Online tracking gets more accurate and harder to evade. Researchers have recently developed the first reliable technique for websites to track visitors even when they use two or more different browsers. This shatters a key defense against sites that identify visitors based on the digital fingerprint their browsers leave behind.
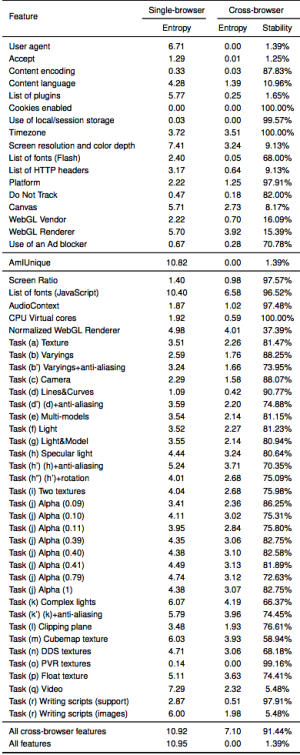
State-of-the-art fingerprinting techniques are highly effective at identifying users when they use browsers with default or commonly used settings. For instance, the Electronic Frontier Foundation’s privacy tool, known as Panopticlick, found that only one in about 77,691 browsers had the same characteristics as the one commonly used by this reporter. Such fingerprints are the result of specific settings and customizations found in a specific browser installation, including the list of plugins, the selected time zone, whether a “do not track” option is turned on, and whether an adblocker is being used.
Until now, however, the tracking has been limited to a single browser. This constraint made it infeasible to tie, say, the fingerprint left behind by a Firefox browser to the fingerprint from a Chrome or Edge installation running on the same machine. The new technique—outlined in a research paper titled (Cross-)Browser Fingerprinting via OS and Hardware Level Features—not only works across multiple browsers. It’s also more accurate than previous single-browser fingerprinting.
Fingerprinting isn’t automatically bad and, in some cases, offers potential benefits to end users. Banks, for instance, can use it to know that a person logging into an online account isn’t using the computer that has been used on every previous visit. Based on that observation, the bank could check with the account holder by phone to make sure the login was legitimate. But fingerprinting also carries sobering privacy concerns.
“From the negative perspective, people can use our cross-browser tracking to violate users’ privacy by providing customized ads,” Yinzhi Cao, the lead researcher who is an assistant professor in the Computer Science and Engineering Department at Lehigh University, told Ars. “Our work makes the scenario even worse, because after the user switches browsers, the ads company can still recognize the user. In order to defeat the privacy violation, we believe that we need to know our enemy well.”
The new technique relies on code that instructs browsers to perform a variety of tasks. Those tasks, in turn, draw on operating-system and hardware resources—including graphics cards, multiple CPU cores, audio cards, and installed fonts—that are slightly different for each computer. For instance, the cross-browser fingerprinting carries out 20 carefully selected tasks that use the WebGL standard for rendering 3D graphics in browsers. In all, 36 new features work independent of a specific browser.
In the paper, the researchers write:
We propose a (cross-)browser fingerprinting based on many novel OS and hardware level features, e.g., these from graphics card, CPU, audio stack, and installed writing scripts. Specifically, because many of such OS and hardware level functions are exposed to JavaScript via browser APIs, we can extract features when asking the browser to perform certain tasks through these APIs. The extracted features can be used for both single- and cross-browser fingerprinting.
Ninety-nine percent success rate
The new tracking technique relies on JavaScript code that’s compact enough to run quickly in the background while visitors are focused on a specific task, such as reading text or viewing video. The researchers have launched this website to demonstrate the techniques and have released the corresponding source code here. In a test that collected 3,615 fingerprints from 1,903 users over a three-month period, the technique was able to successfully identify 99.2 percent of users. By contrast, a single-browser fingerprinting technique dubbed AmIUnique, had a success rate of 90.8 percent.
Fortunately, cross-browser tracking doesn’t work against people using the default installation of the Tor browser. Still, many people tweak their installations of Tor so that it supports certain WebGL graphics capabilities required by gaming sites or other online destinations. While those tweaks may make the Tor browser more usable, they may also make it less immune to the fingerprinting techniques. Cao said he’s not aware of any sites using cross-browser fingerprinting.
Cross-browser fingerprinting is only the latest trick developers have come up to track people who visit their sites. Besides traditional single-browser fingerprinting, other tracking methods include monitoring the way visitors type passwords and other text and embedding inaudible sound in TV commercials or websites. The Tor browser without an attached microphone or speakers is probably the most effective means of protection, although the researchers said running a browser inside a virtual machine may also work.
“This approach is lightweight, but we need to find all possible fingerprintable places, such as canvas and audio context,” the researchers wrote of the potential virtualization defense. “If one place is missing, the browser can still be somehow fingerprinted. We leave it as our future work to explore the correct virtualization layer.”
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











