A new ransomware family was snuffed in its crib today after security researchers tracked it down, analyzed its source code for weaknesses, and released a decrypter in less than 24 hours.
Discovered by MalwareHunterTeam, first signs of this threat appeared yesterday evening when a spam campaign started distributing Word files that would download and install the ransomware on users’ computers.
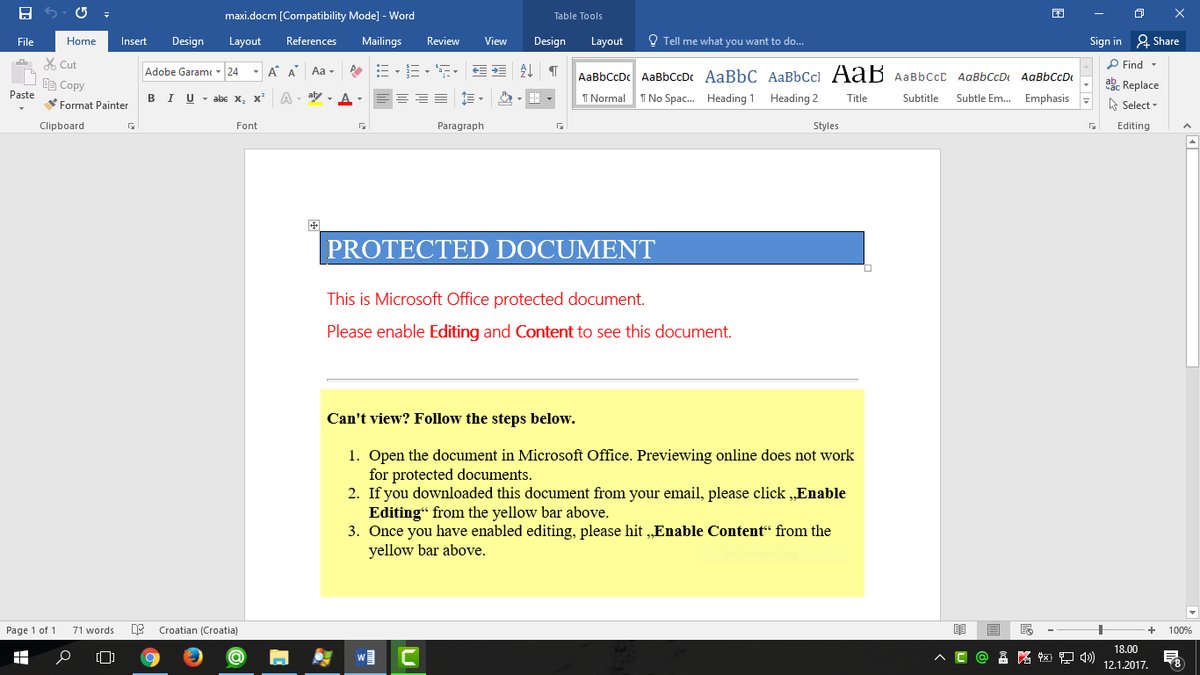
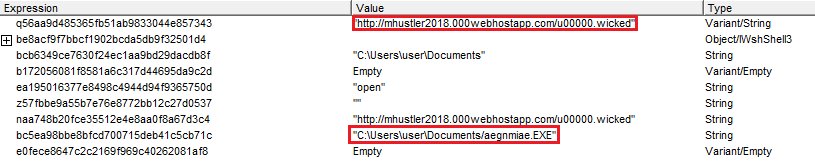
The ransomware, named Marlboro, comes with separate versions for 32-bit and 64-bit systems, which is the first time we’ve seen ransomware drop two separate installers depending on the target’s architecture. Other malware, such as backdoor trojans, banking trojans, or PoS malware employ this technique quite often.
Marlboro’s downloaders are fetched from free hosting accounts, which have been suspended in the meantime. Despite the usage of free hosting to store the Marlboro binaries, a researcher that wanted to remain anonymous said the “[spam] campaign was really well crafted,” as the threat actor appeared to have more knowledge of spam distribution methods rather than malware coding.
Ransomware uses simplistic encryption
Marlboro uses XOR encryption to encrypt the user’s files. All encrypted files will be renamed and will receive an extra “.oops” extension at the end. For example, a file named “image.png” will be renamed to “image.png.oops“.
After the encryption process ends, the ransomware will drop and open a ransom note on the user’s computer. This file is named “_HELP_Recover_Files_.html,” pictured below.

The ransom note alleges that the Marlboro ransomware uses a strong combination of AES and RSA encryption to unlock the user’s files. This is a lie.
The ransomware also drops a second file on the user’s desktop, which is a decrypter created by the Marlboro author himself. This file’s name is “deMarlboro,”, which also gives the ransomware’s name.
The decrypter works by checking the crook’s server for a ransom payment and then starting the decryption process. The decrypter also contains a human operator challenge to block users from spamming the author’s server with requests.
