Today, we have released a white paper on RTM, a cybercrime group that has been relentlessly targeting businesses in Russia and neighboring countries using small, targeted campaigns. This group, active since at least 2015, is using malware, written in Delphi, to spy on its victims in a variety of ways, such as monitoring keystrokes and smart cards inserted into the system.
It has the ability to upload files from the compromised system to its command and control (C&C) server. It also has a fingerprinting module to find systems on which specialized accounting software is installed. In particular, they are looking for signs of popular accounting software called “1C: Enterprise 8”. This software is used by businesses, among other things, to make bulk transfers via Remote Banking Systems (RBSes).
While inspecting RTM bot’s network communications, we saw that they were requesting one specific file created by “1C: Enterprise 8”. This file, named “1c_to_kl.txt”, contains bulk transfer details and is used as an intermediary step in RBSes to execute payment orders. By altering this text file, the criminals can make monetary gains off it by, for example, modifying the recipient account details.
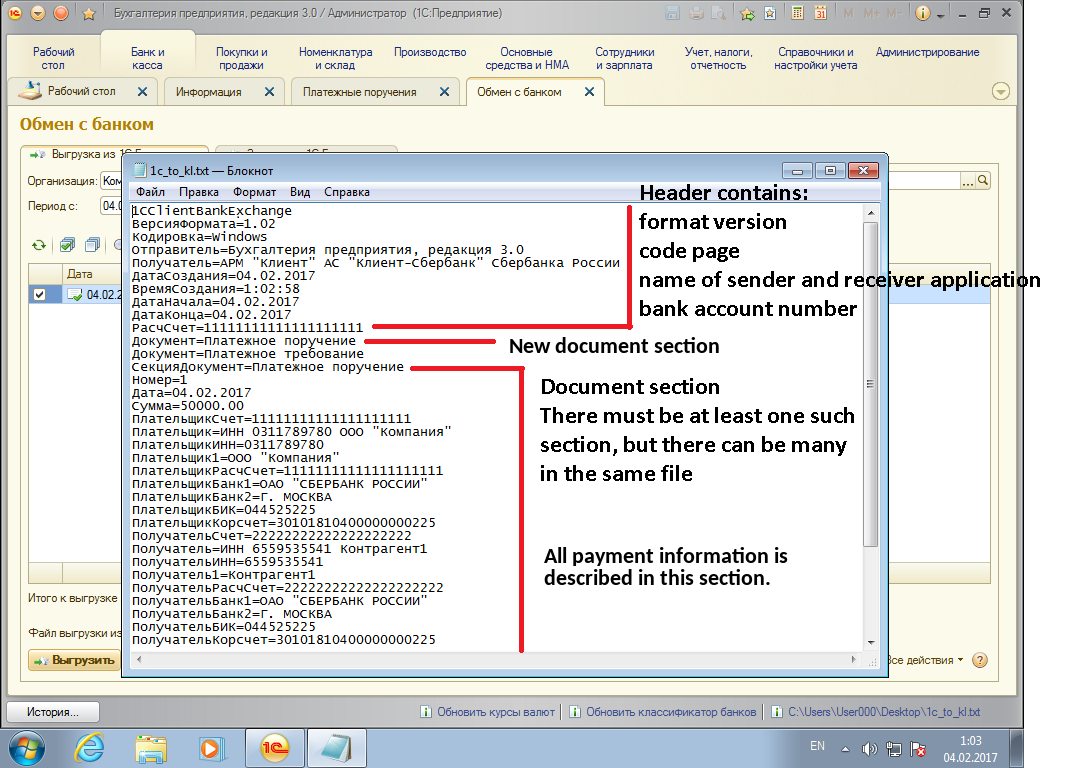
Example 1c_to_kl.txt export file
This problem was severe enough to warrant an advisory from FinCERT, the Russian CERT responsible for fighting cybercrime targeting Russian financial institutions. It warned potential victims in late 2016 that criminals were going after 1c_to_kl.txt export files. We know that this specific attack vector was also used by at least one other group: Buhtrap.
For a long time now, groups like Corkow and Buhtrap have been specifically targeting business RBS users. These groups use complex backdoors and custom tools to steal from their corporate victims. RTM is another manifestation of this trend, where specialized criminals are mounting targeted attacks against financial institutions’ clients to maximize their financial gains.
Lately, we have seen other groups using similar tactics targeting businesses in other parts of the world. In fact, last summer, MELANI, a Swiss reporting and analysis center for information assurance, issued a newsletter warning companies against hacker groups using the Dridex malware to target offline payment software. While we have not seen RTM activities outside of Russia and its neighbors, it would not come as a surprise to see them target other countries in the world.
Source:https://www.welivesecurity.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











