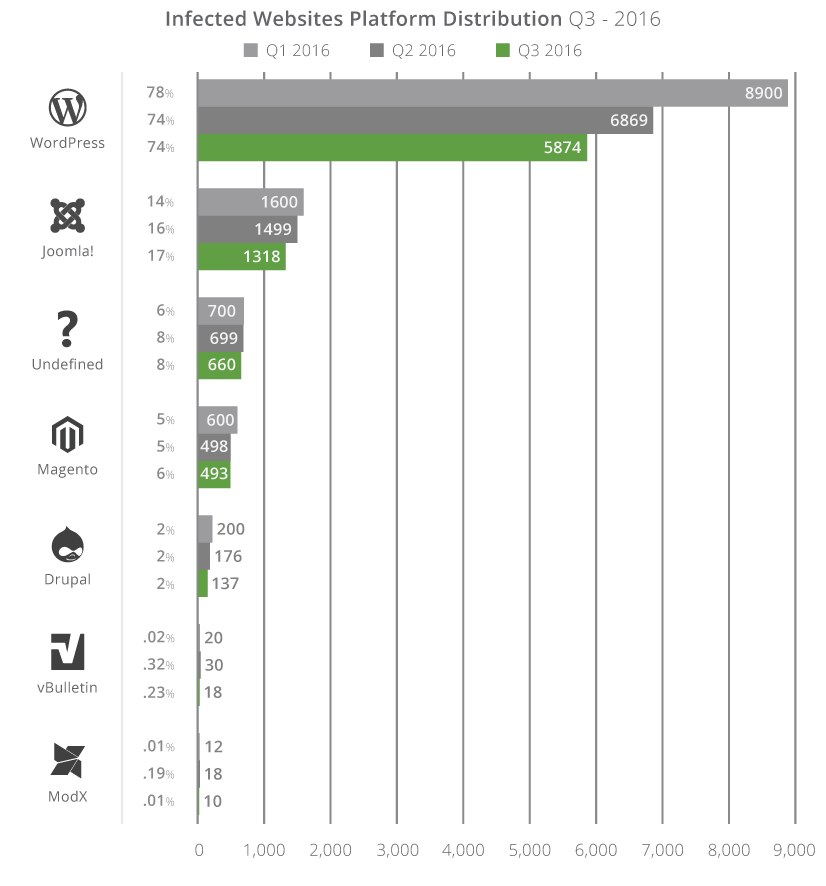
Based on statistical data gathered by Sucuri from 7,937 compromised websites, WordPress, Joomla, and Magento, in this order, continued to be the most hacked CMS platforms in the third quarter of 2016 (months of July, August, and September).
Among all hacked websites, 74% ran WordPress, which isn’t surprising if we take into account the CMS’ massive market share among today’s sites.
Just like for the rest of the year, Joomla with 17% and Magento with 6%, followed WordPress to make up the top three most hacked CMS platforms.
Other notable entries on this list included Drupal, vBulletin, and ModX, but incidents involving these platforms barely made up 2.25% of all security incidents, if putting together all their numbers.
This particular statistic doesn’t mean WordPress, Joomla, or Magento are insecure platforms, but only that webmasters make configuration errors that allow attackers to take control over their websites.
The graph above shows a decrease in the number of incidents compared to previous months, but this is due to a smaller sample size, and readers should only focus the percentage values showed on the left axis.
According to Sucuri, a large part of these hacks took place because webmasters failed to run up-to-date CMS versions.
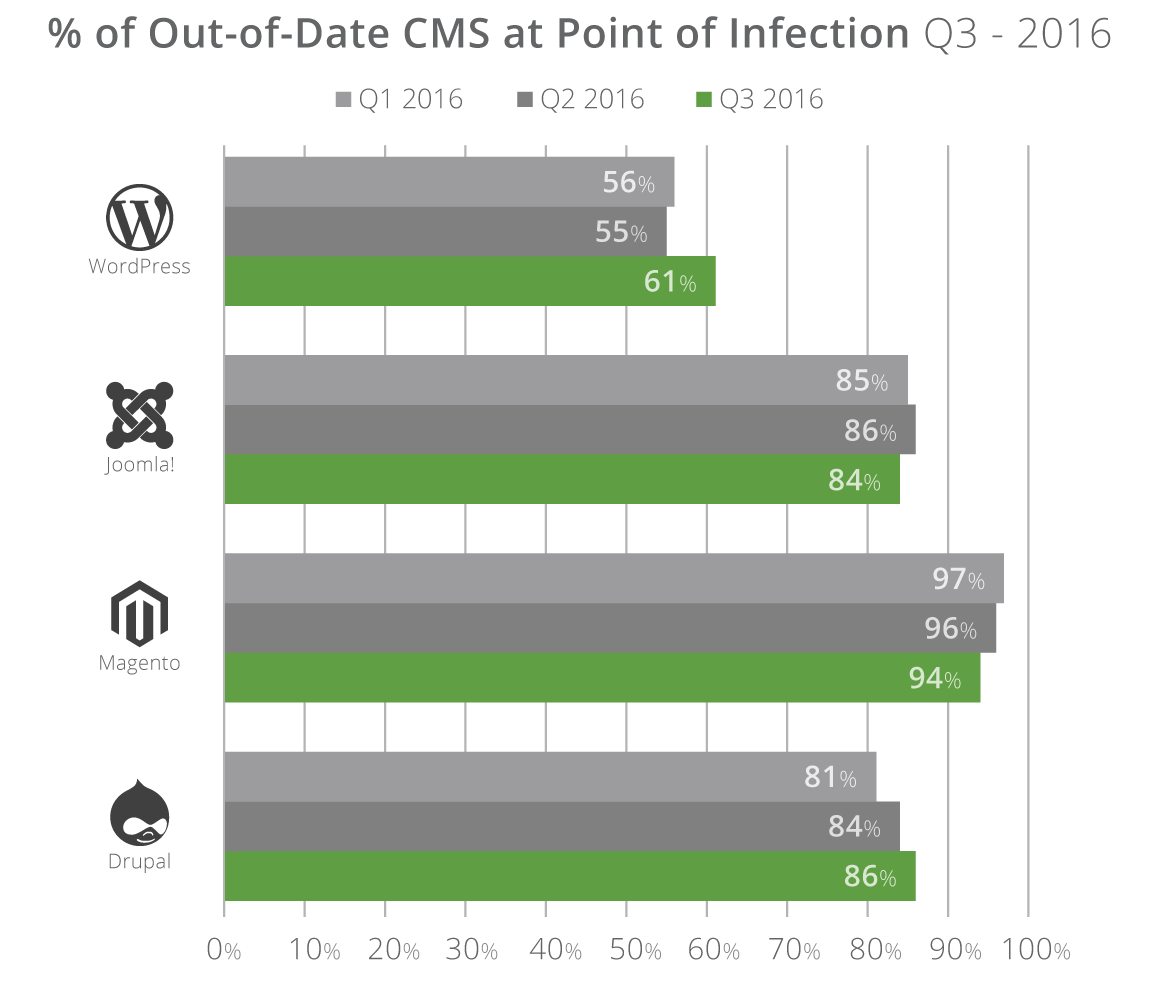
While outdated installations was a major source of problems for Joomla, Magento, and Drupal installations, the percentage was lower for WordPress, where only 61% of all hacked sites ran outdated WordPress installs.