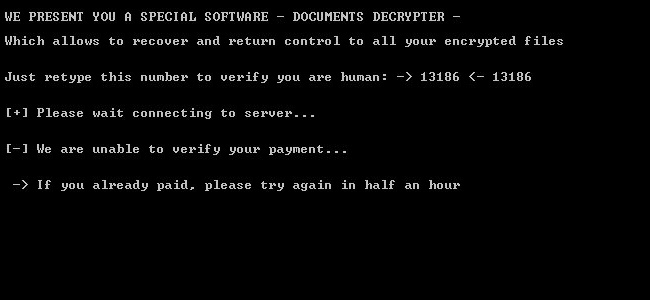
First victims appeared today when infected users started uploading their ransom notes and encrypted files on the ID-Ransomware service that helps users identify the ransomware that locked their files.
According to current statistics, only Serbian and Croatian users appear to have been targeted by Marlboro’s first wave.
Free Marlboro decrypter available
The good news is that security researchers quickly identified a problem with the ransomware’s encryption routine and created a free decrypter to help victims recover their files.
The decrypter, created by Emsisoft CTO and security researcher Fabian Wosar, is available via the Emsisoft website. Wosar was quick to identify several bugs in the ransomware’s mode of operation.
“Due to a bug in the malware’s code, the malware will truncate up to the last 7 bytes from files it encrypts,” the researcher said. “It is, unfortunately, impossible for the decrypter to reconstruct these bytes.” Nevertheless, for some files those bytes are insignificant and won’t mangle their content.
The overall quality of the Marlboro ransomware source code is low, according to both MalwareHunterTeam and Wosar. In fact, some of the ransomware’s inner guts appear to have been put together using code borrowed from StackOverflow’s C++ section.
IOCs
SHA256 Hashes
Word File: a2cf2ccc1d4a71ead386156b8c39a4f6240068cf9af485513284bf98662ae9b3
Downloader: a95d7606d17b221bca0960d04bffdc5ff1585ca13a2511bbf5347a732a3a025c
32-bit Binary: b5c37f3cf90026a815925aa4d53882823221c97127a378f0beb1b8276686caad
64-bit Binary: 1392f228397b8df531194c6c8945b83a02138e150a17483bb298c6168cbd50e9
Files targeted for encryption
.ARC,.DOC,.DOT,.MYD,.MYI,.NEF,.Ott,.PAQ,.PPT,.RTF,.SQLITE3,.SQLITEDB,.XLS,.aes,.asc,.asf,.asm,.asp,.aspx,.avi,.bak,.bat,.bmp,.brd,.bz2,.class,.cmd,.com,.cpp,.crt,.csr,.csv,.dat,.dbf,.dch,.dif,.dip,.djv,.djvu,.docb,.docm,.docx,.dotm,.dotx,.fla,.flv,.frm,.gif,.gpg,.hwp,.ibd,.jar,.java,.jpeg,.jpg,.key,.lay,.lay6,.ldf,.max,.mdb,.mdf,.mid,.mkv,.mml,.mov,.mp3,.mpeg,.mpg,.ms11,.not,.odb,.odg,.odp,.ods,.odt,.otg,.otp,.ots,.pas,.pdf,.pem,.php,.png,.pot,.potm,.potx,.ppam,.pps,.ppsm,.ppsx,.pptm,.pptx,.psd,.qcow2,.rar,.raw,.sch,.sldm,.sldx,.slk,.sql,.stc,.std,.sti,.stw,.svg,.swf,.sxc,.sxd,.sxi,.sxm,.sxw,.tar,.tar,.tbk,.tif,.tiff,.txt,.tz,.uop,.vbs,.vdi,.vmdk,.vmx,.vob,.wav,.wks,.wma,.wmv,.xlc,.xlm,.xlsb,.xlsm,.xlsx,.xlt,.xltm,.xltx,.xlw,.xml,.zipVerbatim ransom note
All of your files are encrypted with RSA-2048 and AES-128 ciphers.More information about RSA and AES can be found here:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with private key and decrypt program, which is on our secret server.
To receive your private key you need to make payment to us.
After you make payment run program called ‘DecryptFiles’ that is located on your Desktop and your Documents.
Program will automatically decrypt all of your files!
If you try to decrypt files with another software your files can be forever lost.
How to buy decrypter?
1. You can make a payment with BitCoins, there are many methods to get them.
2. You should register BitCoin Wallet
3. Purchase Bitcoins – Althought it is not very easy to buy bitcoins, it is getting simpler every day.
Here are our recommendations:
Localbitcoins.com (WU) – Buy Bitcoins with Western Union
Coincafe.com – Recommended for fast, simple service.
Localbitcoins.com Service allows you to search for people in your community willing to sell bitcoins to you directly.
CEX.IO – Buy Bitcoins with VISA/MASTERCARD or Wire Transfer
btcdirect.eu – THE BEST FOR EUROPE
4. Send 0.2 BTC to Bitcoin address:
5. After you make payment, run program called ‘DecryptFiles’that is located on your Desktop and your Documents.
Program will automatically decrypt all of your files!

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











