A new ransomware family is targeting Android devices, locking access to the screen, and constantly pestering the user to enter his payment card details.
According to Fortinet researcher Kai Lu, the one who discovered this new threat, the ransomware appears to be targeting only Russian-speaking users, as its ransom note is only available in Russian. A translated version of the ransom note is available below.
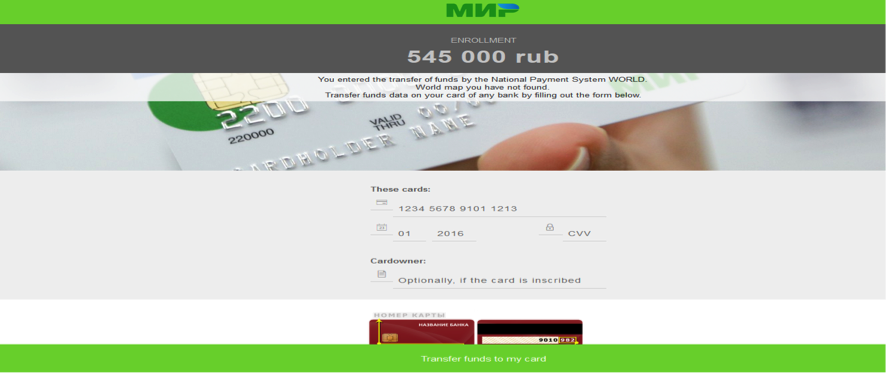
There are several things that stand out about this threat. The first is the humongous ransom demand it asks victims for, which is 545,000 Russian rubles (~$9,100).
This ransom demand is between 10 and 100 times over the price of some phones, and most users who can’t remove the screen locker will instead choose to buy a new phone rather than paying the crooks.
To pay the ransom, victims have to enter their credit card number directly in the ransom screen, a technique very different from how other ransomware operators like to work, which is via Bitcoin, Tor, or gift cards.
Ransomware abuses Google’s Cloud Messaging platform
The other thing that sets this ransomware apart is the usage of the Google Cloud Messaging (GCM) platform, now renamed in Firebase Cloud Messaging.
The GCM is a service offered by Google to Android app developers. It allows app creators access to a service that takes the load off their servers. A developer can send data from his server to the GCM, which then relays it to an app’s registered users. Vice versa, users can send data back to the developer’s server via the GCM.
Detected as Android/Locker.FK!tr, this ransomware uses the GCM in a similar manner, to take the load off its master command and control (C&C) server.
Infected phones contact the GCM platform, where they register and receive an ID, which they pass on directly to the ransomware C&C server. When the crook wants to issue commands to his victims, he simply relays instructions via the GCM platform, who uses PUSH notifications to tell infected phone(s) what actions to take.
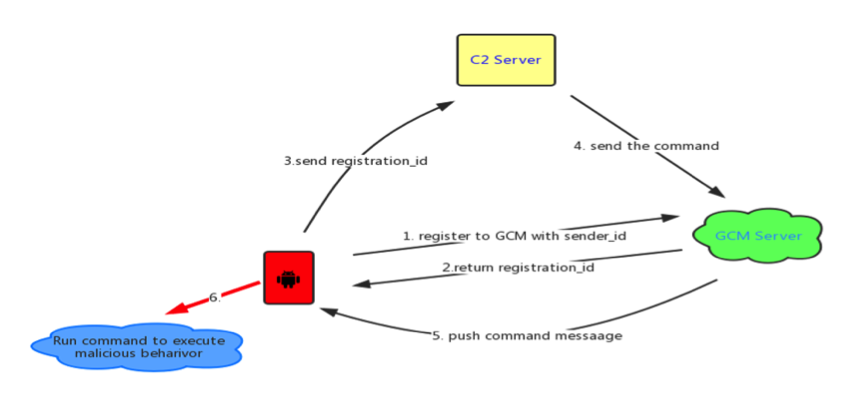
According to Lu, crooks can send 20 types of commands to infected hosts, commands which can lock or unlock the device’s screen, add new contacts to the phone, steal all contacts, send SMS messages, and update the malware’s code.
As mentioned before, this ransomware is currently targeting only Russian users. Just like most Android malware today, this threat is hidden inside an app that requests users to give it administrator rights.
The app is most likely downloaded and installed from third-party app stores. Because the ransomware gets admin rights, users have to reboot their devices in safe mode and remove the app from there.
In the fall of 2016, security researchers from Intel’s McAfee division discovered an Android banking trojan that besides asking victims for their payment card number, it also asked them to take a selfie with their ID card.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