Nevertheless, despite running up-to-date WordPress sites, Sucuri says webmasters failed to update plugins and themes, which eventually led to attackers finding an entry point they could exploit.
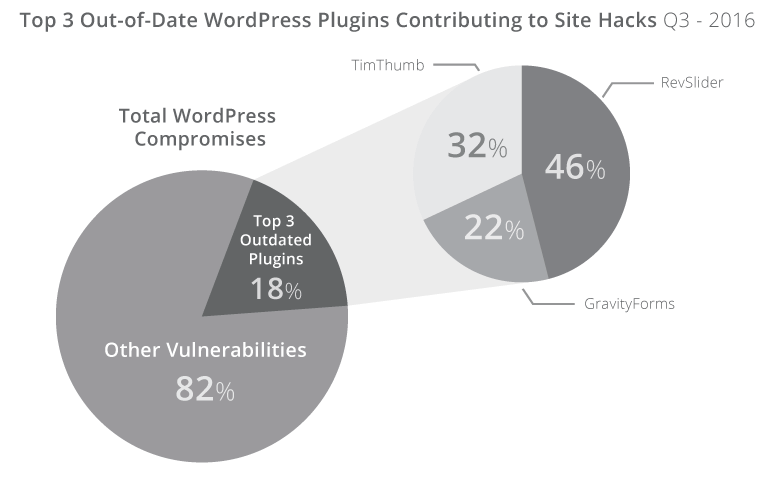
According to Sucuri, around 18% of all hacked WordPress sites can be attributed to websites running three out-of-date plugins: RevSlider, TimThumb, and GravityForms.
More interesting is that these plugins received updates a long time ago, but webmasters failed to protect their sites, with the most outrageous case being TimThumb, which received a security update in 2011, almost six years ago, but which site admins failed to install even now.
In most cases, the reason is that TimThumb has been used as part of other plugins and themes, and most websmasters didn’t even knew they’re site was vulnerable to begin with.
Cleaning up all these hacked websites is no small feat. According to Sucuri, an infection usually implies the contamination of 92 files on average.
Webmasters that remove a suspicious folder or a few files usually fail to remove the entire infection. According to Sucuri, on 72% of all hacked websites, attackers leave a backdoor behind. In these cases, neglecting to properly clean infected servers results in attackers regaining access shortly after.
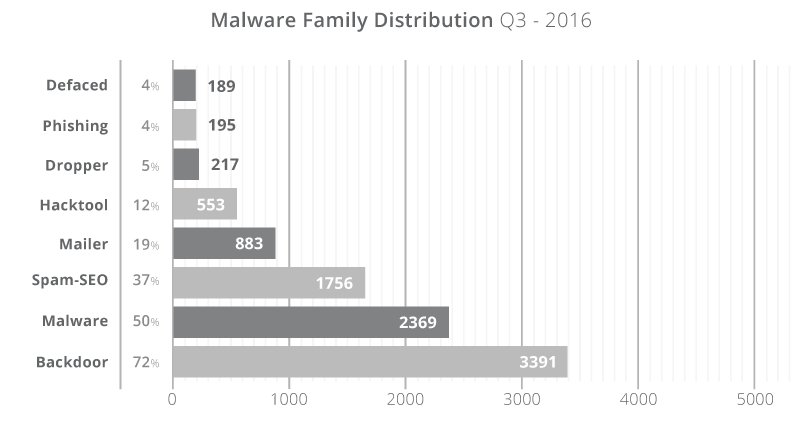
The direct result of these clean-up failures is that the website becomes a harbinger of malware, a participant in email spam campaigns, a pawn in black hat SEO schemes, or a participant in exploit kit operations.
But worse than all is that websites lose their search engine ranking. According to the same Sucuri report, around 15% of these hacked websites aren’t discovered in due time, and end up being blacklisted.
Removing a website from a blacklisting service, such as Google Safe Browsing, Norton SafeWeb, or McAfee SiteAdvisor, is not only extremely difficult and time-consuming but also damaging to a website’s reputation, which sometimes results in loss of revenue due to decreasing traffic.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











