARE1.
In each folder that a file is encrypted, the ransomware will also create a ransom note named YOUR_FILES_ARE_DEAD.hta. This ransom note will be set as an autostart so it is opened every time the victim logs into Windows.
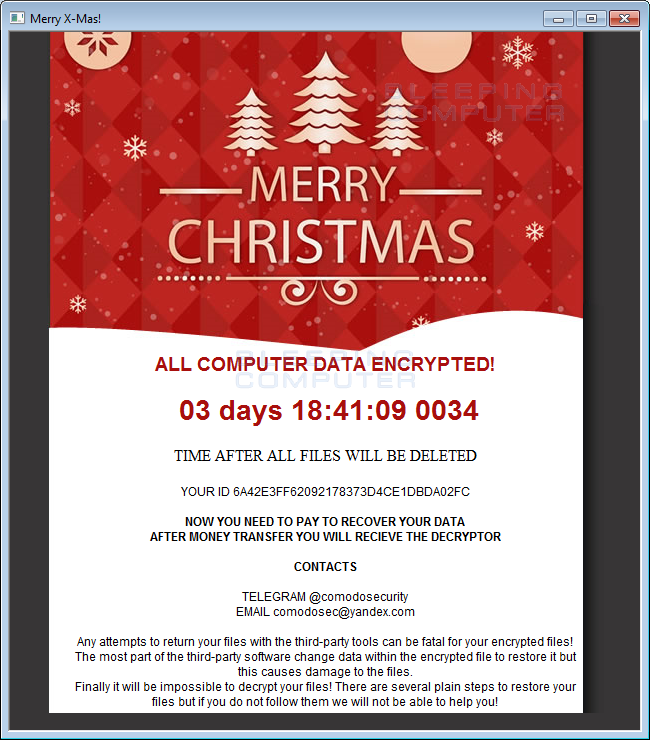
This ransom note contains instructions on how to contact the developer for payment information via email at comodosec@yandex.com or via Telegram at @comodosecurity. At this time it is unknown how much the developer is demanding as a ransom payment. At this time there is no way to decrypt files for free, but Fabian Wosar, a crypto superhero, is taking a look and hopefully a decryption method can be found.
Learn how to protect yourself from Ransomware
With the proper distribution and strong cryptology, a ransomware developer can generate a lot of revenue in a fairly short amount of time. Therefore, this highly lucrative computer infection is here to stay and people need to learn how to protect themselves.
To help with this, I have put together a Ransomware Protection Guide that provides many tips that a user should follow to protect themselves online.
Targeted File Extensions:
001, .1cd, .3d, .3d4, .3df8, .3dm, .3ds, .3fr, .3g2, .3ga, .3gp, .3gp2, .3mm, .3pr, .7z, .7zip, .8ba, .8bc, .8be, .8bf, .8bi8, .8bl, .8bs, .8bx, .8by, .8li, .a2c, .aa, .aa3, .aac, .aaf, .ab4, .abk, .abw, .ac2, .ac3, .accdb, .accde, .accdr, .accdt, .ace, .ach, .acr, .act, .adb, .ade, .adi, .adp, .adpb, .adr, .ads, .adt, .aep, .aepx, .aes, .aet, .afp, .agd1, .agdl, .ai, .aif, .aiff, .aim, .aip, .ais, .ait, .ak, .al, .allet, .alphacrypt, .amf, .amr, .amu, .amx, .amxx, .ans, .aoi, .ap, .ape, .api, .apj, .apk, .apnx, .app, .arc, .arch00, .ari, .arj, .aro, .arr, .arw, .as, .as3, .asa, .asc, .ascx, .ase, .asf, .ashx, .asm, .asmx, .asp, .aspx, .asr, .asset, .asx, .automaticdestinations-ms, .avi, .avs, .awg, .azf, .azs, .azw, .azw1, .azw3, .azw4, .b2a, .back, .backup, .backupdb, .bad, .bak, .bank, .bar, .bat, .bay, .bc6, .bc7, .bck, .bcp, .bdb, .bdp, .bdr, .bfa, .bgt, .bi8, .bib, .bic, .big, .bik, .bin, .bkf, .bkp, .bkup, .blend, .blob, .blp, .bmc, .bmf, .bml, .bmp, .boc, .bp2, .bp3, .bpk, .bpl, .bpw, .brd, .bsa, .bsk, .bsp, .btoa, .bvd, .bz2, .c, .cag, .cam, .camproj, .cap, .car, .cas, .cat, .cbf, .cbr, .cbz, .cc, .ccd, .ccf, .cch, .cd, .cdf, .cdi, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cef, .cer, .cert, .cfg, .cfm, .cfp, .cfr, .cgf, .cgi, .cgm, .cgp, .chk, .chml, .cib, .class, .clr, .cls, .clx, .cmd, .cmf, .cms, .cmt, .cnf, .cng, .cod, .col, .con, .conf, .config, .contact, .cp, .cpi, .cpio, .cpp, .cr2, .craw, .crd, .crt, .crw, .crwl, .crypt, .crypted, .cryptra, .cryptXXX, .cs, .csh, .csi, .csl, .cso, .csr, .css, .csv, .ctt, .cty, .cue, .cwf, .d3dbsp, .dac, .dal, .dap, .das, .dash, .dat, .database, .dayzprofile, .dazip, .db, .db_journal, .db0, .db3, .dba, .dbb, .dbf, .dbfv, .db-journal, .dbx, .dc2, .dc4, .dch, .dco, .dcp, .dcr, .dcs, .dcu