Researchers have discovered a Linux variant of the KillDisk ransomware, which itself is a new addition to the KillDisk disk wiper malware family, previously used only to sabotage companies by randomly deleting data and altering files.
The KillDisk ransomware that targets Linux computers was discovered by ESET a week after researchers from CyberX came across the first KillDisk versions that included ransomware features, but which only targeted Windows PCs.
Linux version fumbles the encryption key
According to the ESET researchers, the way the KillDisk ransomware version work on Windows and Linux is completely different, with the biggest issue being that on Linux, KillDisk doesn’t save the encryption key anywhere on disk or online.
Normally, this would mean that victims would never be able to recover files since the encryption key would be lost immediately after the encryption process ends.
The good news is that ESET researchers say they’ve uncovered a flaw in the Linux variant that permits them to recover the encrypted files. The same weakness does not exist in the version that targets Windows PCs.
KillDisk ransomware, Windows variant
The KillDisk ransomware variant that targets Windows machines worked by encrypting each file via an AES-256 key, and then encrypting the AES keys with a public RSA-1028 key.
A private RSA key stored on the crook’s server allowed attackers to decrypt the victim’s files, but only after victims paid a humongous ransom of 222 Bitcoin (~$215,000). A screenshot of the Windows version’s ransom screen is available below.
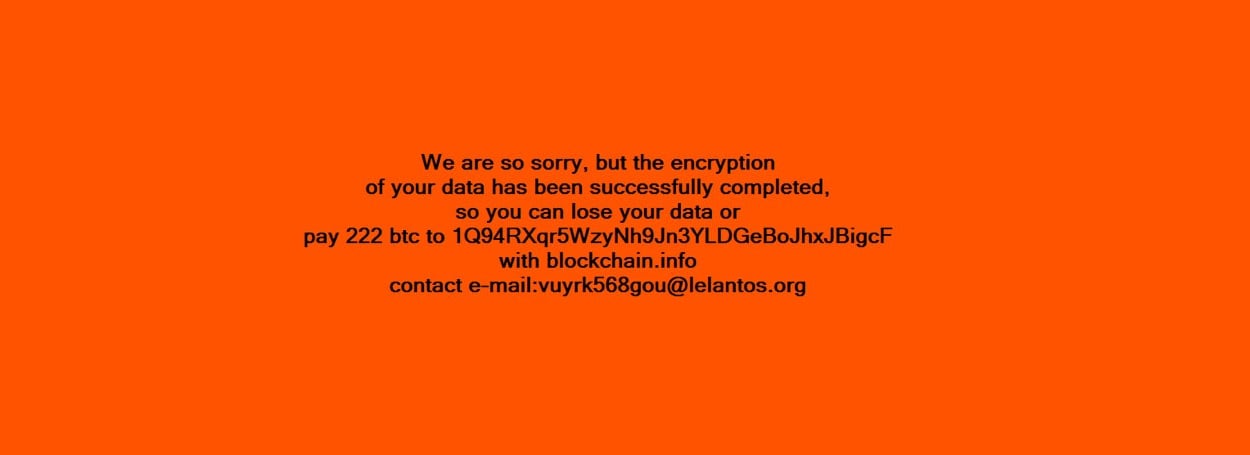
Crooks received the encryption keys on their servers via the Telegram protocol, used for the eponymous IM chat app. Because of this, CyberX named the operators of this ransomware campaign as the TeleBots group.
KillDisk ransomware, Linux variant
The Linux variant spotted by ESET researchers during the past week is very different from the Windows variant.
First and foremost, the Linux version does not talk to its C&C server via the Telegram API anymore. The encryption is also different.
According to researchers, the victim’s “files are encrypted using Triple-DES applied to 4096-byte file blocks,” and “each file is encrypted using a different set of 64-bit encryption keys.”
The Linux variant targets the following folders, at a depth of 17 subfolders, encrypting all files and appending the “DoN0t0uch7h!$CrYpteDfilE” termination.
/boot
/bin
/sbin
/lib/security
/lib64/security
/usr/local/etc
/etc
/mnt
/share
/media
/home
/usr
/tmp
/opt
/var
/rootThe KillDisk Linux ransomware will also rewrite the user’s boot sector and will use the GRUB bootloader to show its ransom screen.
The ransom note is word for word identical with the one shown in the Windows version, including the email address where victims can reach out to crooks.
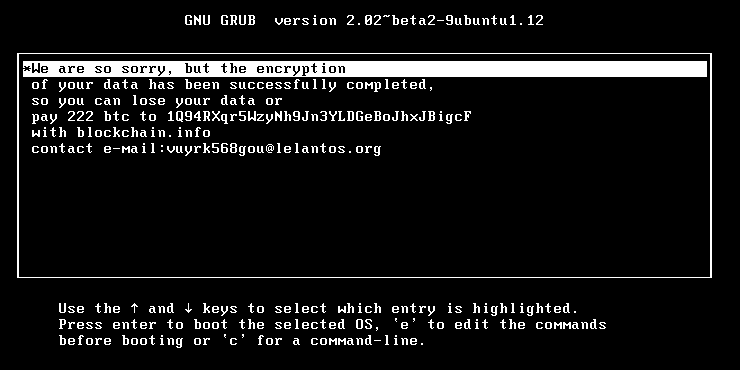
Before going the route of ransomware, KillDisk had been used solely in cyber-espionage and cyber-sabotage operations.
The most notorious attacks using KillDisk involved deleting system files, replacing data files, and rewriting file extensions.
In November 2015, KillDisk was used in attacks against a Ukrainian news media agency. In December 2015, KillDisk was used to sabotage Ukraine’s power grid. A cyber-espionage group known as BlackEnergy is suspected of being behind the attacks.
In December 2016, the TeleBots group used the KillDisk Windows ransomware to attack Ukrainian banks. At the time of writing, there is no evidence to link the TeleBots group with BlackEnergy.
Ransomware features used as a decoy?
In all attacks, BlackEnergy had used KillDisk to destroy computers and erase evidence of their attacks, perpetrated with other malware families.
The newly added ransomware features may be another way to mask their attacks, with companies thinking they might have been hit by ransomware, and not investigate the intrusions for other clues.
The ransomware’s huge ransom demand also plays in with this scenario as it’s absurd to think that a company might pay this much to recover their files.
The TeleBots gang may be hoping that companies give up on their files. By doing so, other signs and clues of the group’s intrusions would remain lost and encrypted forever.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











