The SHA1 (Secure Hash Algorithm 1) cryptographic hash function is now officially dead and useless, after Google announced today the first ever successful collision attack.
SHA1 is a cryptographic hash function used generate hashes for digital data, hashes that, in theory, should be unique for each data blob, and used to sign and attest to a file’s authenticity and identity.
The SHA1 hashing function was designed by the United States National Security Agency (NSA) and its algorithm was first published in 1995.
The algorithm started showing its age in 2005 when cryptanalysts found theoretical flaws that could be used to break SHA1 via collision attacks, a term used to describe when a determined attacker generates a file that has the same SHA1 hash of another, legitimate file.
Collision attacks are very dangerous in real life, as they allow an attacker to replace files without raising any suspicions.
While cryptanalysts have recommended that companies move away from SHA1 to the newer SHA2 or SHA3 hashing functions, SHA1’s demise came in the autumn of 2015, when researchers from several universities across the world published a research paper named The SHAppening.
In this breakthrough research, scientists demonstrated that technological advances in computing power had accelerated SHA1’s lasting power, arguing that it would had taken between $75,000 and $120,000 to break SHA1 using Amazon’s EC2 service, a cost that some nation states could afford even right then.
Shortly after their research went public, browser vendors such as Mozilla, Microsoft, and Google started an accelerated process to replace SHA1 as the hashing function in TLS/SSL certificates, a plan which they are successfully carrying out, as we speak.
Google and Dutch scientists teamed up
Unknown to many was that Google had approached two of the researchers involved in The SHAppening and offered their help in continuing their work.
With Google’s immense computing power at their disposal, and with the help of five of Google’s top cryptographers, this seven-man team published today new research detailing a full SHA1 collision attack.
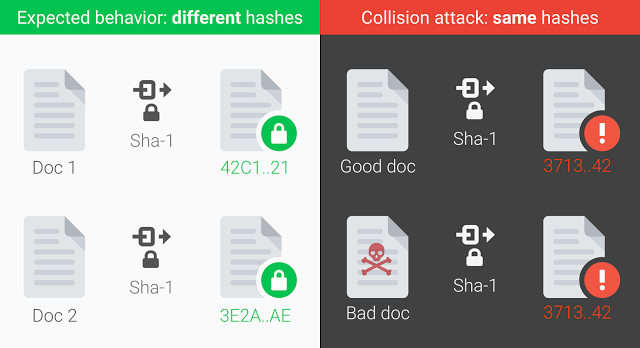
As proof of their work, they also released two different PDF files that feature the same SHA1 hash, which stands to serve as evidence for the first ever successful SHA1 collision.
To better understand their announcement and the consequences of an SHA1 collision attack in the real world, imagine you signed a contract, stored it online as a PDF, and used its SHA1 hash to authenticate that nobody tampered with the file.
Knowing now that SHA1 hashes could be faked, how would you tell if someone hasn’t replaced the original PDF contract with another one that has the same SHA1 hash, but completely different clauses?
Proof-of-concept code to be released in 90 days
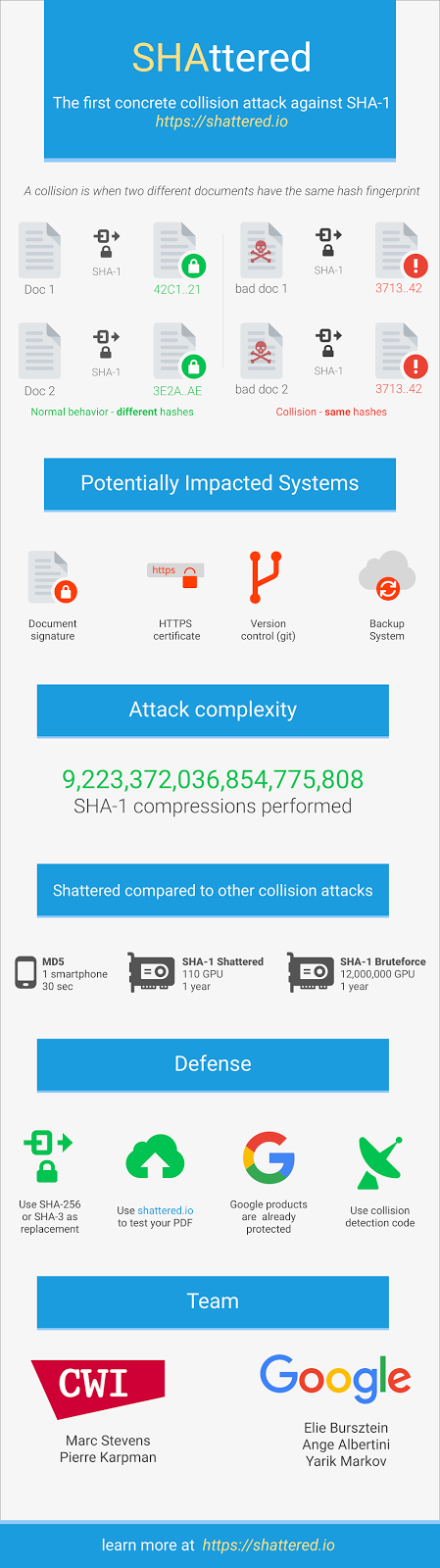
The only good news out of today’s announcement is that Google engineers described the SHA1 collision attack as “one of the largest computations ever completed,” meaning it won’t be financially possible to execute such attacks anytime soon.
Nevertheless, Google plans to release the proof-of-concept code that they used for the collision attack in 90 days, meaning companies that still rely on SHA1 have three months to replace it with something else.
With computing power becoming cheaper each month, and with PoC code publicly available, generating custom SHA1 hashes on a daily basis is just months/years away.
Google has released the two PDF files with the same SHA1 hash here and here, and the following infographic with more information on the attack. There’s also a dedicated website.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