, .ddc, .ddcx, .ddd, .ddoc, .ddrw, .dds, .default, .dem, .der, .des, .desc, .design, .desklink, .dev, .dex, .dfm, .dgc, .dic, .dif, .dii, .dim, .dime, .dip, .dir, .directory, .disc, .disk, .dit, .divx, .diz, .djv, .djvu, .dlc, .dmg, .dmp, .dng, .dob, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dox, .dpk, .dpl, .dpr, .drf, .drw, .dsk, .dsp, .dtd, .dvd, .dvi, .dvx, .dwg, .dxb, .dxe, .dxf, .dxg, .e4a, .edb, .efl, .efr, .efu, .efx, .eip, .elf, .emc, .emf, .eml, .enc, .enx, .epk, .eps, .epub, .eql, .erbsql, .erf, .err, .esf, .esm, .euc, .evo, .ex, .exf, .exif, .f90, .faq, .fcd, .fdb, .fdr, .fds, .ff, .ffd, .fff, .fh, .fhd, .fla, .flac, .flf, .flp, .flv, .flvv, .for, .forge, .fos, .fpenc, .fpk, .fpp, .fpx, .frm, .fsh, .fss, .fxg, .gadget, .gam, .gbk, .gbr, .gdb, .ged, .gfe, .gfx, .gho, .gif, .gif,.bmp, .gpg, .gpx, .gray, .grey, .grf, .groups, .gry, .gthr, .gxk, .gz, .gzig, .gzip, .h, .h3m, .h4r, .hbk, .hbx, .hdd, .hex, .hkdb, .hkx, .hplg, .hpp, .hqx, .htm, .html, .htpasswd, .hvpl, .hwp, .ibank, .ibd, .ibooks, .ibz, .ico, .icxs, .idl, .idml, .idx, .ie5, .ie6, .ie7, .ie8, .ie9, .iff, .iif, .iiq, .img, .incpas, .indb, .indd, .indl, .indt, .ink, .inx, .ipa, .iso, .isu, .isz, .itdb, .itl, .itm, .iwd, .iwi, .jac, .jar, .jav, .java, .jbc, .jc, .jfif, .jge, .jgz, .jif, .jiff, .jks, .jnt, .jpc, .jpe, .jpeg, .jpf, .jpg, .jpw, .js, .json, .jsp, .just, .k25, .kc2, .kdb, .kdbx, .kdc, .kde, .key, .kf, .klq, .kml, .kmz, .kpdx, .kwd, .kwm, .laccdb, .lastlogin, .lay, .lay6, .layout, .lbf, .lbi, .lcd, .lcf, .lcn, .ldb, .ldf, .lgp, .lib, .lit, .litemod, .lngttarch2, .localstorage, .locky, .log, .lp2, .lpa, .lrf, .ltm, .ltr, .ltx, .lua, .lvivt, .lvl, .m, .m2, .m2ts, .m3u, .m3u8, .m4a, .m4p, .m4u, .m4v, .mag, .man, .map, .mapimail, .max, .mbox, .mbx, .mcd, .mcgame, .mcmeta, .mcrp, .md, .md0, .md1, .md2, .md3, .md5, .mdb, .mdbackup, .mdc, .mddata, .mdf, .mdl, .mdn, .mds, .mef, .menu, .meo, .mfd, .mfw, .mic, .mid, .mim, .mime, .mip, .mjd, .mkv, .mlb, .mlx, .mm6, .mm7, .mm8, .mme, .mml, .mmw, .mny, .mobi, .mod, .moneywell, .mos, .mov, .movie, .moz, .mp1, .mp2, .mp3, .mp4, .mp4v, .mpa, .mpe, .mpeg, .mpg, .mpq, .mpqge, .mpv2, .mrw, .mrwref, .ms11, .ms11(Securitycopy), .mse, .msg, .msi, .msp, .mts, .mui, .mxp, .myd, .myi, .nav, .ncd, .ncf, .nd, .ndd, .ndf, .nds, .nef, .nfo, .nk2, .nop, .note, .now, .nrg, .nri, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .ntl, .number, .nvram, .nwb, .nx1, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odi, .odm, .odp, .ods, .odt, .oft, .oga, .ogg, .oil, .opd, .opf, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .owl, .oxt, .p12, .p7b, .p7c, .pab, .pack, .pages, .pak, .paq, .pas, .pat, .pbf, .pbk, .pbp, .pbs, .pcd, .pct, .pcv, .pdb, .pdc, .pdd, .pdf, .pef, .pem, .pfx, .php, .pif, .pkb, .pkey, .pkh, .pkpass, .pl, .plb, .plc, .pli, .plugin, .plus_muhd, .pm, .pmd, .png, .po, .pot, .potm, .potx, .ppam, .ppd, .ppf, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