Downloading and trying to open Windows DRM-protected files can deanonymize Tor Browser users and reveal their real IP addresses, security researchers from Hacker House have warned.
Attacks using DRM-protected multimedia files in Windows have been known since 2005, but until recently, they’ve only been used to spread malware.
Past attacks tried to lure users into opening and playing DRM-protected files. In default scenarios, these files would open in the Windows Media Player, and users would see a popup that asked them to visit a URL to validate the file’s license.
Users who agreed were redirected to an “authorization URL.” Unknown to users is that malware authors could modify these links and point users to exploit kits or malware-laced files.
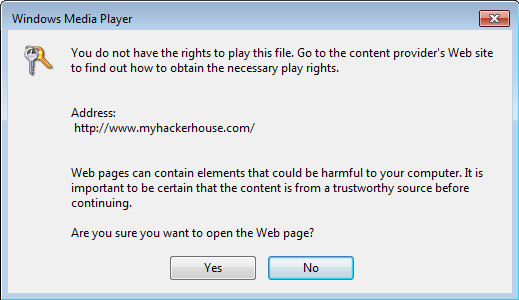
Hacker House researchers found out that this popup asking users if they wanted to visit the authorization URL would only appear for DRM files that have not been signed with the proper tools.
If the attacker signed the DRM-protected multimedia files with official Microsoft SDKs such as Windows Media Encoder or Microsoft Expression Encoder, the popup would not show, and the user’s player would automatically open an Internet Explorer instance and access the authorization URL.
Deanonymization attack is expensive
Hacker House researchers say the cost of properly signing DRM multimedia files ranges around $10,000, a sum that many low-end malware authors aren’t willing to pay for such a niche attack.
Nonetheless, the same is not true for determined state-sponsored attackers or law enforcement agencies, who have the financial and physical resources to support such an attack infrastructure.
For example, law enforcement could host properly signed DRM-protected files on sites pretending to host child pornography. When a user would try to view the file, the DRM multimedia file would use Internet Explorer to ping a server belonging to the law enforcement agency.
The same tactic can also be used to target ISIS militants trying to view propaganda videos, illegal drug and weapons buyers trying to view video product demos, political dissidents viewing news videos, and more.
A video showcasing the deanonymization attack is available below, courtesy of Hacker House researchers.
Sourcr:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











