Islamic State supporters are being targeted with a modified version of the Telegram Android app that contains a version of the OmniRAT remote access toolkit.
The app, named plus_gram.apk, is spread via ISIS’ Telegram channels. Some Daesh members have detected the embedded malware and are now warning others.
Posts on underground ISIS forums detailing this new threat have been discovered by a security researcher who wanted to remain anonymous.
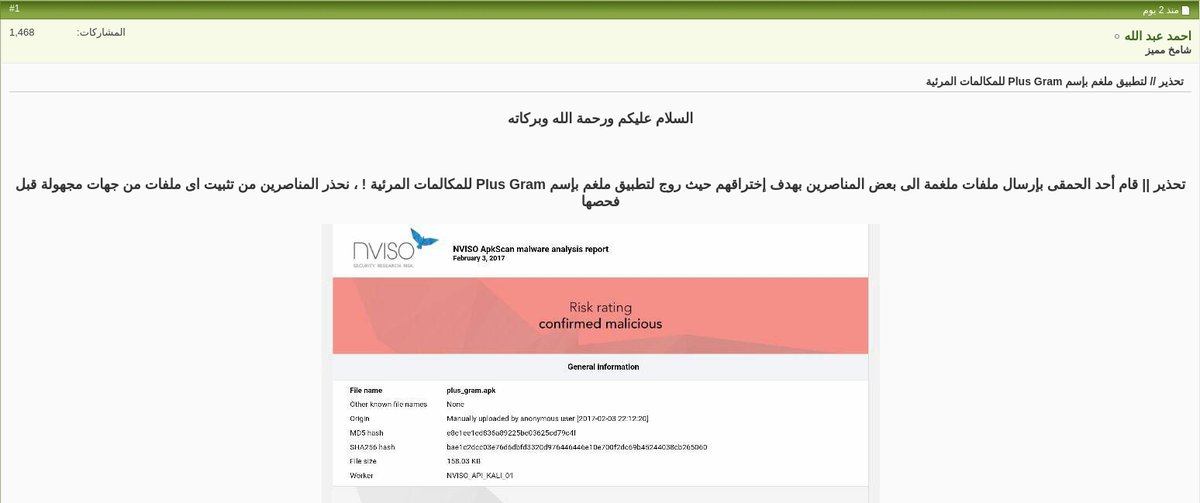
The forum post links to a Nvisio scan that classifies the plus_gram.apk package as “confirmed malicious.”
Security researcher FourOctets, who Bleeping Computer asked to take a look at the malicious app, was the one to spot the OmniRAT trojan.
OmniRAT is a commercially-available Remote Access Trojan (RAT) available online, with packages for infecting Android, Windows, Mac, and Linux systems, one of the few that can target so many operating systems.
According to the OmniRAT homepage, the Android version of this RAT can read and write phone logs, retrieve SMS messages, get GPS coordinates, silently install apps, access the microphone, access the camera, dump the phone’s memory, and more.
Amateurish attempt
According to both FourOctets and the anonymous researcher, whoever put together the plus_gram.apk app has no expertise in working with malware.
“They didn’t even try to hide what it was,” FourOctets said. “[OmniRAT] It’s still in the XML file.”
“I’m thinking it’s just old code repacked for Android, using a common vector,” the anonymous researcher also added. The researcher described the person put the malware together as “an amateur/hobbyist.”
Below is a video presentation of OmniRAT.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