prc, .prel, .prf, .priv, .privat, .props, .prproj, .prt, .ps, .psa, .psafe3, .psd, .psk, .pspimage, .pst, .psw6, .ptx, .pub, .puz, .pwf, .pwi, .pwm, .pxp, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qdf, .qed, .qel, .qic, .qif, .qpx, .qt, .qtq, .qtr, .r00, .r01, .r02, .r03, .r3d, .ra, .ra2, .raf, .ram, .rar, .rat, .raw, .rb, .rdb, .rdi, .re4, .res, .result, .rev, .rgn, .rgss3a, .rim, .rll, .rm, .rng, .rofl, .rpf, .rrt, .rsdf, .rsrc, .rss, .rsw, .rte, .rtf, .rts, .rtx, .rum, .run, .rv, .rvt, .rw2, .rwl, .rwz, .rzk, .rzx, .s3db, .sad, .saf, .safe, .sas7bdat, .sav, .save, .say, .sb, .sc2save, .sch, .scm, .scn, .scx, .sd0, .sd1, .sda, .sdb, .sdc, .sdf, .sdn, .sdo, .sds, .sdt, .search-ms, .sef, .sen, .ses, .sfs, .sfx, .sgz, .sh, .shar, .shr, .shw, .shy, .sid, .sidd, .sidn, .sie, .sis, .sitx, .sldm, .sldx, .slk, .slm, .sln, .slt, .sme, .snk, .snp, .snx, .so, .spd, .spr, .sql, .sqlite, .sqlite3, .sqlitedb, .sqllite, .sqx, .sr2, .srf, .srt, .srw, .ssa, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stm, .stt, .stw, .stx, .sud, .suf, .sum, .svg, .svi, .svr, .swd, .swf, .switch, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .syncdb, .t01, .t03, .t05, .t12, .t13, .tar, .tar.bz2, .tarbz2, .tax, .tax2013, .tax2014, .tbk, .tbz2, .tch, .tcx, .teslacrypt, .tex, .text, .tg, .tga, .tgz, .thm, .thmx, .tif, .tiff, .tlb, .tlg, .tlz, .tmp, .toast, .tor, .torrent, .tpu, .tpx, .trp, .ts, .tu, .tur, .txd, .txf, .txt, .uax, .udf, .uea, .umx, .unity3d, .unr, .unx, .uop, .uot, .upk, .upoi, .url, .usa, .usx, .ut2, .ut3, .utc, .utx, .uu, .uud, .uue, .uvx, .uxx, .val, .vault, .vb, .vbox, .vbs, .vc, .vcd, .vcf, .vcxpro, .vdf, .vdi, .vdo, .ver, .vfs0, .vhd, .vhdx, .vlc, .vlt, .vmdk, .vmf, .vmsd, .vmt, .vmx, .vmxf, .vob, .vp, .vpk, .vpp_pc, .vsi, .vtf, .w3g, .w3x, .wab, .wad, .wallet, .war, .wav, .wave, .waw, .wb2, .wbk, .wdgt, .wks, .wm, .wma, .wmd, .wmdb, .wmmp, .wmo, .wmv, .wmx, .wotreplay, .wow, .wpd, .wpe, .wpk, .wpl, .wps, .wsf, .wsh, .wtd, .wtf, .wvx, .x11, .x3f, .xcodeproj, .xf, .xhtml, .xis, .xl, .xla, .xlam, .xlc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlv, .xlw, .xlwx, .xml, .xpi, .xps, .xpt, .xqx, .xsl, .xtbl, .xvid, .xwd, .xxe, .xxx, .yab, .ycbcra, .yenc, .yml, .ync, .yps, .yuv, .z02, .z04, .zap, .zip, .zipx, .zoo, .zps, .ztmpFiles associated with the Merry X-Mas Ransomware:
YOUR_FILES_ARE_DEAD.hta
Complaint.pdf.exeRegistry Entries associated with the Merry X-Mas Ransomware:
https://HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Adobe2" = %UserProfile%\Desktop\YOUR_FILES_ARE_DEAD.HTAHashes associated with the Merry X-Mas Ransomware:
SHA-256: 75c82fd18fcf8a51bc1b32a89852d90978fa5e7a55281f42b0a1de98d14644fa
Network Communications:
81.4.123.67
https://govapego.com
https://onion1.host/cd/copy/gate.php
Email Address and Payment Contacts:
TELEGRAM: @comodosecurity
EMAIL: comodosec@yandex.com
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











