Security researchers have gained access to one of the servers used by the Cerber gang, from where they were able to extract basic statistics about their operation.
A security researcher that only goes by the nickname of Racco42 discovered the vulnerability on Thursday, January 12.
The issue affected only one Cerber server, not all, and was most likely due to a misconfiguration. The server wasn’t a command and control server, but a mere staging server from where the victims’ computers would connect and download the actual ransomware, which would later run and infect their PCs.
Server errors lets researchers in
An error in one of the server files (hxxp://truthforeyoue.top/search.php) displayed page source code, instead of executing it.
This information found its way to Avast security researcher Jaromir Horejsi, who together with the Avast team leveraged this error to get control over the server.
For a period of three hours, the Avast teams explains, they collected information from server logs.
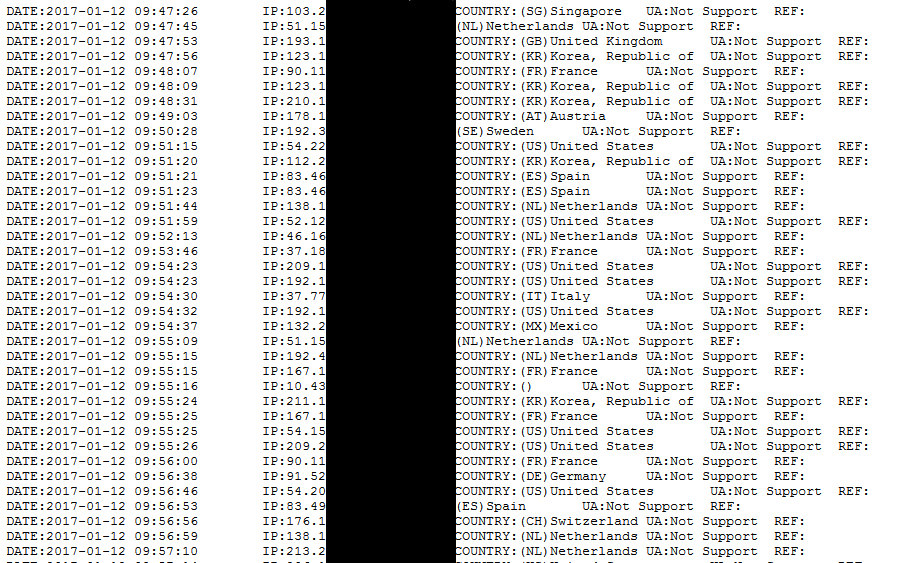
The Avast team observed over 700 victims download Cerber installers, which with no doubt encrypted their PCs.
Extrapolating this number to a whole day, just one typical Cerber ransomware staging server would be able to infect around 8,400 users during a spam run or malvertising campaigns.
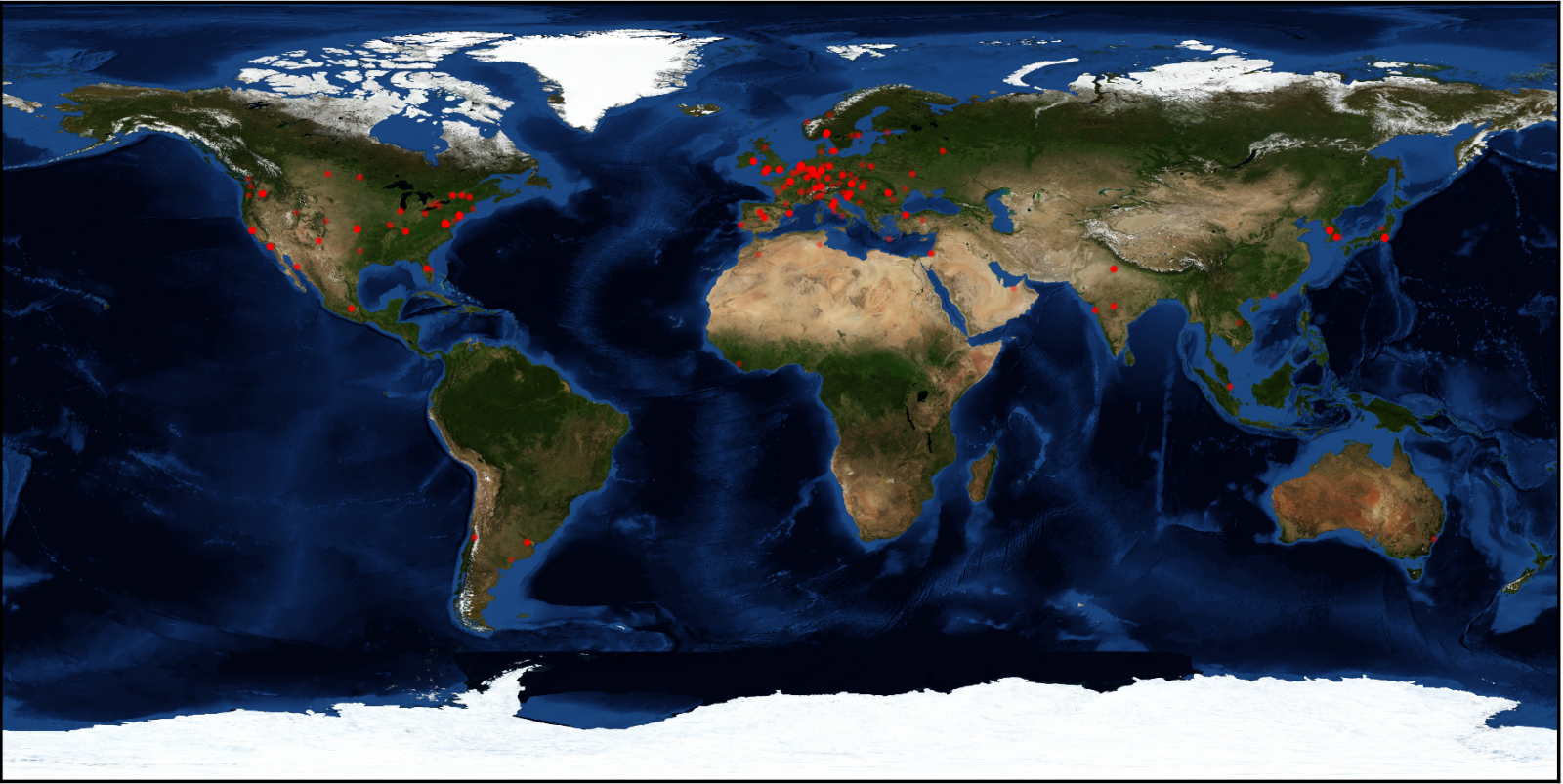
The data Avast researchers collected was plotted on a map which shows that most victims were located in Europe and North America.
This is not the first time security researchers hack their way into the servers of malware authors. Something similar happened in June 2016, when ISC Sans security researchers managed to gain access to a phishing server.
In the winter and spring of 2016, security researchers hacked their way into servers belonging to the Dridex gang and replaced payloads for the Locky ransomware with antivirus installers and sarcastic or offensive messages.
In one of those case, security firm Buguroo recovered data about victims infected with the Dridex banking trojan.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











